Strengthen Security with Attack Surface Reduction Scoring

Understand Your Software Supply Chain Risk Score
Scoring your software supply chain’s attack surface is essential for understanding and quantifying the security risks associated with your external-facing software assets.
Know which components must be hardened immediately, which can be hardened in the next release, and which should be monitored to improve your cybersecurity posture. This helps prioritize security efforts, allocate resources more effectively, and track improvements over time.
By identifying and addressing these critical components, you enhance your overall security strategy and strengthen your defense against potential vulnerabilities.
“From our perspective, adding RunSafe means we have more opportunity to shrink the attack surface and reduce overall risks for our customers since security is now already built into our product.”
Enhanced Risk Management
Data-Driven
Decisions
Make informed security decisions with detailed reports that offer clear insights for effective vulnerability management and strategic improvements.
Proactive
Defense
Stay ahead of evolving threats with proactive risk reduction strategies that identify and address potential issues before they escalate.
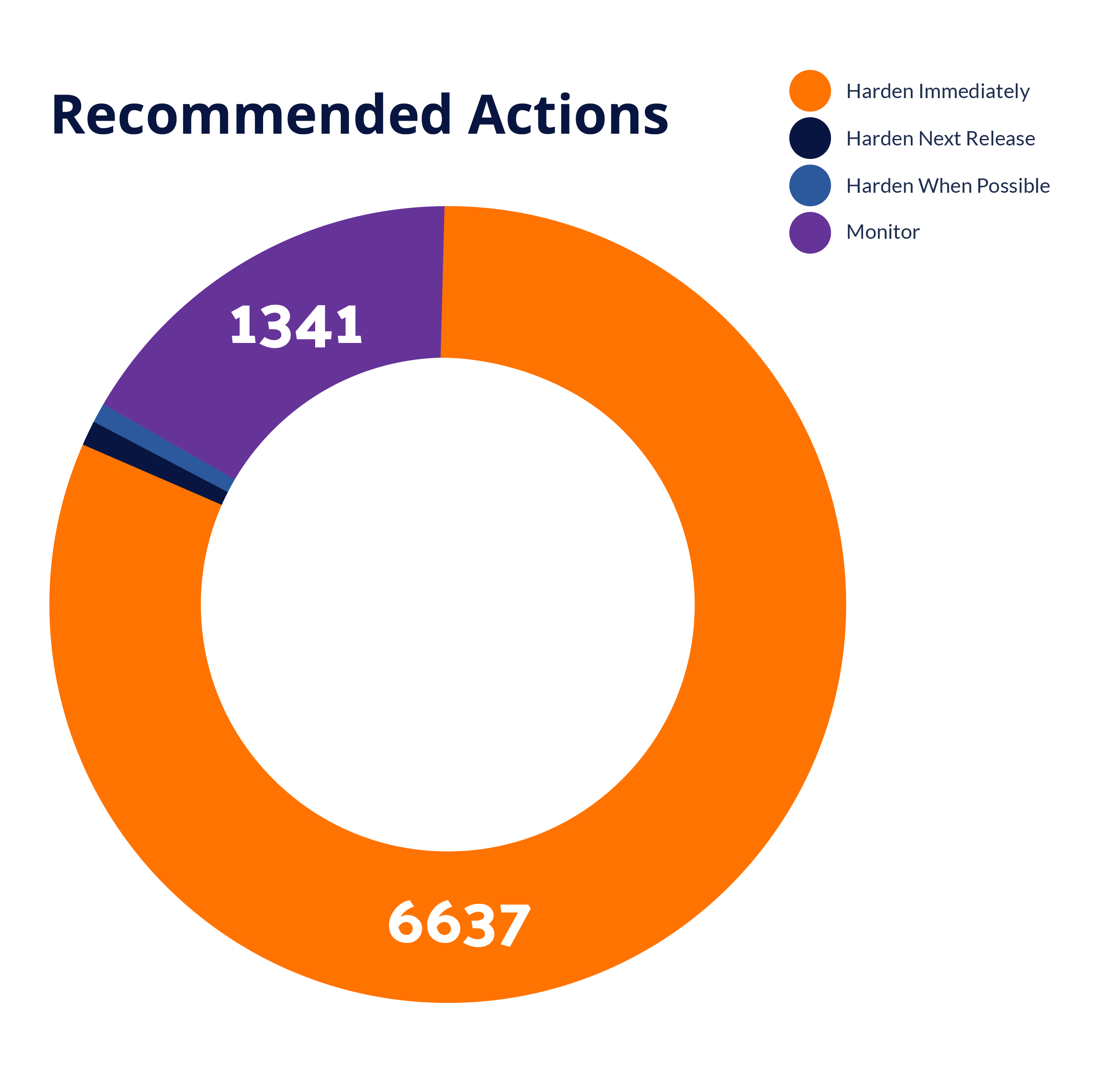
Analyze Your Security Posture for Informed Decisions with Attack Surface Reduction Scoring
RunSafe Security’s Attack Surface Reduction scoring offers a detailed analysis of your security posture. The report includes identifying vulnerabilities, assessing potential risks, and quantifying risk reductions. RunSafe’s scoring focuses on critical indicators like recency, frequency, and severity of vulnerabilities.
By providing a clear picture of your security landscape, the report helps organizations prioritize remediation efforts and allocate resources more effectively. This targeted approach ensures that your security measures are both efficient and impactful, strengthening your defenses against evolving cyber threats.
RunSafe enables organizations to identify high-risk areas, make informed security decisions, and strengthen security strategies. By understanding your attack surface, you can implement targeted security measures, enhancing the resilience of your critical infrastructure against evolving cyber threats.


Quantifying Risk Reduction: Strengthening Security and Ensuring Compliance
Quantifying risk reductions allows you to measure the effectiveness of your security strategies. This data-driven approach helps in demonstrating compliance and governance to stakeholders, providing clear evidence of your proactive efforts to secure your systems. By prioritizing and addressing vulnerabilities, you ensure continuous improvement in your security posture.
By focusing on the most critical vulnerabilities, you can allocate resources efficiently and mitigate risks proactively. This strategic approach enhances your overall security posture, ensuring your embedded systems are resilient against cyber threats.
Latest Resources
The Best SBOM Tools for C/C++ Development
Generating an accurate Software Bill of Materials (SBOM) for C/C++ code is notoriously difficult. Unlike ecosystems with centralized package managers, C/C++ projects rely on vendored code, static linking, and manual dependency management, which causes most SBOM tools...
Why Connected Cars Need “Less Data,” Not More: Cybersecurity, Autonomy, and the Future of Connected Cars
Connected vehicles are getting smarter by the model year, but also noisier, more exposed, and harder to secure. Cars include dozens of computers and sensors, plus cameras, microphones, and wireless connections that constantly observe what is happening inside and...
Breaking Down the Top 15 Software Supply Chain Attacks
Software supply chain attacks surged at the end of 2025, with 41 attacks uncovered in October alone. And there was an unmistakable pattern. Attackers stopped trying to breach organizations directly and instead focused on opportunities for widespread impact. Why pick...
Ready to Get Started?
RunSafe strengthens security by using attack surface reduction scoring to identify vulnerabilities, quantify risks, and prioritize mitigation efforts, minimizing exposure to potential cyber threats.


