A Comprehensive Guide to Creating and Utilizing SBOMs for Enhanced Cybersecurity
Learn about the importance of Software Bills of Materials (SBOMs) and how you can effectively generate SBOMs for embedded systems.
By downloading this guide, you will gain:
- Knowledge of SBOM components tailored for embedded systems
- Step-by-step guidance on generating and maintaining SBOMs
- Strategies for incorporating SBOMs into your development process
- Techniques for using SBOM data to track and mitigate security risks
- Insights into overcoming challenges in managing SBOMs for embedded systems
- Case studies of successful SBOM integration
Why SBOMs Are Needed
Adopting SBOMs as part of a proactive cybersecurity strategy is crucial. They not only help identify and mitigate potential vulnerabilities but also streamline the process of software updates and patches, ensuring that embedded systems remain secure throughout their lifecycle.
By maintaining comprehensive and up-to-date SBOMs, organizations can better manage risks, respond to security incidents more effectively, and demonstrate compliance with industry standards.

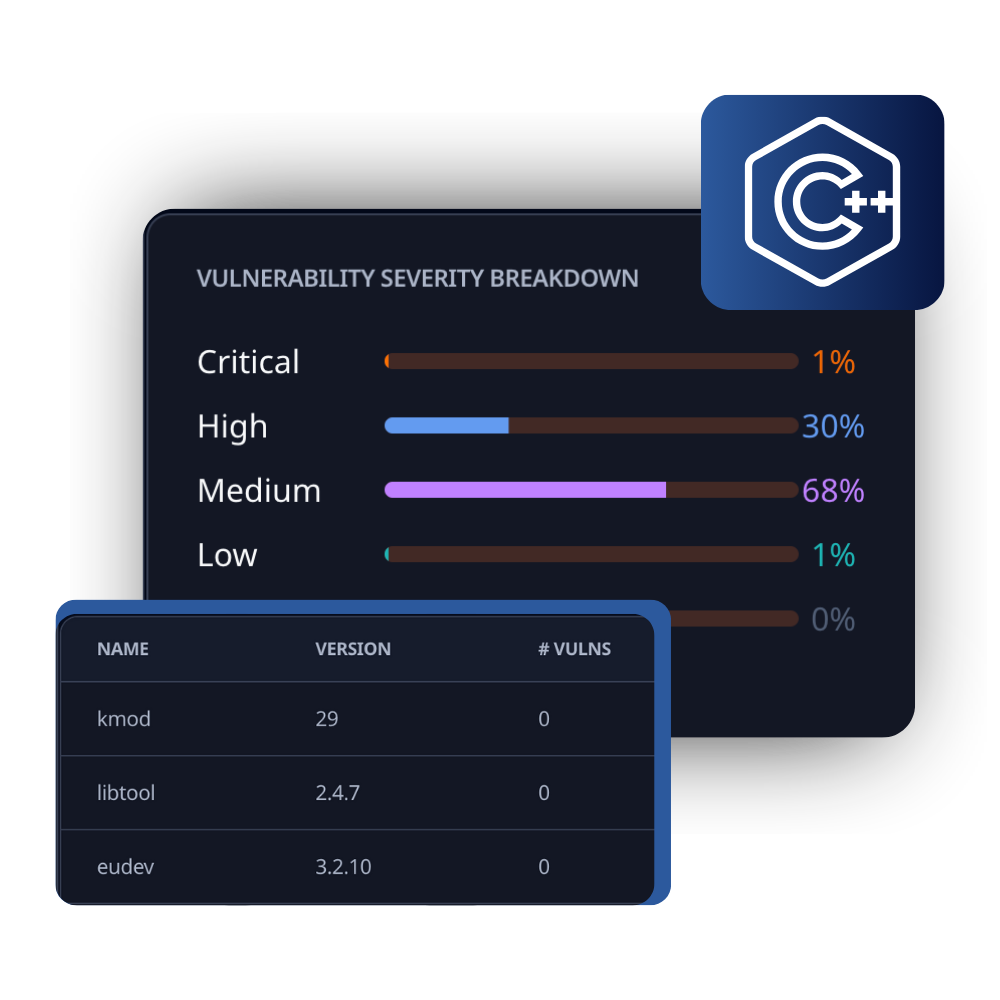
Creating SBOMs for Embedded Systems
SBOMs help improve the security of embedded systems across critical infrastructure, including automotive, medical devices, and industrial control systems. Embedded systems often operate with limited resources and have long lifecycles, making them particularly vulnerable to cyber threats.
Learn about available tools and technologies for generating SBOMs for embedded systems, and best practices for ensuring completeness and accuracy.
