Identify Risk | Protect Code | Monitor Software
RunSafe Security Platform
The RunSafe Security Platform is Trusted By








RunSafe in Action
See why RunSafe Security is the chosen exploit prevention solution for developers and security teams alike — and what it can do for your team.
$2.08M
Saved per year
Average savings customers realized
based on risk reduction.
50%
Increase
Average increase in automated
mitigation by customers.
90%
Reduction
zero-day exposure.
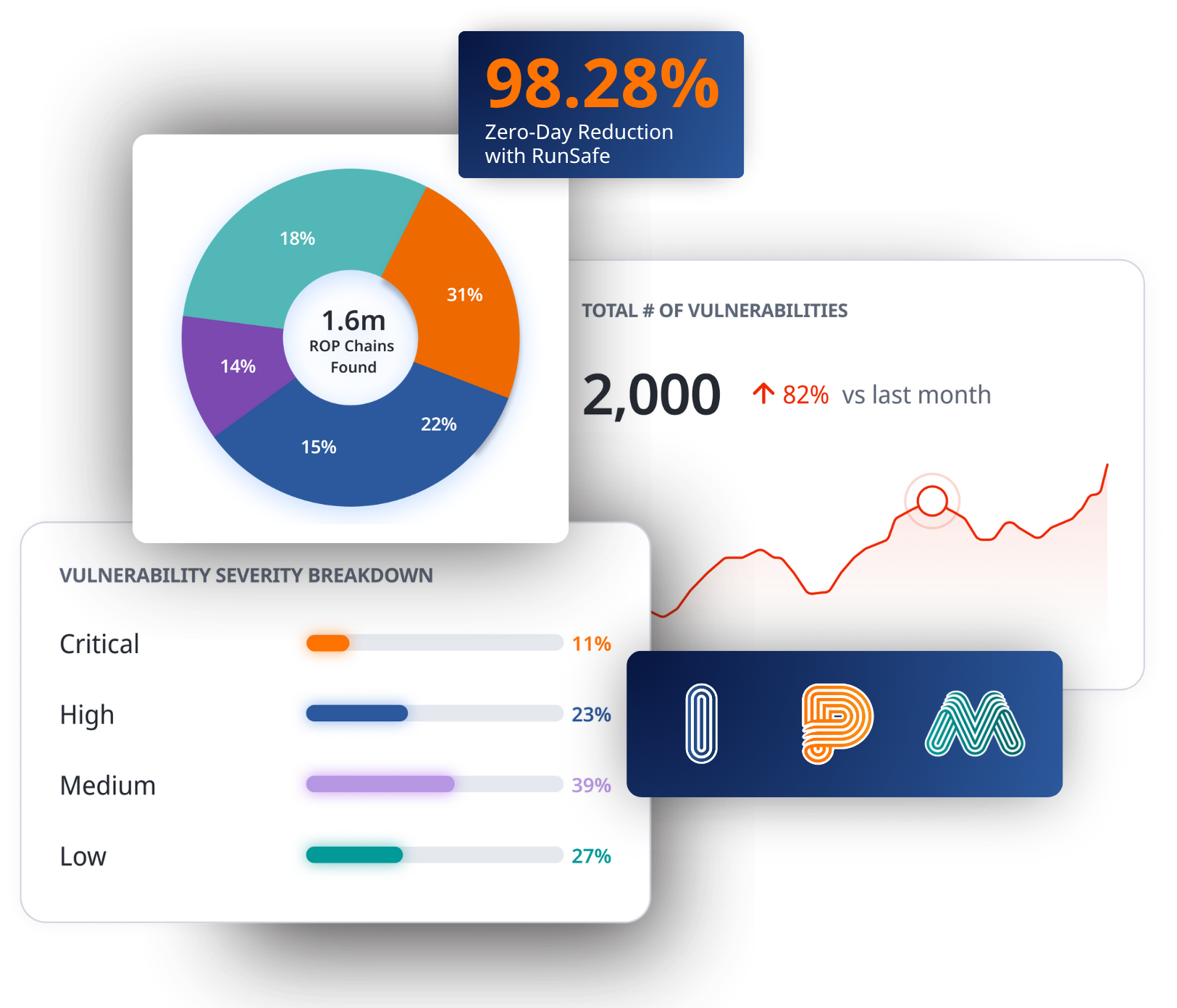
Automated Cybersecurity Protection from Source to Runtime
The RunSafe Security Platform offers comprehensive, modular cybersecurity solutions for embedded systems providing layered protection from software build time to runtime monitoring.
RunSafe provides full visibility into your software’s components by generating a build-time Software Bill of Materials (SBOM). This reveals all software dependencies, identifies vulnerabilities, and quantifies risks, offering actionable insights to reduce exploit paths and enhance your security posture from the start of the development lifecycle.
At runtime, RunSafe applies unique memory relocation techniques to prevent memory-based vulnerabilities from being exploited. This seamless protection requires no code rewrites, ensuring your software remains secure without impacting performance or disrupting development workflows.
Once deployed, RunSafe monitors runtime crash events, distinguishing between bugs and attacks. This ensures continuous protection and provides valuable diagnostic data without affecting system performance, maintaining operational resilience across industries.
Streamline Security and Reduce Cyber Risk with The RunSafe Security Platform
Automated Vulnerability Mitigation
Protect your software effortlessly without requiring developers to re-write existing code.
No Code Rewrites Required
Memory-based vulnerability protection without the need for costly and time-consuming code rewrites. This ensures secure software deployments without disrupting development workflows or system performance.
Reduced Cyberattack Risk
Implement robust protections seamlessly without altering the established behaviors of your systems.
Seamless Cybersecurity for Software Resilience and Efficiency
Protect your software from the most exploited and devastating vulnerabilities, seamlessly integrating across build and deploy toolchains without causing developer friction to achieve resilience, peace of mind, and a competitive edge. RunSafe helps organizations save significant development time, reduce the costly burden of rewriting code, mitigate the high financial risk of cyberattacks, and accelerate new product development by minimizing patching efforts. These operational savings and risk reductions lead to increased innovation and efficiency across the software lifecycle.
Scalable Cybersecurity Solutions with the RunSafe Security Platform
The RunSafe Security Platform offers unmatched flexibility by allowing organizations to adopt the Identify, Protect, and Monitor modules individually or in combination. This enables tailored cybersecurity strategies that scale as your needs grow. This modular approach ensures that organizations can focus on addressing specific vulnerabilities or build comprehensive protection across their entire product line.
Identify Risk
RunSafe Identify
RunSafe Security provides comprehensive cybersecurity solutions for embedded systems by generating build-time Software Bill of Materials (SBOMs), identifying known vulnerabilities present in software, assessing risks from unknown zero days, and quantifying risk reductions.
By offering insights into software components, vulnerabilities and effective mitigation strategies, RunSafe empowers organizations to enhance the resilience of their critical infrastructure against evolving cyber threats
Comprehensive SBOM Generation
RunSafe provides detailed build-time Software Bills of Materials (SBOMs) for embedded systems. An SBOM is a formal record containing the details and supply chain relationships of various components used in building software.
This transparency is crucial for identifying and managing potential risks associated with third-party components, ensuring compliance with regulatory standards, and maintaining a secure software supply chain.
Identify and Quantify Vulnerabilties
RunSafe’s solution includes advanced tools for assessing vulnerabilities within embedded systems. By identifying weaknesses in libraries, components, and packages, RunSafe enables organizations to understand their security posture better.
This proactive approach helps prevent potential exploits by addressing vulnerabilities before they can be targeted by attackers.
Quantify and Score Risk
RunSafe minimizes the attack surface of embedded systems. This involves reducing the number of potential entry points for attackers.
By quantifying your risk reductions, organizations can prioritize their security efforts and measure the effectiveness of their security strategies. This process not only enhances overall security but also helps in demonstrating compliance and governance to stakeholders.
Unique Memory Relocation
RunSafe mitigates cyber exploits by dynamically relocating software functions in memory every time the software is loaded. This process, known as Load-time Function Randomization, ensures that each instance of the software has a unique memory layout, making it extremely difficult for attackers to predict the location of specific functions.
This proactive security measure effectively neutralizes common exploit techniques such as Return-Oriented Programming (ROP) and buffer overflow attacks.
Protect Without Code Rewrites
One key benefit of the RunSafe Protect solution is that it preserves system performance and functionality. The load-time randomization process does not modify the original software code, ensuring no impact on the software’s operational efficiency.
This approach allows organizations to enhance security without sacrificing performance or disrupting existing workflows.
Protect Code
RunSafe Protect
RunSafe Security mitigates cyber exploits by relocating software functions in memory every time the software is run, resulting in a unique memory layout, preventing attackers from exploiting memory-based vulnerabilities.
This approach maintains system performance and functionality without modifying the original software.
Protect Code
RunSafe Protect
RunSafe Security mitigates cyber exploits by relocating software functions in memory every time the software is run, resulting in a unique memory layout, preventing attackers from exploiting memory-based vulnerabilities.
This approach maintains system performance and functionality without modifying the original software.
Unique Memory Relocation
RunSafe mitigates cyber exploits by dynamically relocating software functions in memory every time the software is loaded. This process, known as load-time function randomization, ensures that each instance of the software has a unique memory layout, making it extremely difficult for attackers to predict the location of specific functions.
This proactive security measure effectively neutralizes common exploit techniques such as Return-Oriented Programming (ROP) and buffer overflow attacks.
Protect Without Code Rewrites
One key benefit of the RunSafe Protect solution is that it preserves system performance and functionality. The load-time randomization process does not modify the original software code, ensuring no impact on the software’s operational efficiency.
This approach allows organizations to enhance security without sacrificing performance or disrupting existing workflows.
Monitor Software
RunSafe Monitor
RunSafe Security monitors software looking for indicators of compromise and attack and identifying code quality issues based on software crash events.
This capability enables precise triage, minimizing time and effort wasted on false positives. RunSafe’s passive monitoring listens for software crashes, collecting data on stability, reliability, and potential vulnerabilities.
When a crash occurs, this data is swiftly sent to security operations teams or developers for accurate and efficient triage, enhancing overall software security and resilience.
Runtime Monitoring
RunSafe monitors software at runtime, collecting detailed crash data to distinguish between bugs and potential attacks.
This crash data collection allows for immediate identification of issues, ensuring that vulnerabilities are swiftly addressed before they can be exploited.
Crash Identification
RunSafe implements passive monitoring to listen for software crashes. This passive approach collects valuable data on software stability, reliability, and potential vulnerabilities, providing a comprehensive overview of the software’s health and security posture.
Proactive Incident Response
When a crash occurs, RunSafe swiftly directs the collected data to incident response teams. This timely and accurate data enables quick and effective triage, ensuring that security issues are resolved promptly and minimizing the impact on software operations.
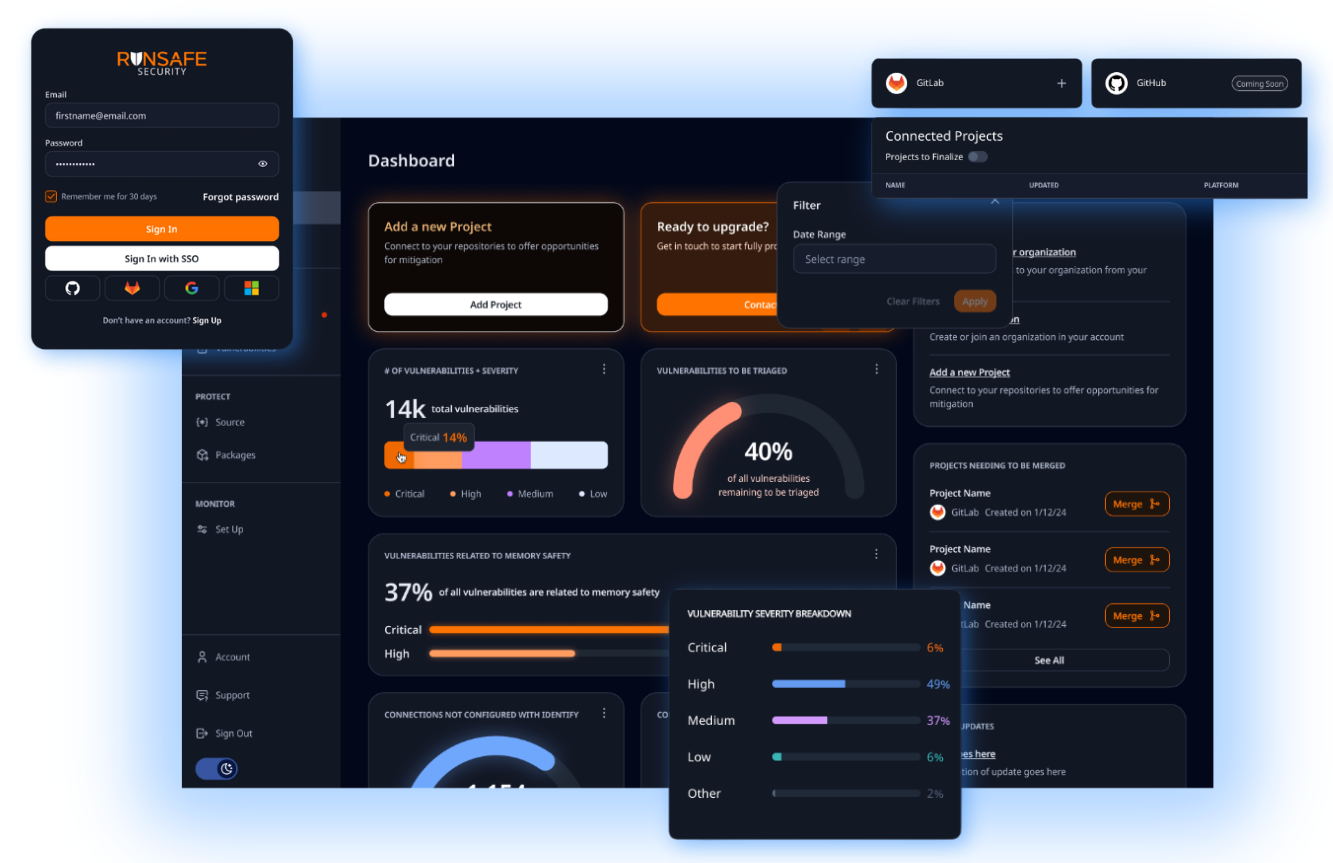
Reduce Operational Costs with Automated Cybersecurity
The RunSafe Security Platform reduces operational costs by automating security processes through its Identify, Protect, and Monitor modules. The Identify module generates SBOMs at build time, providing visibility into software components and automating vulnerability identification, saving labor costs. RunSafe Protect eliminates memory-based vulnerabilities at runtime, avoiding costly code rewrites and ensuring system performance is unaffected. RunSafe Monitor tracks crash events, distinguishing between bugs and attacks, which minimizes downtime and reduces the cost of incident response. Together, these features streamline security efforts and improve operational efficiency for embedded systems.

Why Choose The RunSafe Security Platform?
20-30%
Labor Hours Saved on Development Works
RunSafe prevents system shutdowns by securing vulnerabilities before an attack. With RunSafe’s automated security protection, vulnerability identification and remediation become part of the build process, freeing up developers to focus on new feature development.1
UP TO $250,000
Saved per Vulnerability
UP TO $3 MILLION
Saved in Potential Breaches
UP TO $20 MILLION
Saved in Avoiding Regulatory Fines
$100,000 PER YEAR
Saved in Opertational Costs
UP TO $5 MILLION
In Increased Revenue Opportunities
Achieve Security and Cost Efficiency with RunSafe Security Platform
The RunSafe Security Platform’s comprehensive security solutions not only protects organizations from costly cyberattacks and regulatory fines but also offer significant cost savings by reducing labor, downtime, and remediation expenses.
By automating security processes, enhancing operational efficiency, and maintaining compliance, RunSafe helps organizations realize long-term financial benefits while maintaining a strong competitive edge.





