Critical infrastructure today is powered by software. The need to secure millions of lines of code in embedded systems deployed in ICS/OT environments, the automotive industry, defense, and more has never been more urgent.
Embedded systems in these industries often run on legacy devices and have lengthy lifespans, making patching and regular security scanning and vulnerability identification and mitigation difficult. Runtime Exploit Prevention, also known as Runtime Application Self-Protection (RASP), offers a powerful way to secure these devices in real time, maintaining safety and reliability.
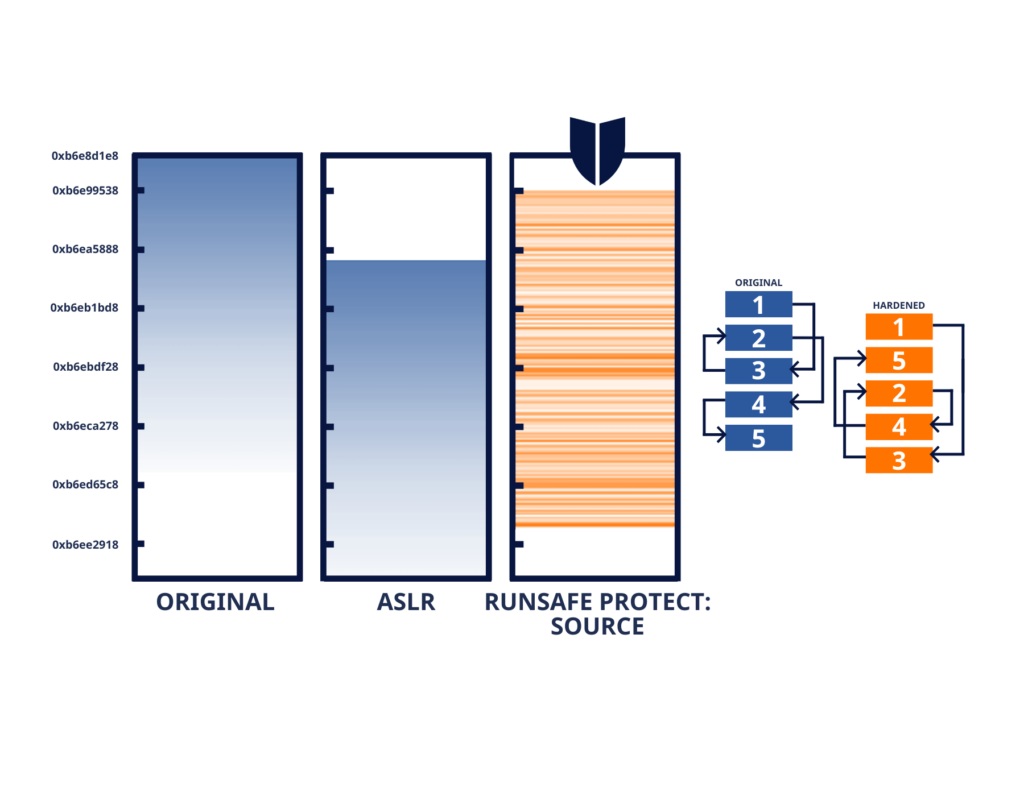
RASP has evolved over the years from traditional Address Space Layout Randomization (ASLR) to more modern solutions like Load-time Function Randomization (LFR), which provides an ideal solution for protecting embedded systems, effectively stopping both known and unknown threats.
What Is Runtime Application Self-Protection (RASP)?
Runtime Exploit Prevention involves measures designed to dynamically neutralize attacks while an application is live. Instead of relying solely on pre-deployment defenses like code reviews or penetration testing, these measures work during execution to detect, block, and adapt to threats in real time.
At the heart of this concept is Runtime Application Self-Protection (RASP). Unlike traditional security methods, RASP directly integrates into the application, constantly monitoring and protecting it from inside. It doesn’t rely on external tools or hardware, making it uniquely positioned to detect suspicious behaviors like unexpected input or exploitative code patterns at runtime.
RASP is particularly effective against memory corruption exploits, such as buffer overflows and Return-Oriented Programming (ROP) attacks, which are challenging to address with conventional security solutions.
Why Is Runtime Exploit Prevention Critical?
Runtime exploit prevention addresses vulnerabilities that emerge after deployment, where traditional preemptive measures fall short. Some of the key reasons RASP has grown in importance include:
- Proactive Defense: It identifies and mitigates attacks as they occur, preventing breaches before they cause damage.
- Adaptability: RASP solutions, such as Load-Time Function Randomization (a RASP technique used in tools like RunSafe Protect), make systems dynamic by altering code layouts during runtime. This frustrates attackers and neutralizes memory-based exploits.
- Reduced Cost and Downtime: By providing built-in defenses, RASP reduces the need for costly patches and emergency fixes after deployment.
Commonly, RASP is used in critical applications where downtime or breaches are unacceptable, including healthcare systems, ICS/OT environments, and military infrastructure.
How Does Runtime Exploit Prevention Protect Embedded Systems?
Embedded systems, like those found in vehicle control systems or industrial control units, are central to modern technology and are incredibly vulnerable. In particular, memory-based vulnerabilities are one of the biggest weaknesses in embedded software.
Runtime exploit prevention, like LFR, secures embedded systems without requiring code rewrites. For example, LFR provides advanced runtime protection by randomizing individual functions within a program to create a unique memory layout every time the software loads, creating a moving target for attackers.
More importantly, LFR can operate even in resource-constrained environments—making it ideal for low-power devices, mission-critical military systems, or embedded vehicle software. RunSafe’s Protect solution, for instance, integrates seamlessly into existing DevSecOps pipelines, ensuring that embedded systems are protected during runtime without sacrificing performance or requiring significant engineering effort.
Vulnerabilities Runtime Exploit Prevention Addresses
Runtime exploit prevention is specifically effective against various high-risk vulnerabilities, including:
- Memory Corruption Exploits: Prevents buffer overflows, heap overflows, and stack-based attacks.
- Return-Oriented Programming (ROP): Disrupts attackers’ ability to exploit pre-existing instructions within an application.
- Use-After-Free Exploits: Mitigates common vulnerabilities by randomizing memory layouts, rendering leaked addresses useless.
- Code Injection Attempts: Detects and blocks malicious instructions before execution.
- Zero-Day Vulnerabilities: Provides protection for memory-based zero days even when the vulnerability is unknown at the time of deployment.
These capabilities are essential at a time when memory safety vulnerabilities account for nearly 70% of all exploitable software flaws, as highlighted by the National Security Agency (NSA).
What Types of RASP Tools Are Available?
The market for runtime application self-protection tools is expanding rapidly. These tools offer unique features tailored to the needs of different industries. Here’s a look at common types of RASP tools:
- Function-Level RASP Solutions: These tools randomize memory layouts of individual functions or processes. For example, RunSafe Protect’s Load-Time Function Randomization (LFR) offers unparalleled memory diversification.
- Behavioral Analysis-Based Tools: Tools like Imperva RASP actively monitor and analyze application behavior, blocking threats based on unusual input patterns or system calls.
- Language-Specific RASP Solutions: Some tools are designed for specific programming languages. For instance, Checkmarx offers RASP capabilities targeted at Java and .NET applications.
- Integrated DevSecOps Platforms: Solutions such as Veracode integrate RASP directly into CI/CD systems, providing protection throughout the development lifecycle.
How RunSafe’s RASP Solution Stands Out
RunSafe Security’s Protect solution takes runtime exploit prevention to the next level. By implementing advanced RASP techniques and innovative Moving Target Defense (MTD) mechanisms, it provides comprehensive protection against memory-based attacks.
Here’s what sets RunSafe apart:
- Function Randomization: RunSafe’s patented LFR technology scrambles memory layouts each time software runs, creating billions of possible configurations. This makes reliable exploitation nearly impossible for malware.
- Seamless Integration: Protect integrates directly into existing DevSecOps workflows, requiring no changes to codebases or build systems.
- Low Overhead: Unlike traditional runtime security tools, Protect has minimal impact on performance—less than 1% overhead in most use cases. This makes it suitable for real-time and embedded systems.
- Broad Applicability: Protect supports an extensive range of platforms, including Linux, Windows, and embedded architectures like ARM. This flexibility makes it ideal for securing applications across industries.
- Resilient to Zero Days: Protect reduces the exploitability of memory-based zero-day vulnerabilities, ensuring applications remain secure even against unknown threats.
RunSafe’s unique focus on runtime memory protection solves one of the biggest risks to embedded software, addressing both known and unknown memory-based vulnerabilities to safeguard critical systems.
Final Thoughts on Adopting Runtime Exploit Prevention
Whether you’re a medical device manufacturer or developing military systems, runtime exploit prevention is an essential layer of defense. RASP represents a shift from reactive to proactive cybersecurity, addressing risk not just at deployment but throughout a device’s lifecycle.
Learn more about RunSafe Protect in our deep dive into the technology that powers it. Get the white paper: Tech Deep Dive: RunSafe Security’s Protect Solution.