Across the Department of Defense, software factories have become the mechanism for software modernization. From the AirForce’s Platform 1 to the Navy’s Overmatch Software Armory, software factories use DevSecOps principles to continuously and rapidly deliver secure next-gen systems and capabilities.
But as development speeds increase, securing software at the same pace becomes a challenge. Security often becomes a bottleneck in the delivery pipeline, introducing delays that prevent new technology from making it quickly into the field. Adversaries, however, don’t wait.
This is where Runtime Application Self Protection (RASP) enters the picture. RASP is a powerful addition to existing CI/CD pipelines, offering protections from build time to runtime to increase the cyber resiliency of military systems without sacrificing speed.
Applying RASP in the DoD Software Factory
Imagine trying to infiltrate a building where not just the entrances but the entire floor plan completely changes every time you enter — that’s what attackers face when targeting applications protected by RASP.
RASP is a security technology that operates within software applications to detect and block attacks while an application is running. Unlike Address Space Layout Randomization (ASLR), which has been a standard security feature for years, Load-time Function Randomization (LFR) — a form of RASP — provides advanced runtime protection by randomizing individual functions within a program to create a unique memory layout every time the software loads.
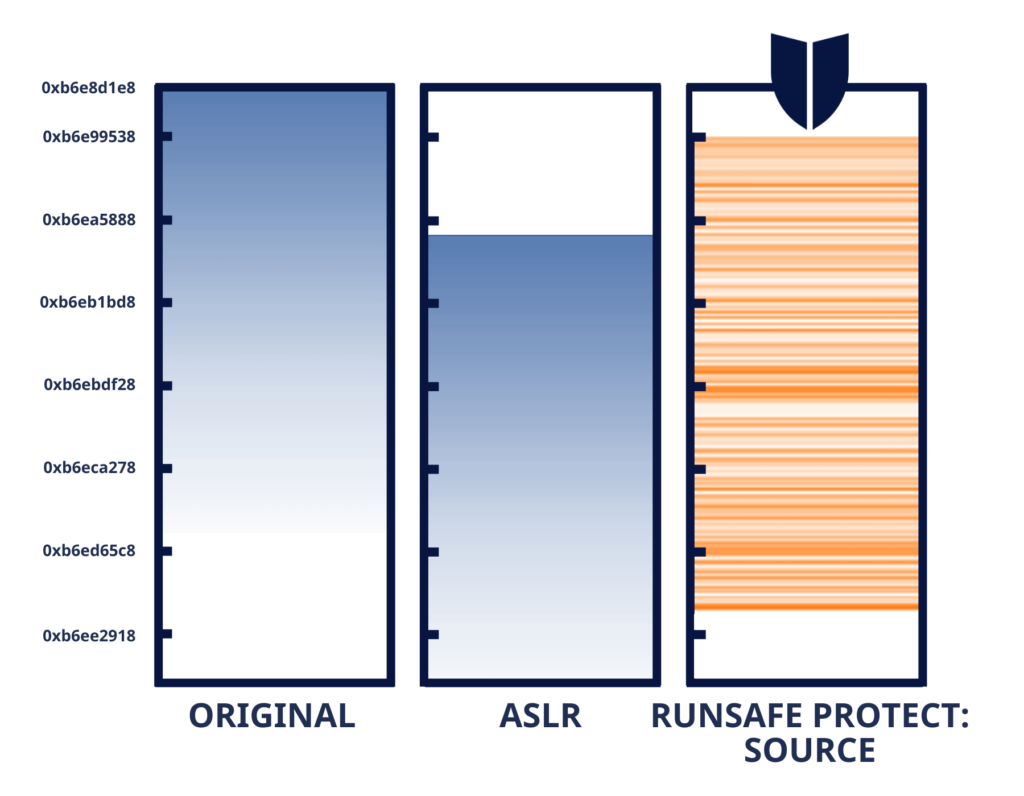
Like in our building analogy, RASP reshuffles the rooms so attackers cannot find a successful path to attack. With RASP, a device or system already deployed in the field can defend against attacks like malware, code injection, backdoors, zero-days, and memory-based vulnerabilities.
Within the context of a software factory, implementing RASP allows for the prevention of exploits at runtime, significantly reducing the severity and risks of unpatched vulnerabilities. When integrated into the CI/CD pipeline, RASP provides continuous protection, whether the software is in development, testing, or deployed in the field, making it possible to confidently ship software faster.
How RASP Complements Source Code Analysis in the Software Factory
While source code analysis tools excel at identifying known vulnerabilities during development, they can’t catch everything. This is where RASP provides crucial complementary protection. RASP operates as an active guardian, preventing exploitation in the field even if the vulnerability wasn’t caught during static analysis.
Runtime protection is particularly valuable for embedded military applications written in C/C++. Memory safety vulnerabilities represent up to 70% of exploitable vulnerabilities in embedded software. In 2022, the National Security Agency (NSA) issued guidance emphasizing the severity of memory safety vulnerabilities, stating that they remain the most readily exploitable category of software flaws. Additionally, MITRE’s Common Weakness Enumeration (CWE) consistently ranks memory corruption vulnerabilities among the top 25 most dangerous software weaknesses.

RASP, by randomizing memory layouts, prevents attackers from exploiting memory safety vulnerabilities. By doing so, RASP protects assets in the field by taking high-severity memory-based vulnerabilities and reducing the risk to not exploitable, eliminating the memory safety threat without requiring massive code changes or impacting performance.
Combining static analysis with RASP strengthens the software factory, addressing issues early on in the development process while also having a layer of defense at runtime that actively protects against both known vulnerabilities and zero days targeting memory-based vulnerabilities.
Real-World Implementations: RASP in Action
RunSafe Security’s Identify and Protect solutions have been deployed with success across multiple DoD programs. Software teams are using RunSafe’s automated runtime exploit prevention solution to improve the cyber resiliency of weapon systems.
- RunSafe Identify: Generate an SBOM and identify vulnerabilities
- RunSafe Protect: Deploy RASP to prevent the exploitation of memory-based vulnerabilities in C/C++ code
What makes RunSafe’s approach particularly valuable in defense contexts is its operational flexibility:
- Operates entirely on-premises
- Requires no network connectivity
- Seamlessly integrates with existing CI/CD workflows
- Maintains compatibility with DoD cloud environments
- Adds minimal performance overhead (just 1%)
- Provides an alternative to rewriting C/C++ code, saving time and costs
Perhaps most importantly, RunSafe’s implementation doesn’t overcomplicate the DevSecOps process. Once set up, it requires minimal maintenance while providing continuous protection
Looking Forward: The Strategic Advantage
For defense organizations leaning into the software factory concept to modernize their DevSecOps practices, RASP represents a strategic opportunity. RASP offers immediate protection while maintaining development velocity. It’s a force multiplier that enhances existing security tools while supporting the mission-critical need for rapid software delivery.





