Understanding and managing software components is crucial for safeguarding against cybersecurity vulnerabilities. A Software Bill of Materials (SBOM) serves as a comprehensive inventory of all components, libraries, and modules used in software applications. SBOMs help organizations identify and address potential security risks efficiently and transparently.
SBOMs are particularly significant in embedded systems, which are integral to numerous critical applications, from medical devices to industrial control systems. Because embedded systems often incorporate a variety of third-party and open-source components, they are susceptible to hidden vulnerabilities. SBOMs give visibility into these components, allowing developers and software manufacturers to get ahead of risk.
What Is a SBOM?
A Software Bill of Materials is a detailed list of all components, libraries, and modules used in a software application. Think of it as an ingredient list for a recipe, but for software. Each entry in an SBOM provides crucial information about the components, including their origin, version, and any known vulnerabilities. This comprehensive inventory is essential for managing software supply chains and ensuring robust security. SBOMs play a pivotal role in providing transparency and accountability for risk assessment in software development.
Why SBOMs Matter in Embedded Systems
Embedded systems are specialized computing systems that perform dedicated functions within larger mechanical or electrical systems. Found in devices ranging from medical equipment and industrial controls to consumer electronics and automotive systems, embedded systems are integral to critical infrastructure. These systems are designed for specific tasks, often operating in real-time and requiring high reliability and stability.
Given their crucial roles in sectors such as healthcare, energy, transportation, and manufacturing, embedded systems are often targets for cyber threats. Their integration into critical infrastructure means that any vulnerability can have far-reaching and potentially catastrophic consequences.
SBOM Example: Key Components for Embedded Systems
For embedded systems, having a comprehensive and accurate SBOM is essential. Below are the key components:
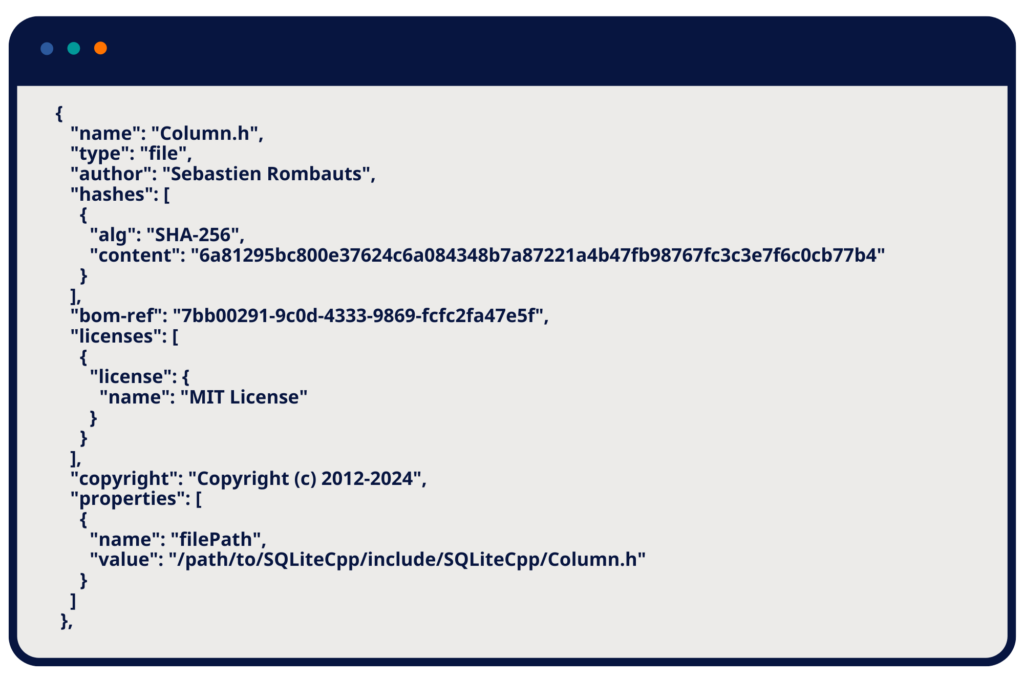
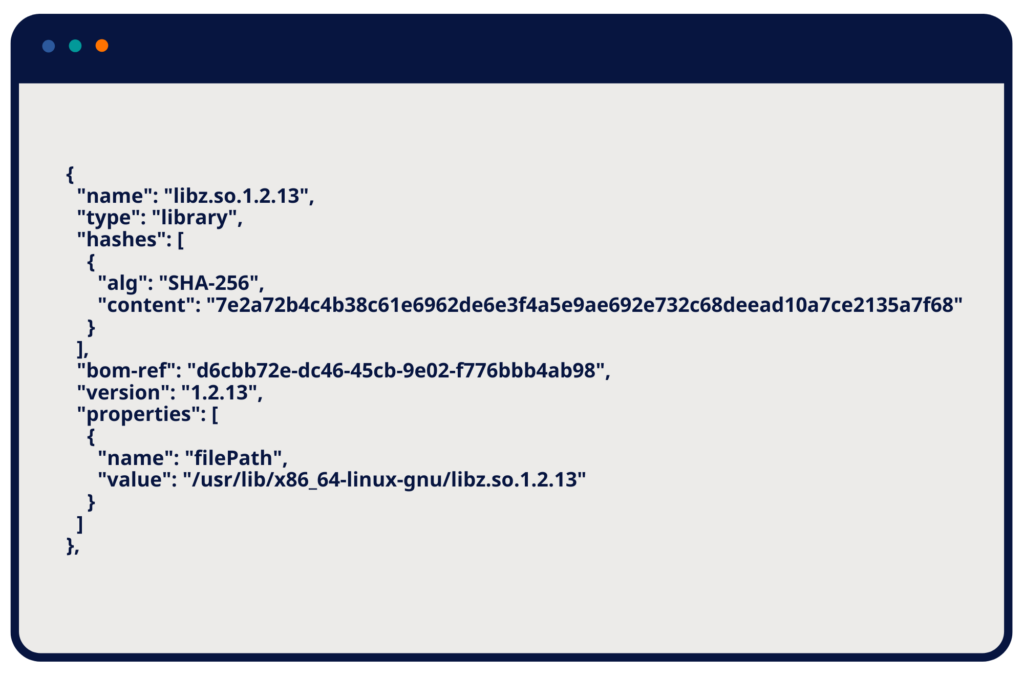
- Component name: Each software component is listed by its name. This includes libraries, frameworks, and modules. Example: libssl.so.1.1.
- Version information: The specific version of each component is noted. Example: Version 1.1.1g.
- Supplier Information: Details about the vendor or author of the component. Example: OpenSSL Software Foundation.
- Licensing information: The type of license governing the use of the component. This ensures compliance with legal and regulatory requirements. Example: Apache License 2.0.
- Component hash: A cryptographic hash (e.g., SHA-256) that verifies the integrity of the component. Example: 3c1a84ab7f23cd8c1e8f4564a2e4f45b234a7d8e92b6ec34b8b9d5c6e8f01234.
- Dependency relationships: Information on how components depend on each other. Example: libssl.so.1.1 -> libcrypto.so.1.1.
- Security and vulnerability information: Known vulnerabilities associated with the components. Example: CVE-2020-1971.
An SBOM for an embedded system might include a line like the following example:
File Component Example from a Build-Time SBOM
Library Component Example from a Build-Time SBOM
GET FULL VISIBILITY INTO THE COMPONENTS IN YOUR EMBEDDED SYSTEMS [START FREE TRIAL]
Creating an SBOM: Top Security Tools and Best Practices
Common tools for generating SBOMs in embedded systems include:
- Syft: A CLI tool for creating SBOMs from container images and filesystems.
- CycloneDX: A lightweight SBOM standard.
- SPDX: An open standard with tools like SPDX-Tools for SBOM creation and validation.
- Black Duck: A comprehensive open-source management tool with SBOM generation features.
- FOSSA: An automated tool for open-source compliance, security, and SBOM generation.
- Endor Labs: Goes beyond traditional SCA tools by not relying solely on package manifests, addressing transitive dependencies effectively.
- RunSafe Security: Generates SBOMs as part of the build process with unique capabilities for C/C++ languages
Best practices for creating effective and comprehensive SBOMs include the following:
- Integrate automated tools into the CI/CD pipeline for consistent SBOM updates.
- List all software components, including dependencies, versions, licenses, and suppliers.
- Regularly update SBOMs to reflect new components and patches.
- Use cryptographic hashes to verify component integrity.
- Include known vulnerabilities (e.g., CVEs) for proactive security management.
- Ensure license compliance for all components.
- Maintain clear documentation and transparency throughout the supply chain.
Using SBOMs to Enhance Embedded Systems Security
Using SBOMs is a proactive strategy for bolstering the security of embedded systems. SBOMs provide a detailed inventory of all software components, including versions and dependencies. This transparency allows security teams to track known vulnerabilities (e.g., CVEs) associated with each component.
By regularly updating SBOMs and cross-referencing them with vulnerability databases, organizations can quickly identify and address security weaknesses. Automated tools can alert teams to newly discovered vulnerabilities, facilitating prompt patching and mitigation efforts.
By analyzing the SBOM, organizations can prioritize security efforts based on the potential impact of each vulnerability.
Challenges and Solutions in SBOM Implementation
Integrating SBOMs into embedded systems faces challenges like managing numerous third-party components, limited processing power, and memory constraints. Tracking component versions and ensuring consistency across environments is difficult, and the lack of industry-wide standards can cause compatibility issues.
Practical solutions include using automated SBOM tools like SPDX and CycloneDX, incorporating SBOM generation into CI/CD workflows, adopting standardized SBOM formats, conducting regular audits, and training development teams on best practices for SBOM creation and maintenance. These strategies help streamline dependency tracking, maintain accuracy, and ensure compatibility in managing software component inventories.
The Future of SBOMs in Embedded Systems
The future of SBOMs in embedded systems is set to transform significantly, spurred by emerging trends, government directives, and technological advancements aiming to bolster security and operational efficiency.
Recent federal directives have underscored the importance of SBOMs in ensuring software security, aligning with NIST Guidance and emphasizing secure software development practices. Automation tools and AI are poised to play an increasingly vital role in SBOM generation, streamlining vulnerability identification and risk prediction.
Future SBOMs are likely to integrate real-time monitoring, machine learning, and big data analytics to enhance integrity and authenticity. Standardization efforts and regulatory recognition are expected to drive broader adoption and interoperability, integrating SBOMs into DevSecOps practices and facilitating early vulnerability detection.
How SBOMs Improve Software Security
SBOMs are essential for securing embedded systems, providing transparency, vulnerability tracking, and risk assessment. As embedded systems play critical roles in various industries, the adoption of SBOM practices becomes paramount for maintaining robust security postures. By integrating SBOMs into your cybersecurity strategy, you can proactively address potential threats and enhance the resilience of your systems.