RunSafe Identify
Generate SBOMs at build time, enforce license policy, identify vulnerabilities in your software, and quantify risk with RunSafe Identify.
Generate SBOMs at Build-Time
RunSafe Identify generates detailed SBOMs for embedded systems at software build time, eliminating the need for binary analysis. Build-time SBOMs give full visibility into your software components with a full dependency tree and without a package manager.
With a complete SBOM, including C/C++ SBOM generation, organizations can quickly identify potential vulnerabilities in software components, understand common vulnerabilities across product lines, take action to prioritize mitigation, and meet compliance requirements, like the EU CRA.
RunSafe generates CycloneDX-compliant SBOMs that report on all mandatory NTIA minimum elements and integrates into your CI/CD pipeline for continuous security throughout development.

Identify and Quantify Vulnerabilities
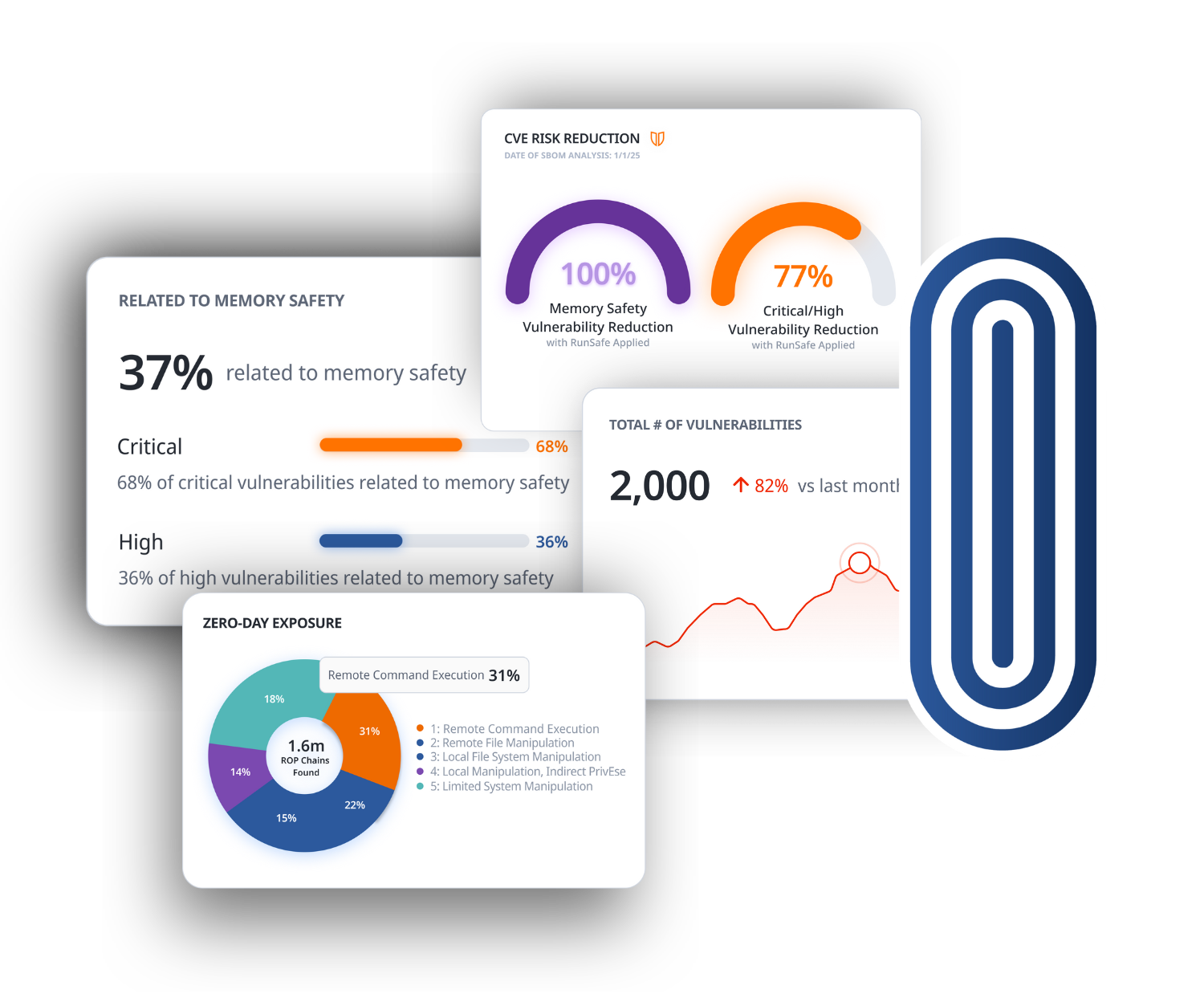
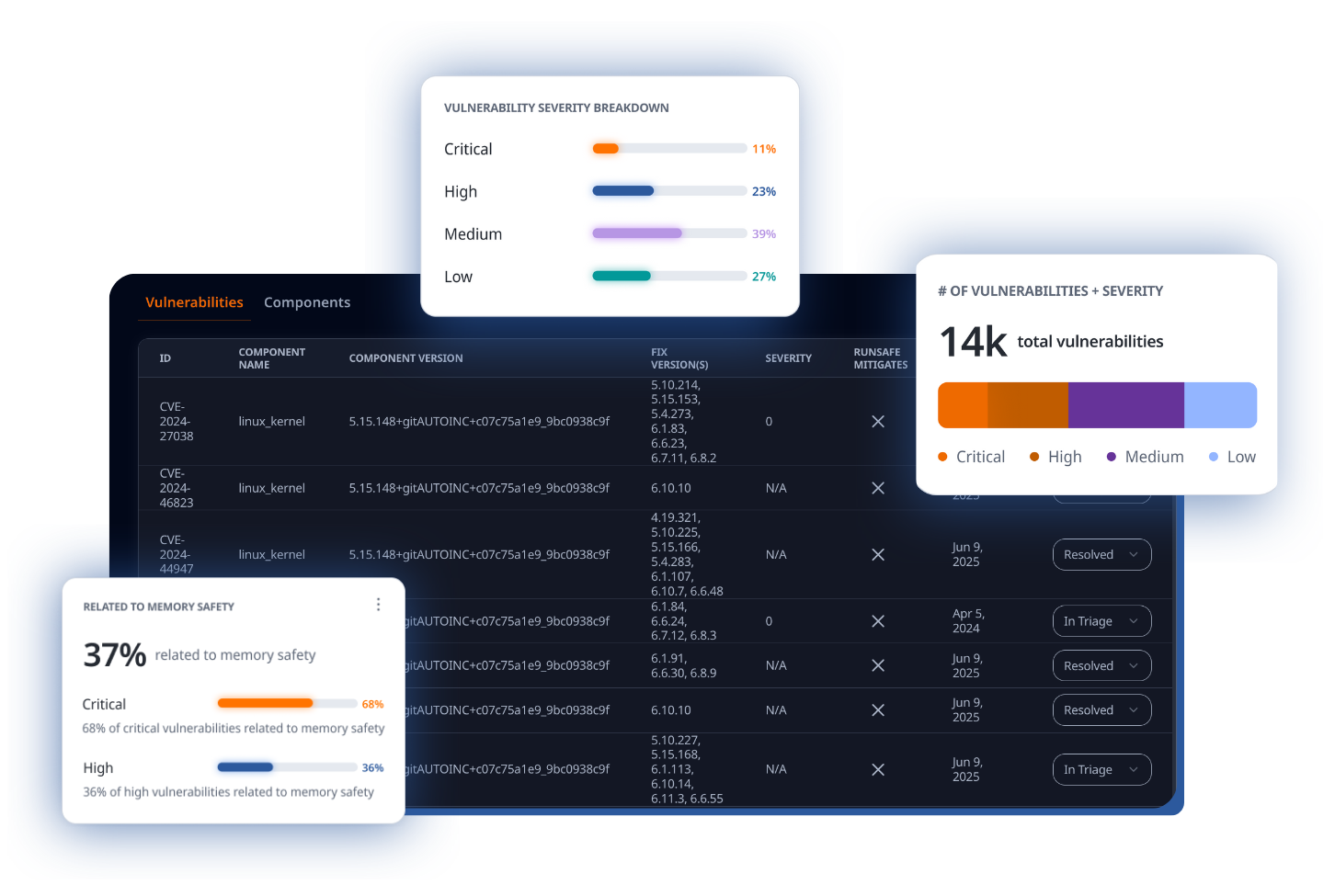
RunSafe identifies vulnerabilities in embedded software based on your SBOMs. See a breakdown of vulnerabilities identified, including component name and version, severity score, and if it is a Known Exploited Vulnerability (KEV). Triage vulnerabilities directly within the platform.
RunSafe Identify includes our Risk Reduction Analysis tool, which analyzes exposure to CVEs and memory-based zero days within embedded systems. By identifying weaknesses in libraries, components, and packages, RunSafe enables organizations to better understand their security posture and prioritize risks based on severity, exploitability, and impact on the system.

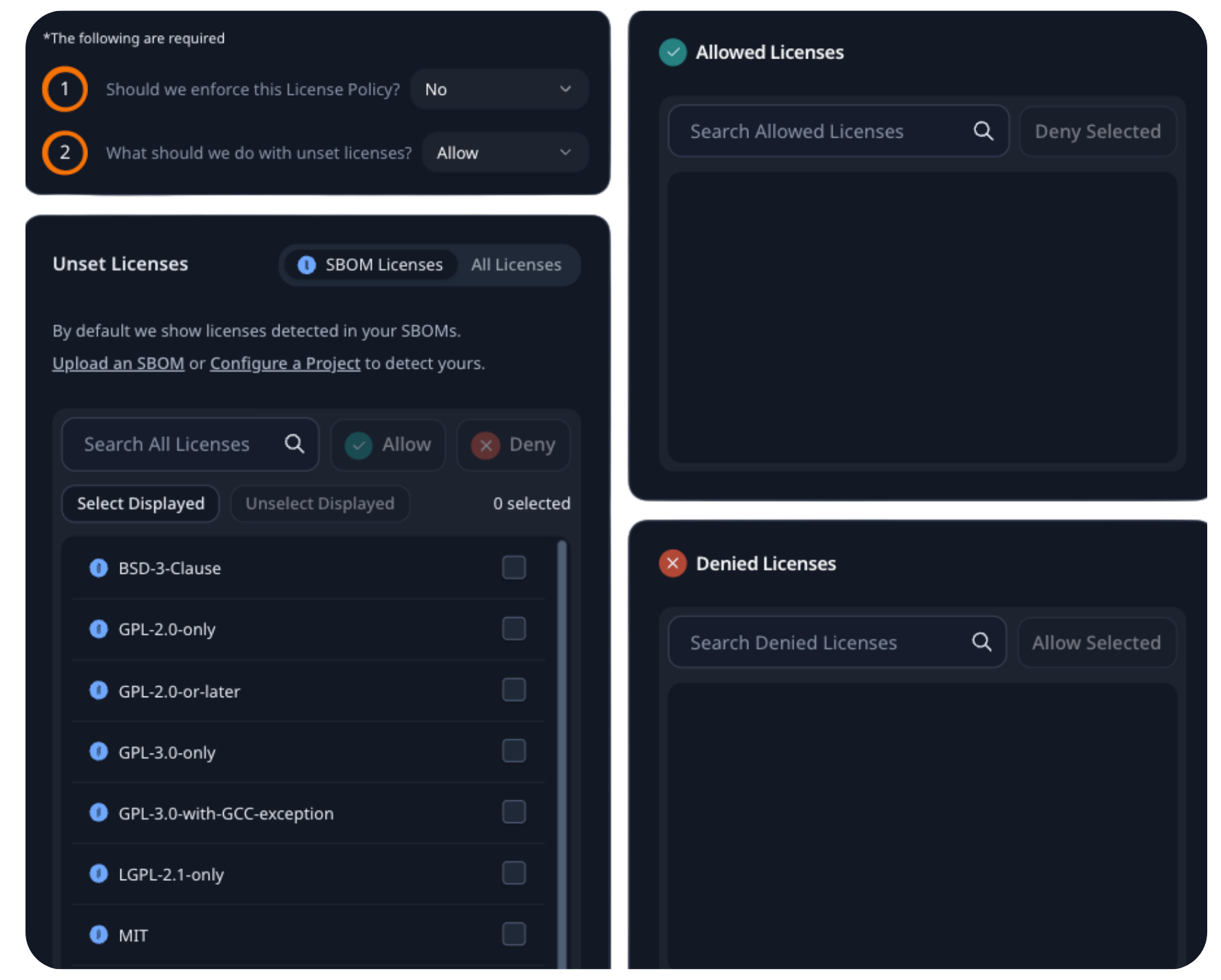
Enforce License Compliance
Embedded teams are concerned about “copyleft” licenses that can put IP and software at risk.
RunSafe’s license compliance feature allows organizations to surface licenses early and then block or approve them based on their specific risk profile.
Once configured, enforcement happens automatically in your CI/CD pipeline to prevent copyleft from reaching release or merge.
Know Exactly What’s in Your Software
Confident Software Supply Chain Security
By generating SBOMs, identifying vulnerabilities and monitoring open-source licenses, know what’s in your embedded software and how to protect it.
Regulatory
Compliance
RunSafe Identify supports companies needing to meet SBOM requirements, from the FDA to the EU Cyber Resilience Act.
Operational
Efficiency
By automating SBOM generation and vulnerability identification directly in your CI/CD pipelines, RunSafe takes the pressure off your teams and allows them to focus on innovation.
Try RunSafe Identify Today
Try RunSafe Identify for build-time SBOM generation, vulnerability identification, and license compliance. Start a free trial.