Table of Contents:
The Attack Surface is Increasing: Understand Your Risk & Protect Your Software
Taking Inspiration From Loyalty Marketing Programs
Eliminate Software Vulnerabilities
With cyber attacks on the rise, it is more important than ever that your software is protected against threat actors, data loss, data theft, and more. Beyond phishing attacks, cyber criminals are actively exploiting your software vulnerabilities. Are you doing everything you can to protect your Software Bill of Materials (SBOM) components, preventing software exploitation and other breaches?
We just launched our Attack Surface Reduction Index ™ (ASRI) to help organizations prioritize how best to handle software vulnerabilities. The inspiration for the ASRI is rather surprising. In fact, back in the early 2000s, we never imagined how the retail loyalty marketing programs could inspire a strategy to reduce the attack surface in software products and enterprise IT software infrastructure.
Yet, today, as the most loyal campaign in software is likely the bad actor campaign to hold software for ransom, compromise systems, or manipulate code to do something unintended, it is fitting that lessons learned from the analytical models in loyalty marketing can be used to disrupt software bad actors across critical infrastructure, connected devices, and cloud workloads. In fact, in today’s connected, digital world, flipping loyalty marketing on its head to thwart loyal attackers makes a lot of sense.
Taking Inspiration From Loyalty Marketing Programs
The essence of retail loyalty marketing incorporates three dimensions of one’s customer: recency of visit, frequency of visit, and monetary spend. By understanding these factors, retail marketers target the best customers and tailor marketing offers accordingly. In effect, they optimize campaigns to boost performance of your overall marketing spend.
At RunSafe Security, we asked ourselves, what if we used recency, frequency, and severity to help optimize mitigation tactics to thwart the attacker. Our most loyal users—attackers—use memory-based exploits most frequently and we know memory-based exploits have the highest severity. We can use this data to prioritize code hardening and mitigation that cuts the would-be attacker at their knees.
So we started with 800,000 software packages and whittled this down to about 140,000 software packages to analyze, using known exploits and vulnerabilities associated with software. We paired this with some machine-learning algorithms to develop a model to score software so its owners can optimize mitigation based on the exposure.
By applying the model to the full set of 140,000+ software packages with information on at least 10 known vulnerabilities, we developed this scatter plot chart with four quadrants that are based on the median Attack Surface Reduction Index and the median vulnerability (CVE) count for each software package.
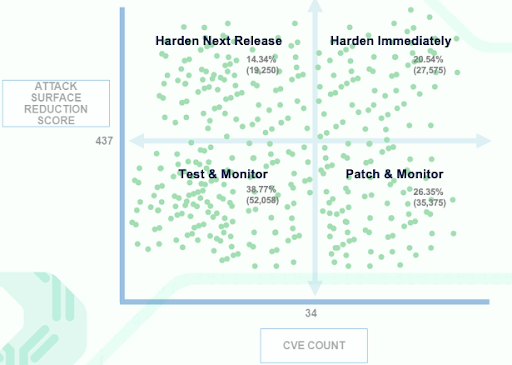
As seen in the chart, the upper right quadrant becomes low-hanging fruit to take immediate action: high vulnerability count and high opportunity to reduce the attack surface.
Eliminate Software Vulnerabilities
Our powerful methodology examines the Software Bill of Materials (SBOM) and alerts stakeholders of the level of risk they face. RunSafe technology can then automate the high-risk code hardening, significantly lowering your risk of attack.
Click here to read our whitepaper on how you can apply this approach to your software. Or, if you want to discuss directly with a RunSafe solution engineer to learn how to apply the findings to enhance your software bill of materials, develop toolchains, or software supply chain risk management program, contact us today and we will connect with you immediately.
Let’s get rid of some of the most loyal users of our network—the attacker—in a simple way that helps you prioritize your efforts.
______________________________________________________________________________
FAQs:
What is Attack Surface Reduction IndexTM (ASRI)?
Attack Surface Reduction IndexTM (ASRI) is a risk assessment software that can identify software vulnerabilities at the highest risk of breach so that you can prioritize mitigation. With ASRI you can secure the software supply chain with a better understanding of which vulnerabilities to focus your attention on.
How does ASRI assess risk?
RunSafe took inspiration from the retail marketing loyalty programs and developed a scoring system that uses a model based on recency, frequency, and severity of Common Vulnerabilities and Exposures (CVEs).
Can RunSafe help me prevent software exploitation and other breaches?
Absolutely. To learn more about RunSafe Security’s Attack Surface Reduction IndexTM (ASRI), email info@runsafesecurity.com or download our whitepaper.




