It’s no secret that despite our best efforts to eliminate exploits in today’s enterprise applications and software, they’re still finding a way in. In order to begin fighting these exploits and immunizing your software, the first place to start is identifying their avenues of attack.
Current technologies exist to help in finding vulnerabilities, but unfortunately, they’re not sufficient. Here are the problems we’re facing:
- Software is passing scanning tests while the technology is missing 50% of present vulnerabilities and weaknesses in code
- Runtime app monitoring technology misses deep indicators of lurking threats
- Heartbeat checks aren’t reliably reporting system performance and stability
- Low-level activity is sneaking by, undetected, and causing disruptions in service
- There is an increasing dependence on open source packages, but organizations don’t have a way of mitigating the vulnerabilities that threaten infrastructure
Have you ever wondered how exposed your systems are to vulnerabilities?
What’s needed is a way of reliably and accurately monitoring the health and stability of systems at runtime so that you can flag failures or potential attacks before a disruption of service occurs.
How the Technology Works
Our team at RunSafe Security set out to make indicators of instability and unreliability visible at runtime that most technologies miss today.
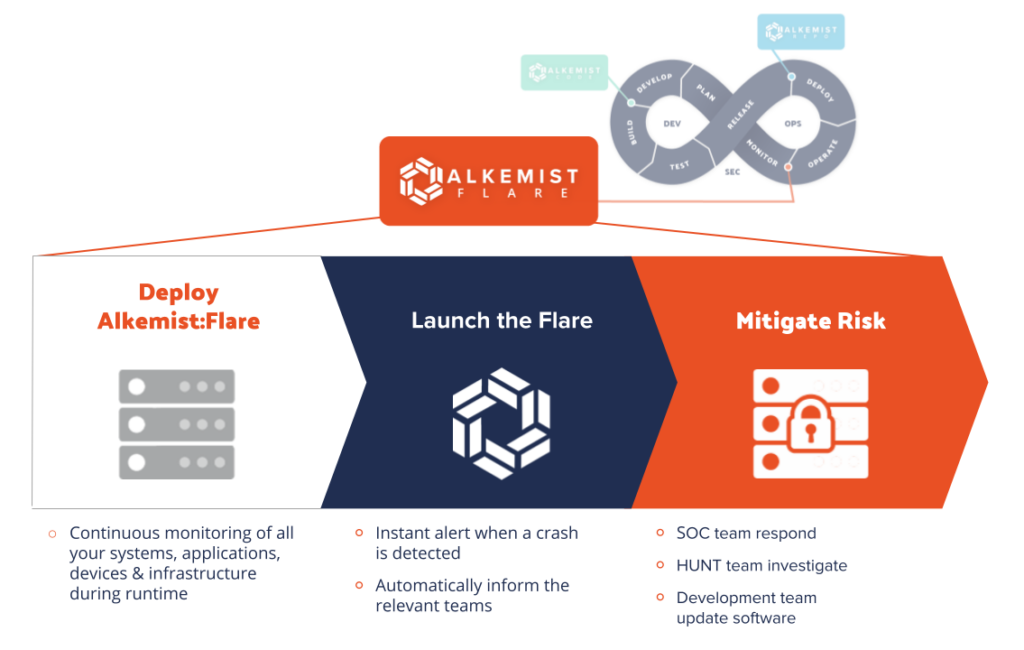
And so, Alkemist:Flare came to be. Like a signal flare, Alkemist:Flare delivers a bright, real-time indicator of application failures related to cyber attacks and software weaknesses, capturing at runtime what scanning tools don’t identify at testing time.
Now, IT managers, security operations, and development teams can see events that are causing system reliability issues, performance degradation, service availability risk, and attack vectors that lead to disruption in service. Users receive alerts identifying process instability and vulnerability indicators, providing the opportunity to fix code weaknesses, report vulnerabilities to software vendors, build additional layers of protection, and share telemetry data to security operations for automated responses or detailed research.
Alkemist:Flare delivers continuous monitoring of:
- Cloud workloads
- Software applications
- Open source packages
- IT/OT infrastructure
- Endpoint devices
- Embedded systems
Who’s Using Security Monitoring?
Across all industries, the first step in preventing service disruption is being instantly aware of vulnerabilities within software. Here are a few ways that different organizations have used vulnerability monitoring to improve their operations:
For a FinTech SaaS company, it’s imperative to protect sensitive customer data—not just for compliance, but for reputation purposes. The organization implemented reliable monitoring technology to enhance their ability to identify vulnerabilities before they became problems.
An embedded software provider in the energy space needs to monitor its distributed energy resources to ensure bad actors aren’t exploiting existing vulnerabilities in the software. By using technology that accurately indicates stability while instantly flagging failure and potential attacks, they are able to trust their distributed energy resources are healthy.
To ensure their customers’ open source software was not being exploited, a managed services security provider combined cyberhardening tools with monitoring technology. The team was able to increase the speed and effectiveness of their response if an attack did occur by knowing about it immediately.
Applying Reliable Monitoring to Higher Business Objectives
Alkemist:Flare captures runtime application failures and alerts your team members, so you’re able to monitor the overall stability and reliability of your systems at runtime, and increase the speed and effectiveness of your cyber attack response.
Are you aware of all of your vulnerabilities? Get a free 30-day analysis of your software with Alkemist:Flare today.
The report includes:
- An assessment of the stability and reliability of the software across your systems
- A prioritization of vendors or open source packages that could put your infrastructure at risk
- Recommendations on how to mitigate exposure to cyber attack for your most vulnerable software