At RunSafe Security, we have been busy developing ways to accelerate integrating security into the software development process by aligning with the DevSecOps push. We love what our friends at Jenkins, Kubernetes, Docker, RedHat OpenShift and so many others are doing – and we think that it is time for us to step up to the table and once and for all put the “Sec” into DevSecOps.
There are some words of caution, however, because automating sophisticated security has had some challenges that can slow developers down. In fact, Gartner lists three reasons why companies have not yet adopted DevSecOps, including: (1) developers must change behavior; (2) providers are forcing legacy security tactics into DevOps; and, (3) DevOps is still in the Trough of Disillusionment.
Now, what if I told you RunSafe’s cyberhardening tool, Alkemist, could help you overcome these reported challenges developers face? Let’s address each one individually:
- Developer Effort – there are plenty of companies that offer code review, scanning, or static and dynamic analysis of software to identify vulnerabilities. However, when known vulnerabilities are identified, developers complete a punch list before publishing new features. Security needs to avoid slowing down developers. Alkemist is a fast transform that takes seconds to apply and doesn’t slow down developers.
- Legacy Security Measures – yes, forcing code review after you compiled code is a legacy mindset. Why not assess code when a developer is actually doing work? Security should address this broad problem set with novel approaches that are easy to apply. Alkemist renders inert memory-based attacks whether the vulnerabilities are known or unknown.
- Trough of Disillusionment – the famous hype cycle is by now a predictable pattern for technology adoption. The interesting part is how long a technology stays in a particular phase. Perhaps this velocity is correlated to long-term market potential. In this case, though, given the developer effort and legacy security tactics, we need a new model for hardening software and containers to unleash the massive potential of DevSecOps. Enter RunSafe’s Alkemist, which enables easy to deploy security checks without slowing down developers.
Utilizing Alkemist for DevSecOps
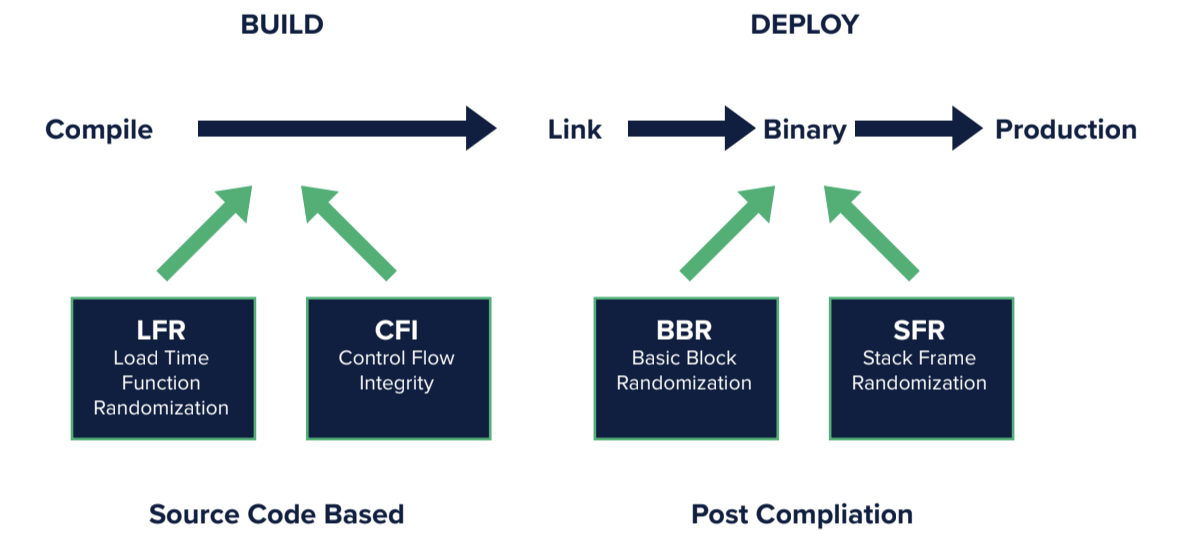
Alkemist applies multiple cyberhardening techniques protecting software binaries from randomizing where functions get loaded into memory thereby providing stack entropy and diversity. Whether it is a buffer overflow, stack or heap attack, or any other memory-based vulnerability hackers exploit, Alkemist reduces attack surfaces so that developers can focus on productivity.
Whether you are working with source code you wish to compile, publishing your own code, or deploying third-party binaries, Alkemist integrates into your CI/CD pipelines in multiple ways. You can add Alkemist into the linking process of your build toolchain or you can add Alkemist at containerization time.
Either way, Alkemist is an easy integration offering automating means to harden compiled code without forcing manual legacy methods into developer’s processes. Having witnessed developers shift from waterfall to agile and now to advance CI/CD processes, it is time to unleash the true potential of DevSecOps. In July, we will be releasing multiple integration points to support your software pipelines. We will offer sample code, how to videos, and support.
At RunSafe Security, we look for ways to economically shift the advantage from attacker to software publisher. By making our advanced security techniques accessible in CI/CD pipelines and containers, developers can add security without manual effort – and disrupt not just the challenges to realizing the DevSecOps potential but also to disrupt hacker economics by eliminating the hackers ability to automate an attack or apply an exploit built in the lab to the fielded device.
To apply RunSafe’s Alkemist in your build and deploy toolchains, please visit www.RunSafeSecurity.com/DevSecOps.