The healthcare industry has reached a cybersecurity tipping point. While IT has been the primary focus of security efforts to date, RunSafe Security’s 2025 Medical Device Cybersecurity Index found that 22% of healthcare organizations have experienced cyberattacks that compromised medical devices.
The consequences reach beyond network disruptions: 75% of these incidents directly compromised patient care, with nearly half compelling organizations to revert to manual processes just to maintain operations. When a cyberattack necessitates transferring patients to other facilities, which occurred in 24% of cases, the situation creates serious medical emergencies.
The convergence of IT and OT security is putting medical devices at the center of cybersecurity strategy, the report shows. Healthcare organizations can no longer protect medical devices in isolation. Securing patient-critical systems now requires defending the entire interconnected ecosystem.
Because of this, we’re seeing a changing relationship between healthcare providers and medical device manufacturers. The findings of the 2025 Index show that for healthcare buyers, cybersecurity is becoming a gatekeeper to market access.
Medical Device Cybersecurity: From Nice-to-Have to Must-Have
Healthcare buyers have spoken with their wallets and their purchasing decisions. The data reveals a dramatic transformation in how medical devices are evaluated and purchased:
- 83% of healthcare organizations now integrate cybersecurity standards directly into their RFPs
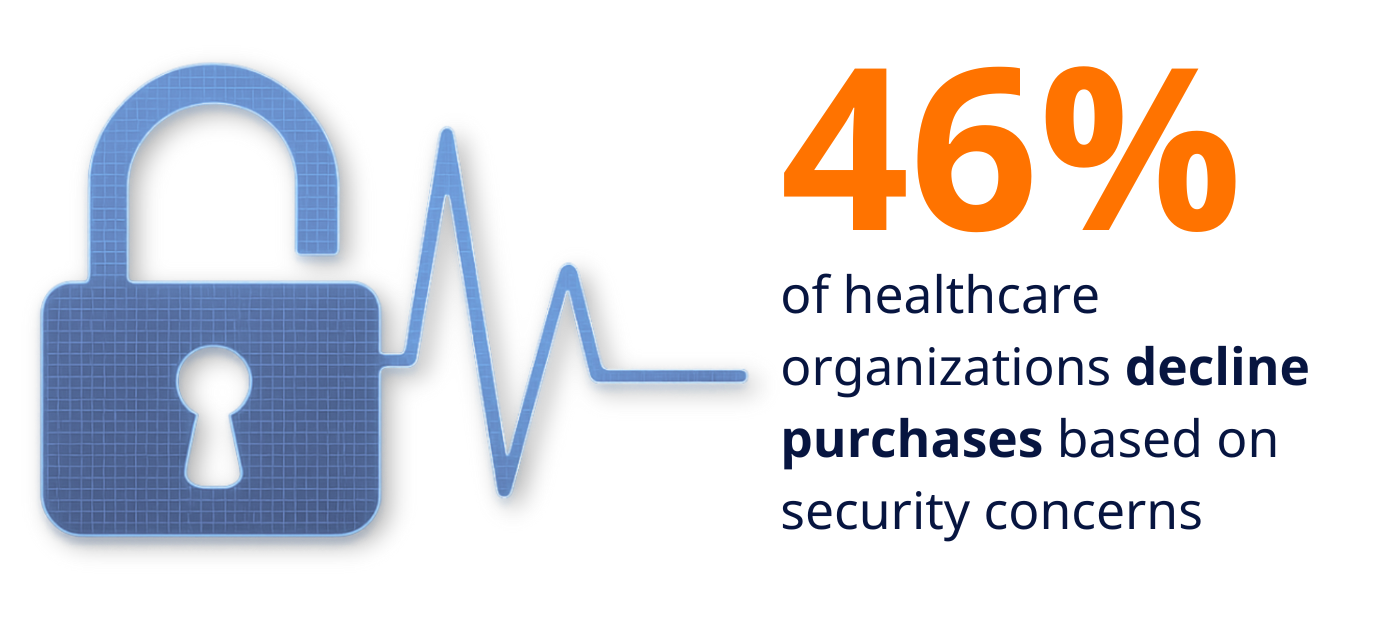
- 46% have declined to purchase medical devices due to cybersecurity concerns
- 79% are willing to pay a premium for devices with advanced runtime protection
When nearly half of potential buyers are prepared to walk away from purchases over security issues, manufacturers can no longer treat cybersecurity as an afterthought. This willingness to reject products represents a fundamental shift from traditional procurement practices where functionality and cost dominated decision-making.
Healthcare leaders have moved from asking “What can this device do?” to “How secure is this device?” The organizations that have experienced attacks understand that the most feature-rich device in the world can become a liability if it is not secure.
The Trust Equation Has Changed
The ripple effects extend beyond individual purchasing decisions. Nearly a third (32%) of healthcare organizations report that security incidents have affected their trust in specific vendors, requiring additional security verification from previously trusted partners.
Those manufacturers must now prove their security credentials to maintain existing relationships, not just win new ones. Healthcare organizations are conducting security audits of their entire vendor ecosystem, reassessing partnerships through the lens of cybersecurity risk rather than traditional performance metrics.
What Healthcare Leaders Want: Transparency and Built-In Defense
The survey data reveals clear expectations from healthcare buyers. They are not asking for band-aid solutions but want security baked into the device’s DNA from day one.
1. Software Bills of Materials (SBOMs) Are Non-Negotiable
78% of organizations consider SBOMs essential or important in procurement decisions. This extends beyond regulatory compliance to practical vulnerability management. The FDA now requires SBOMs in premarket submissions, and healthcare buyers understand that knowing device components constitutes fundamental ongoing security. Transparency becomes a competitive necessity.
However, generating comprehensive and accurate SBOMs remains challenging for many embedded medical devices written in C/C++. Traditional binary analysis SBOM solutions often produce excessive false positives and overlook critical components, such as static libraries. Healthcare organizations increasingly seek vendors who can provide build-time SBOM solutions that accurately capture only the components present in the final device.
2. Built-In Security Over Bolt-On Solutions
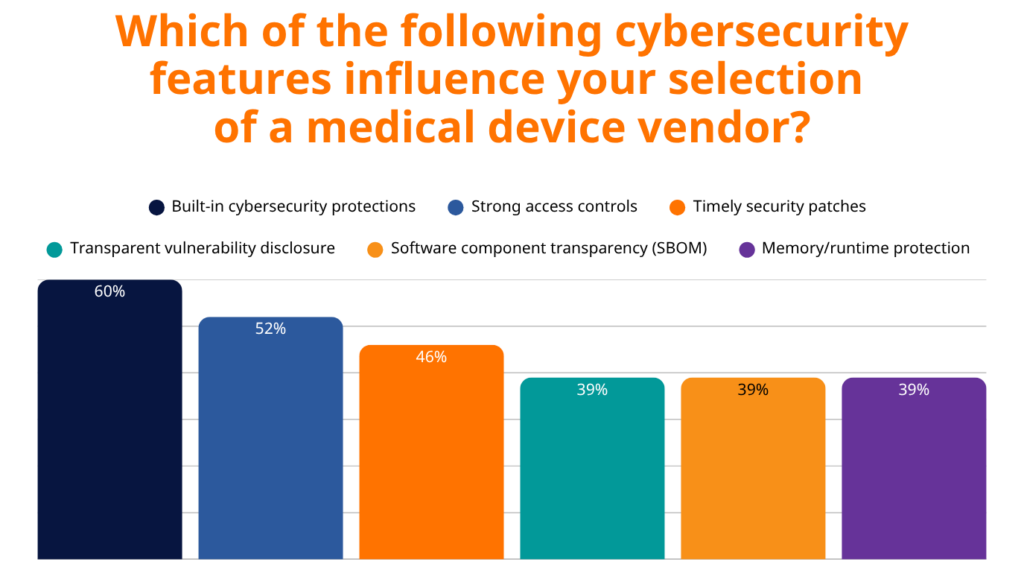
60% of healthcare organizations prioritize built-in cybersecurity protections when selecting vendors. This preference reflects hard-learned lessons where retrofitted security measures proved insufficient against sophisticated attacks.
Runtime protection technologies are gaining traction, with 36% of organizations actively seeking devices with these capabilities, while another 38% are aware of these technologies but don’t yet require them. This suggests the market is evolving rapidly from early adoption to mainstream expectation.
3. Premium Pricing for Premium Protection
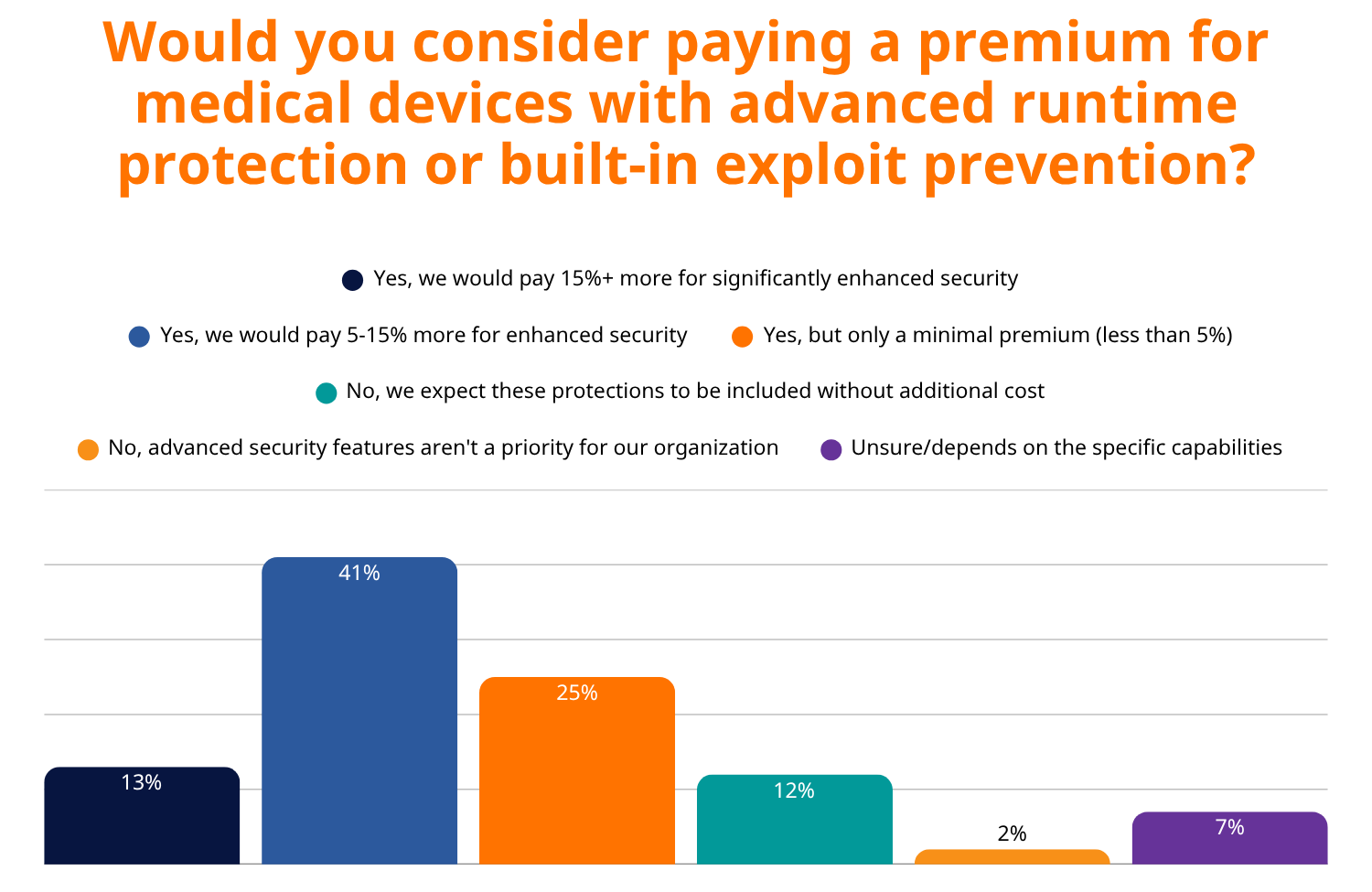
Perhaps most telling is healthcare buyers’ willingness to invest in advanced security. 79% of buyers would pay a premium for devices with advanced runtime protection, with 41% willing to pay up to 15% more for enhanced security.
This demonstrates that healthcare leaders have moved beyond viewing cybersecurity as a checkbox requirement to understanding it as a complex, resource-intensive discipline that requires ongoing investment. They recognize the documented financial impact of attacks like WannaCry, which cost the NHS £92 million, and understand that prevention is far more cost-effective than recovery.
The Regulatory Landscape Is Amplifying Demands
73% of healthcare organizations report that new FDA cybersecurity guidance and EU regulations are already influencing their procurement decisions. The regulatory environment is creating a cascading effect where compliance requirements drive purchasing behavior, making cybersecurity not just a competitive advantage but a regulatory necessity for market access.
Key regulatory drivers include:
- FDA’s Section 524B mandates cybersecurity information in submissions for network-capable devices
- The EU’s Cyber Resilience Act imposes mandatory cybersecurity requirements on connected products
- The NIS2 Directive explicitly targets medical device manufacturers with cybersecurity compliance requirements
The Financial Reality: Budgets Are Rising, Confidence Is Lagging
Healthcare organizations are responding with their wallets—75% increased their medical device and OT security budgets over the past 12 months. However, only 17% feel extremely confident in their ability to detect and contain attacks on medical devices.
This gap between spending and confidence suggests that simply throwing money at the problem isn’t enough. It highlights the critical need for solutions that work within the unique constraints of medical devices that often can’t be easily patched, may run on legacy operating systems, and require 24/7 availability for patient care.
What This Means for Medical Device Manufacturers
The transformation of healthcare cybersecurity expectations presents both opportunities and imperatives for manufacturers:
Opportunities:
- Economic foundation for security innovation: With buyers willing to pay premium prices, manufacturers now have the financial justification to invest heavily in security features
- Competitive differentiation: Manufacturers who embrace transparency and built-in security can capture market share from competitors who lag behind
- Regulatory compliance as market access: Meeting new cybersecurity requirements extends beyond avoiding penalties to gaining access to buyers who will not consider non-compliant products
Imperatives:
- Secure by Design: Retrofitting security is no longer acceptable; it must be integrated from the ground up
- Transparency through SBOMs: Accurate, comprehensive Software Bills of Materials are becoming table stakes
- Runtime protection: Advanced security features like runtime exploit prevention are rapidly moving from nice-to-have to must-have
- Ongoing vulnerability management: Manufacturers must demonstrate proactive approaches to identifying and addressing security issues
The Path Forward: Prevention Over Reaction
The data in the 2025 Index makes it clear that healthcare is moving from reactive cybersecurity to proactive prevention. The organizations that have experienced attacks understand that the most sophisticated incident response plan is no substitute for preventing the attack in the first place.
The healthcare industry is essentially conducting risk-based purchasing decisions, weighing the cost of advanced security features against the potential catastrophic consequences of device vulnerabilities. And increasingly, they’re concluding that the cost of prevention is far lower than the cost of compromise.
For medical device manufacturers, this transformation represents a fundamental shift in market dynamics. Those who embrace security transparency, integrate runtime protections, and demonstrate proactive vulnerability management will find themselves positioned to capture market share in an industry increasingly willing to invest in advanced protection.
Conversely, manufacturers who treat cybersecurity as an afterthought risk not only regulatory rejection but also exclusion from a market that has fundamentally redefined what constitutes an acceptable medical device.
The convergence of IT and OT security, combined with unprecedented regulatory oversight and buyer sophistication, has created a new competitive landscape where cybersecurity excellence serves as the foundation upon which trust, market access, and patient safety are built.
Key Takeaways for Medical Device Manufacturers
- Cybersecurity is now a gatekeeper to market access—nearly half of healthcare buyers will reject products over security concerns
- Built-in security trumps bolt-on solutions—60% of buyers prioritize integrated cybersecurity protections
- Transparency through SBOMs is non-negotiable—78% consider them essential or important in procurement decisions
- Premium pricing is acceptable for premium protection—79% of buyers will pay more for advanced security features
- Regulatory compliance drives purchasing behavior—73% report that new cybersecurity guidance influences procurement decisions
The message from healthcare leaders is clear: security isn’t negotiable anymore. It’s the price of admission to a market.
Download the full 2025 Medical Device Cybersecurity Index for all the key takeaways and findings.
Learn more about how RunSafe Security helps medical device manufacturers integrate security with our Protect solution and unique SBOM generator.