When maintaining embedded systems, patching is one of the most resource-intensive challenges for software developers and security teams. Between developing patches, testing, deploying them, and working to maintain system uptime, patching is a big drain on resources. It also eats up time. It can take months on average for patches to be released by vendors and deployed, leaving systems vulnerable to exploitation, which has a direct impact on operational and business continuity.
Despite these challenges, applying patches quickly remains an industry-best practice for keeping software and embedded devices secure. However, relying solely on scanning and patching is proving inadequate for modern security needs. The challenge now for software manufacturers is finding ways to improve the patching process to proactively and strategically defend embedded systems.
This blog will explore:
- When organizations should prioritize patching
- How reachability analysis is evolving but remains limited
- The role of runtime protection solutions in reducing vulnerability severity
- The tangible benefits of runtime security for developers and software manufacturers
When Should You Apply a Patch?
Severity remains a top qualifier when deciding which vulnerabilities to patch. Most organizations focus on critical and high vulnerabilities first, moving on to medium and low severities only when practical. For publicly released software, external-facing systems take precedence, but it’s important to remember that internal tools with access to sensitive data or proprietary information shouldn’t be ignored either.
For example:
- Critical vulnerabilities affecting widespread functionality or enabling remote code execution often warrant immediate action.
- Medium or low vulnerabilities might be deprioritized but can still pose risks depending on their reachability or the systems they impact.
Reachability Analysis as a Future Tool
One potential solution to this prioritization problem is reachability analysis, which assesses whether a specific vulnerability is exploitable in a given system. While some tools already provide reachability analysis for languages like JavaScript and Python, their accuracy and adoption remain inconsistent. Unfortunately, such solutions are not yet widely available for languages like C and C++, which underpin many embedded and legacy systems.
This is where runtime security solutions come into play.
Reducing Vulnerability Severity with Runtime Security Solutions
Runtime security solutions provide an innovative approach to mitigating vulnerabilities without waiting for patch cycles. By securing software in real-time, these tools reduce the operational urgency to patch, buying teams valuable time while still maintaining protection against exploits.
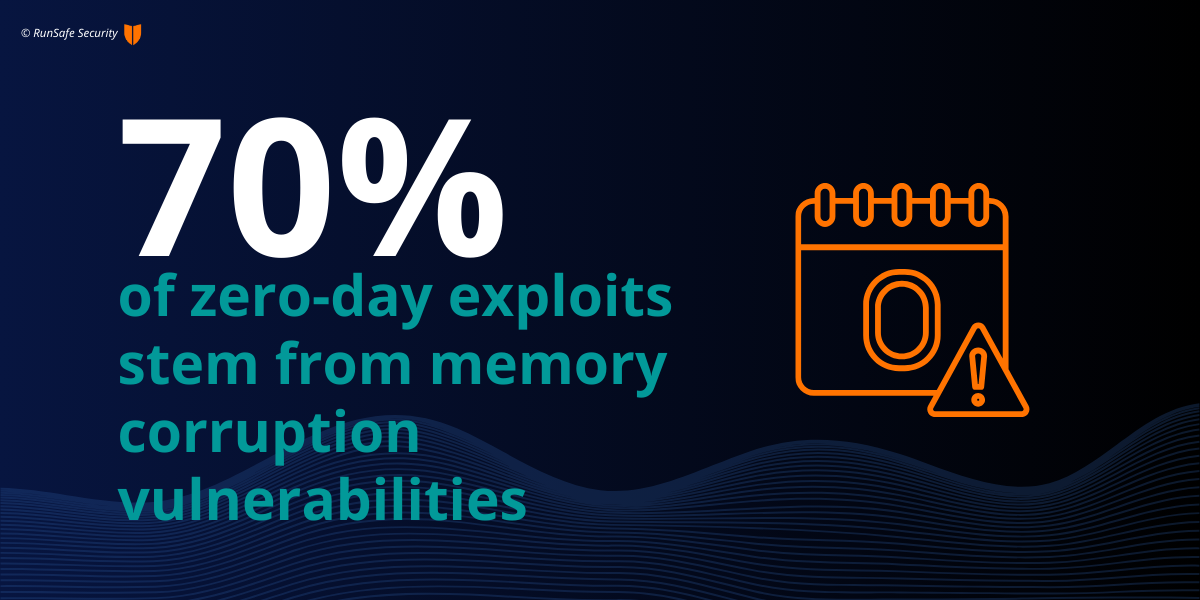
A key benefit of runtime solutions is it allows organizations to reduce the severity score of common vulnerabilities found across embedded software. For example, a significant number of embedded systems are written in memory-unsafe languages such as C and C++. These systems are uniquely vulnerable to memory-based vulnerabilities, including buffer overflows and use-after-free errors. Alarmingly, 70% of zero-day exploits stem from memory corruption vulnerabilities, leading to severe repercussions like remote code execution.
By eliminating memory-based vulnerability exploitability, runtime solutions offer immediate security benefits to embedded systems, including the ability to lower vulnerability severity and reduce the need to patch.
How RunSafe Protect Reduces Vulnerability Severity
Solutions like RunSafe Protect directly mitigate memory-based vulnerabilities at runtime. By doing so, developers can reduce the severity of vulnerabilities based on their Common Vulnerability Scoring System (CVSS) rating. For instance:
- Using the CVSS v4.0 calculator, developers can adjust parameters such as availability and integrity to “none” for memory-based CVEs mitigated by RunSafe Protect.
- This adjustment effectively reduces the CVSS score to zero, making the vulnerability non-exploitable.
Critically, this mitigation doesn’t replace patching—it complements it. Teams should continue to scan for vulnerabilities, adjust severity scores based on runtime mitigations, and follow existing risk management guidelines. However, runtime security minimizes the urgency associated with patching, ensuring systems remain defended while developers work on longer-term fixes.
The Broader Benefits of Runtime Security Solutions
Implementing runtime security doesn’t just enhance protection—it also delivers measurable benefits to both development teams and overall organizational efficiency. Here’s how:
Improved Operations and Smoother Patch Schedules
With runtime protections in place, patching schedules can be aligned with planned updates, reducing the need for emergency patches that disrupt workflows. Developers gain more time to properly develop, test, and deploy patches without compromising security.
Saving Developer Resources
Patching is a time-intensive process. By ensuring vulnerabilities are mitigated at runtime, runtime solutions free up developers to focus on their core tasks—writing new code and shipping innovative products. This operational efficiency directly enhances the organization’s productivity.
Enhanced Customer and Stakeholder Confidence
When vulnerabilities are mitigated at runtime, organizations can issue security advisories that reassure customers and partners. The ability to state that systems are already protected thanks to runtime protections strengthens confidence in your processes and builds trust with stakeholders.
Economic Advantages
The financial benefits are clear:
- Lower risk of costly breaches or operational downtime
- Smoother allocation of development and security resources
- Greater ability to prioritize business growth over firefighting vulnerabilities
By reducing workload, mitigating risk, and streamlining operations, runtime security ensures organizations achieve both technical and business goals.
Practical Steps for Smooth Patch Management
Runtime security solutions like RunSafe Protect offer organizations breathing room. But patching remains an essential element of your cybersecurity strategy. Here are recommended next steps for improving your patch management workflow:
- Adopt a Comprehensive Vulnerability Management Plan: Use tools that perform regular scans, prioritize vulnerabilities by severity, and integrate runtime protections to reduce urgent patches.
- Leverage Runtime Security Solutions: Introduce tools that can instantly mitigate known vulnerability types, especially memory-based vulnerabilities common in critical systems.
- Invest in Reachability Analysis Tools: When available, these tools can help you focus patching efforts on the most exploitable vulnerabilities.
- Regularly Align Security Updates with Operational Schedules: Plan patches during downtime or alongside regular updates to minimize disruption.
By adopting a layered approach to vulnerability management, organizations can keep systems secure without overburdening teams or disrupting day-to-day operations.
Take Control of Your Patch Management Strategy
Patching may remain one of the most difficult tasks in embedded systems, but it doesn’t have to drain resources or derail business priorities. By supplementing traditional scanning and patching processes with runtime security solutions, organizations can reduce vulnerability severity, protect critical systems, and empower development teams to focus on the future. Want to simplify vulnerability identification and automate mitigations?
Explore how the RunSafe Security Platform can reduce the severity of memory-based vulnerabilities and smooth out your patching process.