Automated Embedded Security for Safer, More Reliable Devices
- Gain complete visibility into software components with C/C++ build-time SBOMs
- Defend software at runtime with automated code protection
- Meet compliance requirements and improve business outcomes
$2.08M
Saved per year
Average savings customers realized
based on risk reduction.
50%
Increase
Average increase in automated
mitigation by customers.
90%
Reduction
70%
Coverage
“From our perspective, adding RunSafe means we have more opportunity to shrink the attack surface and reduce overall risks for our customers since security is now already built into our product.”
Donnie Sturgeon, Senior Director of Avocent Business and Product Development, Vertiv
Trusted By
See the Risks. Stop the Threats.
Protect Your Embedded Systems.

Addressing Vulnerabilities in Critical Infrastructure
RunSafe Identifies Risk Exposure and Protects Code
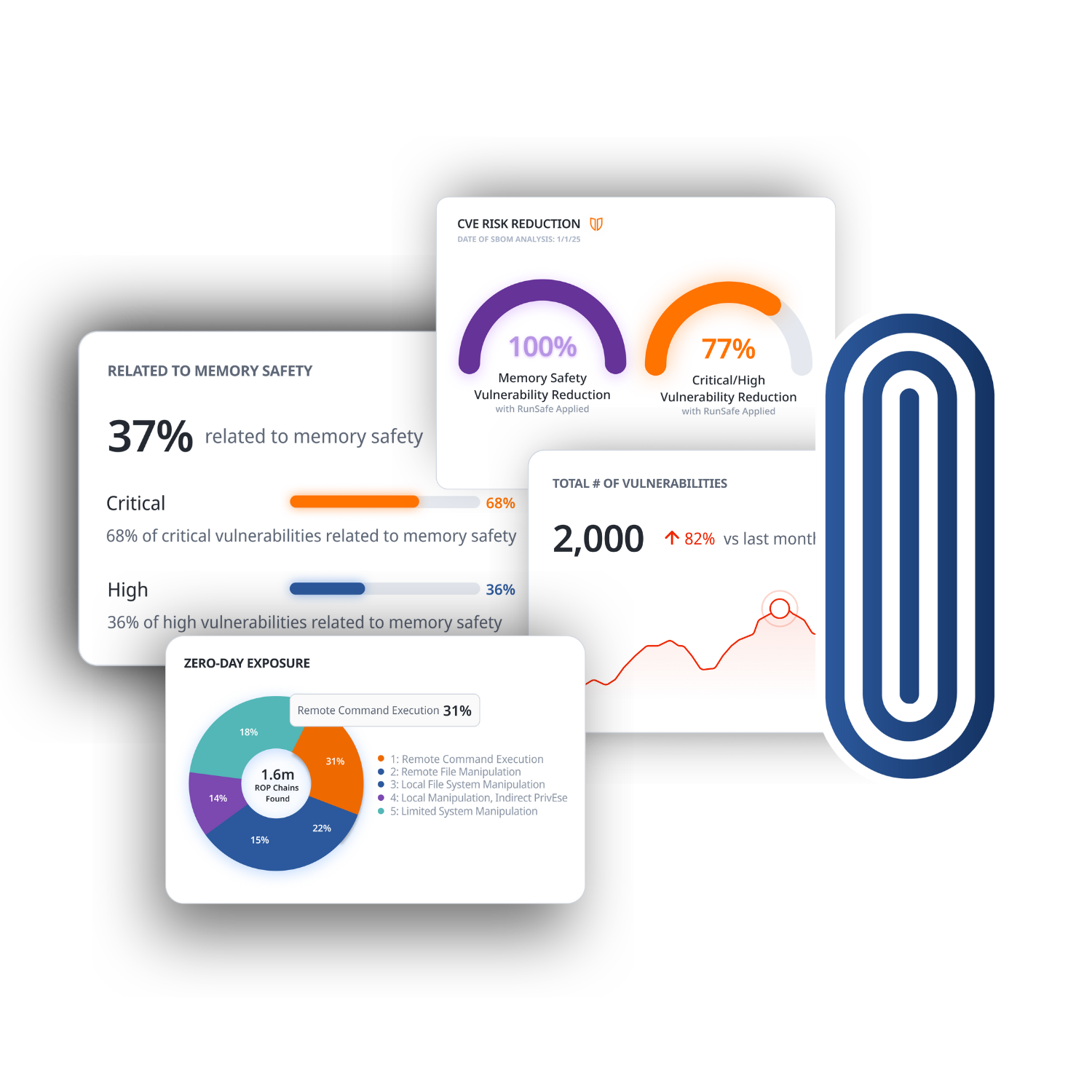
Have Eyes on Vulnerabilities in Your Software
RunSafe Identify provides the authoritative build-time SBOM generator for embedded systems, identifies vulnerabilities, and calculates risk reduction potential.
With full visibility into your software and weaknesses in your code, you can take action to mitigate vulnerabilities while meeting compliance requirements.


Protect New and Legacy Code
Automate code protection and free your developers from the constant cycle of patching.
RunSafe Protect safeguards software against memory-based vulnerabilities at runtime without compromising performance, providing much-needed protection for legacy systems and embedded software across critical infrastructure.

Monitor Software for Prompt Incident Response
RunSafe Monitor tracks software crashes to quickly identify potential threats. It filters out false positives, allowing your team to focus on real issues and respond more efficiently.

Awards

















