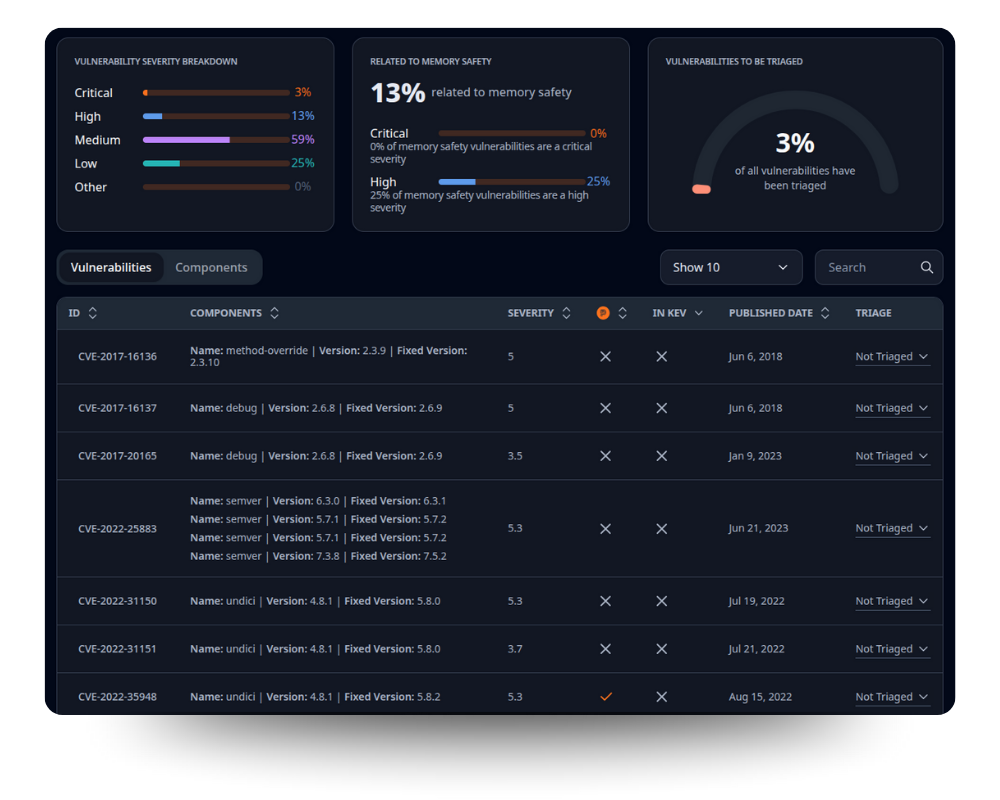
RunSafe is ending the year strong with a number of upgrades to the RunSafe Security Platform and big additions to our Identify solution, including reachability analysis and package and sub-package detection for QNX.
Here’s what’s new in December:
- RunSafe Security Platform: Single project view for important data at a glance
- RunSafe Security Platform: Historical SBOM reports, vulnerability triage sync, KEV data, and more!
- Identify: QNX package and sub-package detection and package grouping by directory
- Identify: Reachability analysis
- Identify: CLI usage improvements
Introducing Single Project View
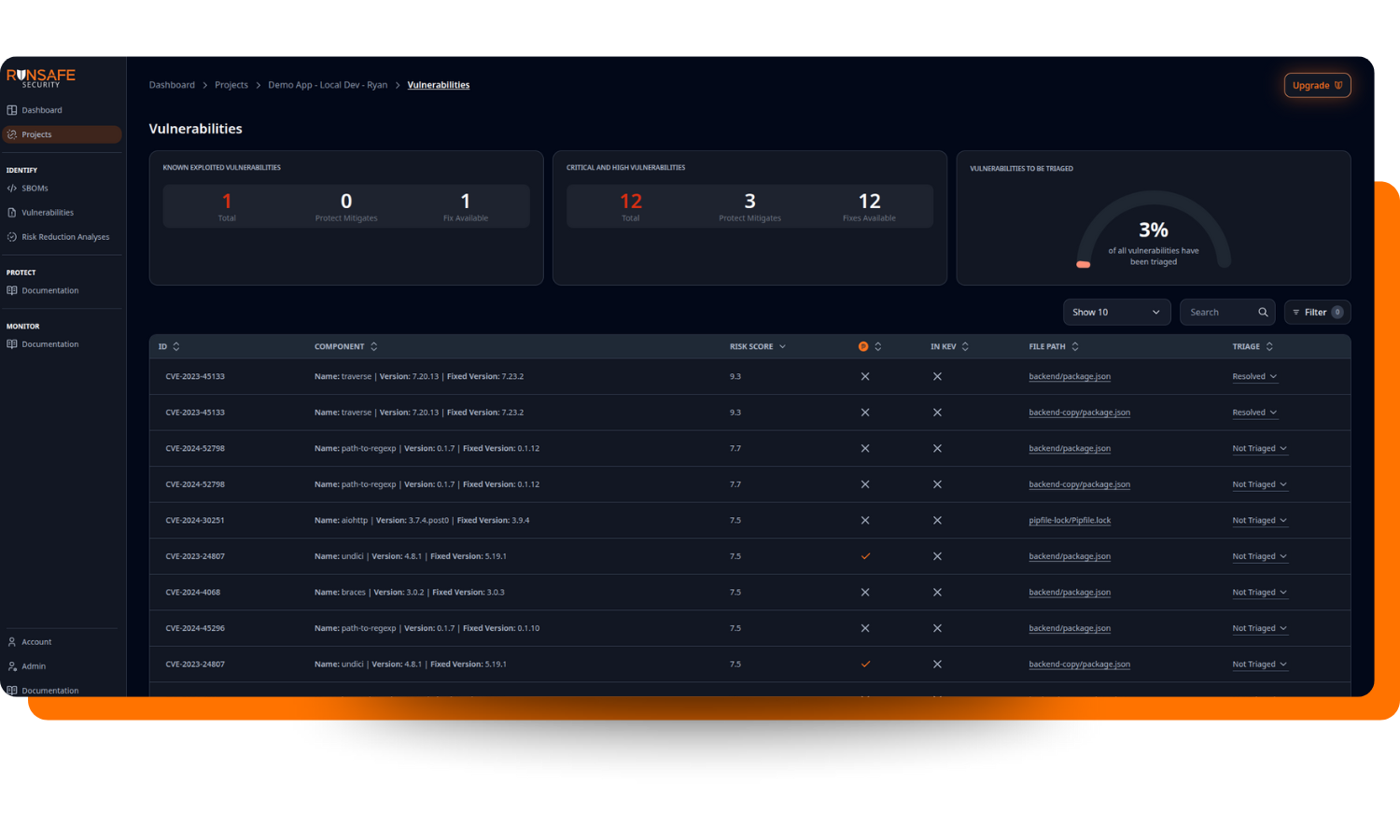
We’re excited to share a helpful new addition to the RunSafe Security Platform: Single Project View. This update provides a central dashboard for each project’s key data, enabling you to quickly view important information without needing to switch between pages.
With Single Project View, you can easily see:
- Known Exploitable Vulnerabilities (KEVs)
- Critical and High Vulnerabilities
- License compliance issues
- Enabled features
In addition to the high-level summary information, users can also dive into project-level details for vulnerabilities and license compliance as needed.
Recent Platform Upgrades
We’ve rolled out several improvements to make vulnerability management smoother and provide you with more precise and valuable security insights.
Historical SBOM Reports
You can now look back at how your SBOM reports have changed over time. If you scanned a project today and a vulnerability popped up yesterday, you can easily compare reports to see what changed and when. This view makes it easier to understand trends and document how your security posture is evolving.
The historical SBOM reports are built on top of our automatic nightly SBOM scans, so you’re always working with up-to-date vulnerability information. If something new is disclosed overnight, you’ll see it in your reports the next morning with no extra steps required.
Vulnerability Triage Sync
To help cut down on repetitive work, triage decisions now carry forward automatically. If you mark something as a false positive or accept a risk, that choice will stay in place for all future scans of the same SBOM. No more re-triaging the same issues. Your decisions stay consistent across scans.
Enhanced GitHub Integration
We’ve expanded our GitHub integration to include license compliance. Now you can handle both vulnerabilities and license issues right from your GitHub workflow.
KEV Data in SBOM Reports
SBOM reports now highlight vulnerabilities listed in CISA’s Known Exploited Vulnerabilities (KEV) catalog. This provides additional context to help prioritize issues that are currently being exploited in the wild.
New Docs Subdomain
Our documentation has moved to a new home at docs.runsafesecurity.com. This dedicated subdomain provides a more organized and accessible location for all RunSafe product documentation, making it easier to find the resources and guides you need.
Iron Bank Listing
RunSafe Security is now officially listed in Iron Bank, the DoW’s repository of hardened, digitally signed container images. We’re excited to support teams across the DoW with secure, accredited software.
Identify Adds QNX Package Detection and Package Grouping by Directory
QNX Package and Sub-Package Detection: Uncovering Hidden Vulnerabilities
RunSafe now supports QNX package and sub-package detection, improving vulnerability identification and visibility within QNX-based real-time operating systems (RTOS).
RTOS platforms like QNX and VxWorks bundle open-source components like GCC without providing separate Common Platform Enumerations (CPEs) for those underlying packages. Instead, QNX publishes a single CPE for the entire QNX Software Development Platform (SDP). This means customers must rely on the RTOS vendor to track and disclose vulnerabilities affecting any bundled sub-packages, limiting independent visibility into potential risk.
To address this gap, RunSafe now reports on both the main QNX SDP CPE and the CPEs of the sub-packages included within the platform. For example, in QNX 7.1, RunSafe reports on the QNX SDP CPE alongside the GCC 8.3.0 CPE provided as part of the QNX environment.
Without sub-package-level reporting, vulnerabilities in these components can go undetected. RunSafe closes this visibility gap, enabling more accurate vulnerability awareness in RTOS environments.
Package Grouping by Directory for Clearer SBOMs in Complex Builds
RunSafe now supports package grouping by directory, making it easier to organize files and represent packages accurately in SBOMs, especially for proprietary builds.
Using path globbing, teams can group files by directory and define them as logical packages with metadata like licenses, CPEs, or other package attributes assigned. In the resulting SBOM, all files that match a given glob pattern are represented as subcomponents of a defined package, creating a clearer and more accurate package layout. This is helpful when a single build produces multiple outputs, such as a library and an application built together.
This feature is particularly useful for C and C++ environments, where builds often generate multiple artifacts and package boundaries aren’t always obvious. RunSafe helps bring clarity and structure to even the most complex builds.
Reducing False Positives with Reachability Analysis
One of the most significant challenges in vulnerability management is dealing with false positives, or vulnerabilities reported in code that aren’t actually compiled into your final software build. We’re addressing this head-on with our new reachability analysis capability.
How It Works
RunSafe now leverages source file extraction to automatically identify which code is actually compiled into your software build. By analyzing which source files are included in your build process, we can automatically triage away vulnerabilities that aren’t relevant because the affected code was never compiled in.
Benefits
Reachability analysis is particularly powerful for complex builds, such as Linux kernel images. When scanning a Yocto image today, you might see 3,000 Linux kernel vulnerabilities flagged. However, many of these are in drivers or components you’re not actually using. For example, if there’s a vulnerability in a Bluetooth driver or a specific sound driver, but your device doesn’t use Bluetooth or that particular sound driver, those vulnerabilities don’t represent a real risk to your system.
With reachability analysis, RunSafe can automatically filter out these irrelevant vulnerabilities, reducing your vulnerability count from potentially thousands down to the subset that actually matters for your specific build. This means less time spent investigating false positives and more time focused on addressing actual security risks.
The feature will provide you with more accurate vulnerability data, helping your team work more efficiently and maintain better security hygiene.
CLI Usage Improvements
We’ve made several improvements to the RunSafe CLI to streamline workflows and improve reliability.
Easier License Authentication
A new runsafe_sbom login command has been added to simplify license authentication. This allows users to authenticate or update licenses directly from the CLI without restarting the service, making automation and CI/CD workflows easier to manage.
Improved VxWorks Version Detection
We fixed an issue with VxWorks version detection to better support non-standard installations. The CLI now more reliably identifies VxWorks environments even when directory layouts or versioning differ from default configurations, improving compatibility across a wider range of embedded build systems.
Interested in Learning More?
For current RunSafe customers, reach out to your account team to learn how these updates can strengthen your embedded security and software supply chain security across your environments.
If you’re just getting started with RunSafe, contact us to see how our platform helps organizations reduce software risk, improve vulnerability insight, and protect products from development through deployment.