Identify Software Supply Chain Risk at
Build Time with C/C++ SBOMs
Generate precise and complete Software Bills of Materials for your C/C++ projects at build time. No package manager required.
Get Complete Visibility Into Software Components — Without a Package Manager
RunSafe’s SBOM generation capabilities provide deep visibility into embedded software written in C/C++.
By generating SBOMs at build time, RunSafe captures only the components and libraries in a build for an accurate picture of your embedded software and fewer false positives and negatives.
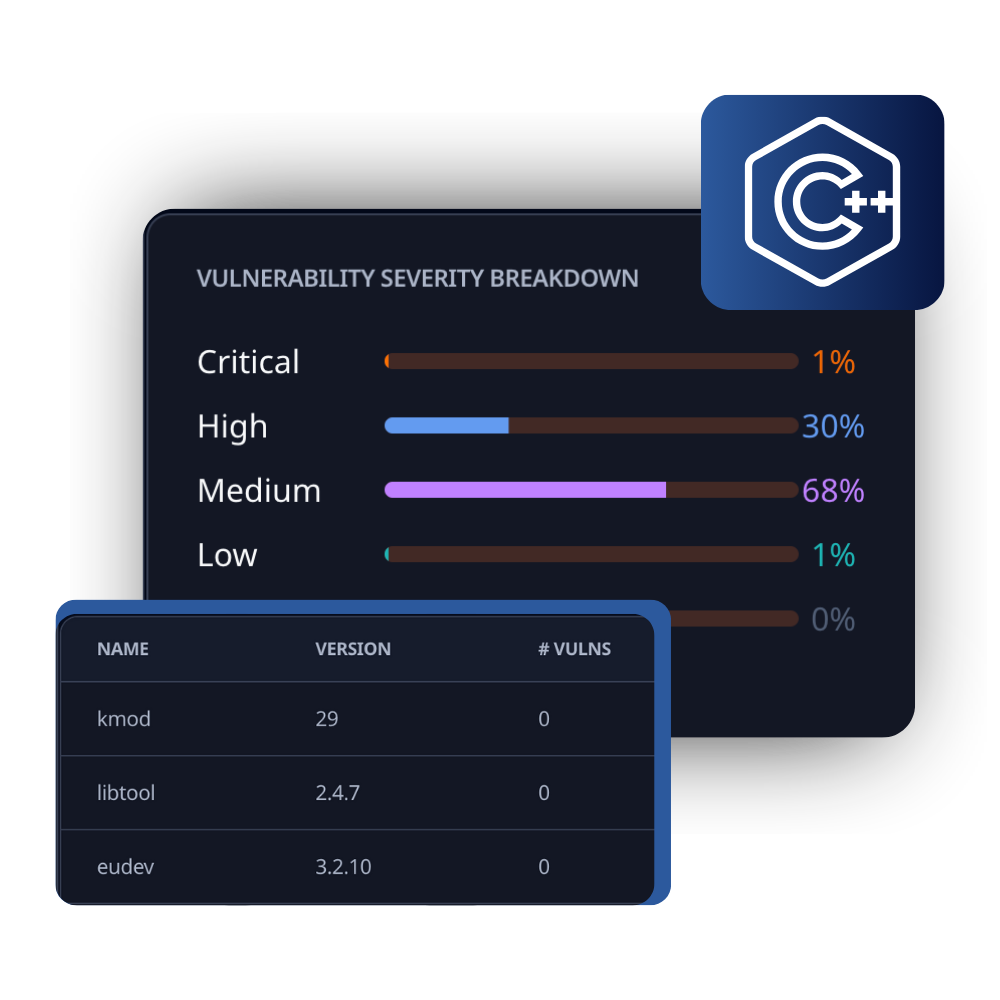
What RunSafe’s C/C++ SBOM Includes
RunSafe generates CycloneDX SBOMs at build-time and includes all mandatory NTIA minimum elements for compatibility with regulatory reporting requirements.
Dependency Discovery
Reports on all opened files to identify dependencies in your C/C++ codebase, including static and dynamic libraries.
- Static and dynamic libraries
- Source, header, and compiled files
- Applications
Vulnerability Assessment
Cross-references discovered components against known vulnerability databases to increase security and reduce software supply chain risk.
- CVE mapping
- CVSS scoring
- Real-time risk identification
License Compliance
Includes provenance information, like supplier, author, and licenses, to meet compliance with legal and organizational requirements.
- Licenses
- Copyrights
- Authors
Seamless Integration and Deployment
Integrates with CI/CD pipelines for automated SBOM generation and continuous security monitoring.
- CI/CD integration
- Automated reporting
- No developer disruption
Reduce Software Supply Chain Risk with Build-Time SBOMs

Meet SBOM Compliance Requirements
Quickly
Identify
Vulnerabilities

Reduce False
Positives & Negatives

Protect Legacy Systems and Real-Time Software
Get 100% Visibility Into Components
How Much Visibility Does RunSafe Provide?
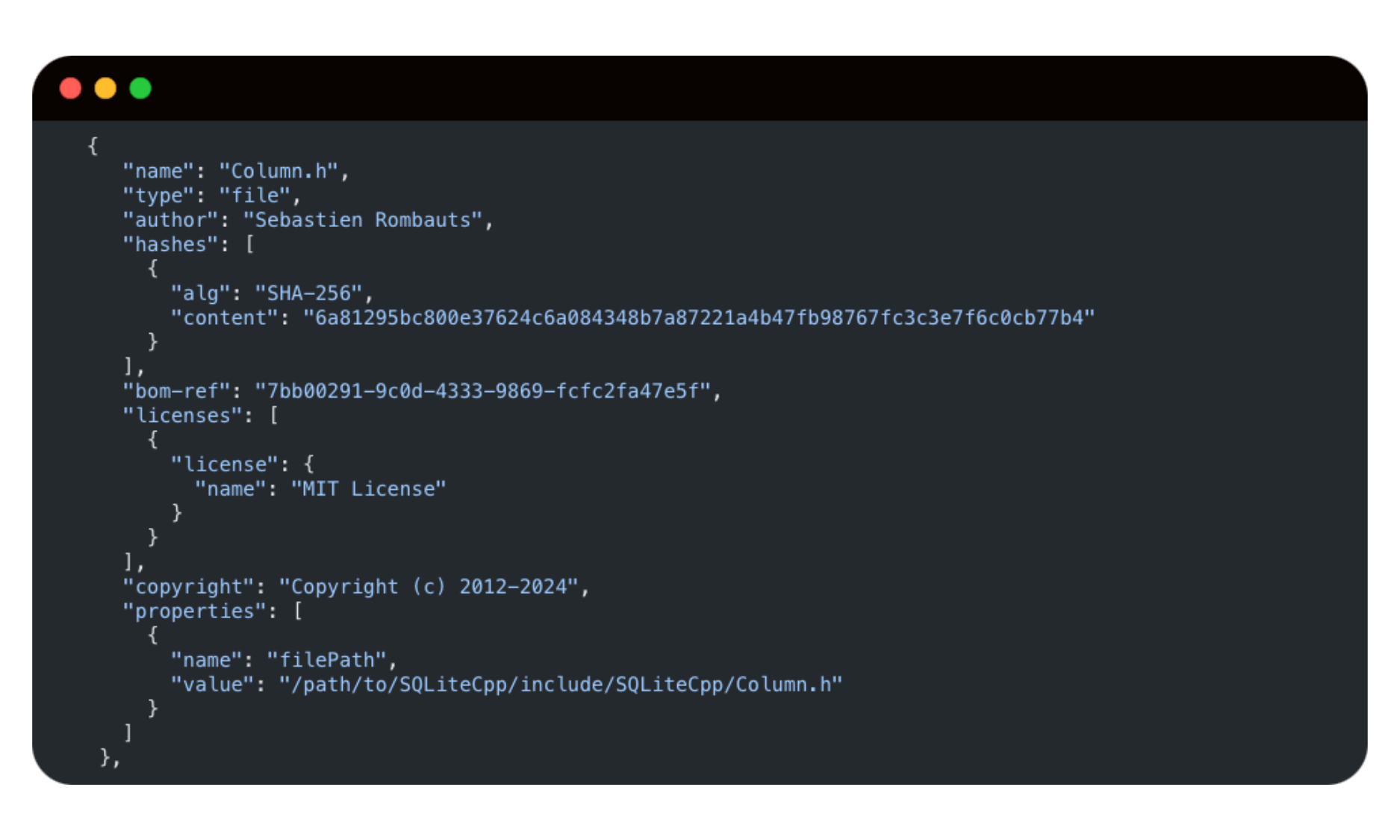
RunSafe reports on only the files that go into the final target, for precise SBOMs with detailed provenance information (authors, copyright, licenses).
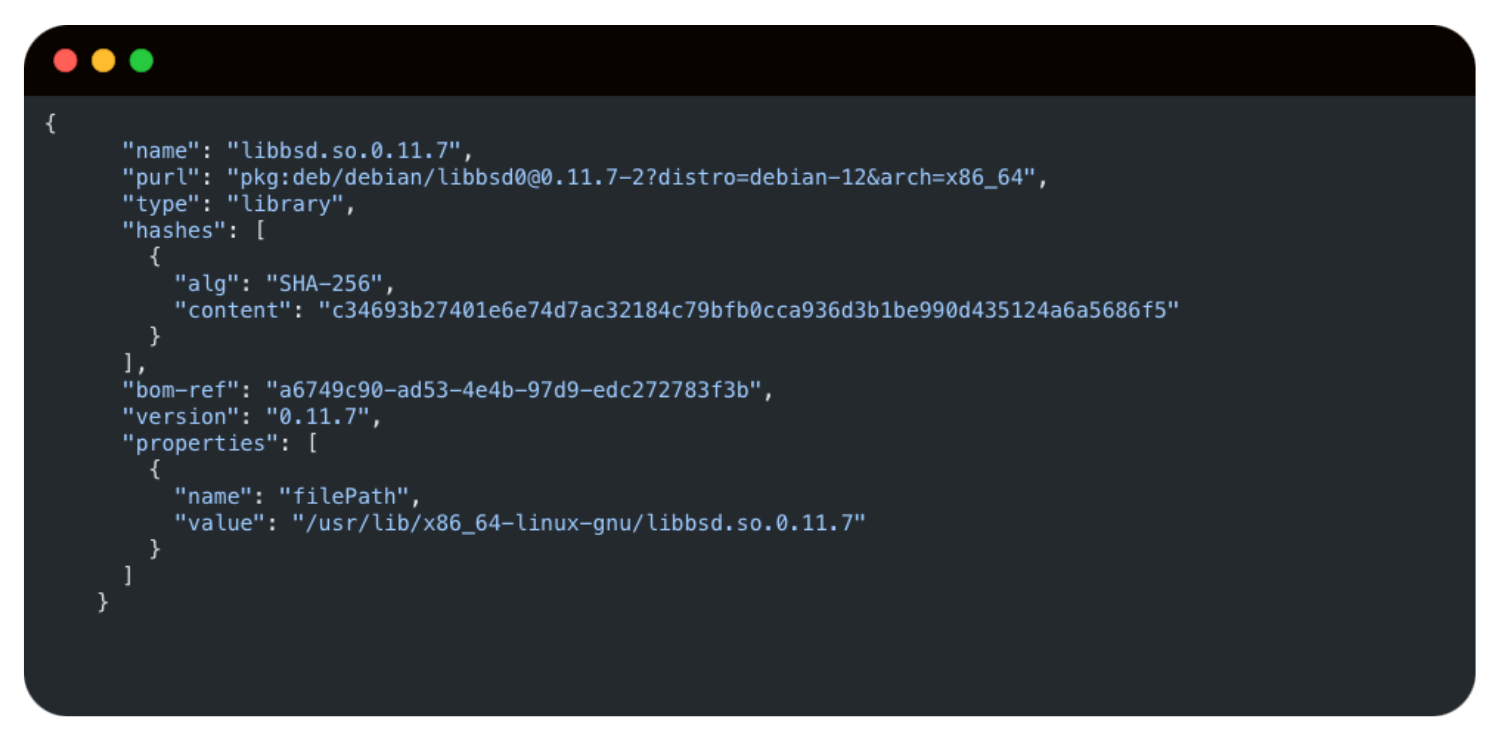
RunSafe’s SBOM captures both static and dynamic libraries, unlike binary-based SBOMs that only report on dynamic libraries.
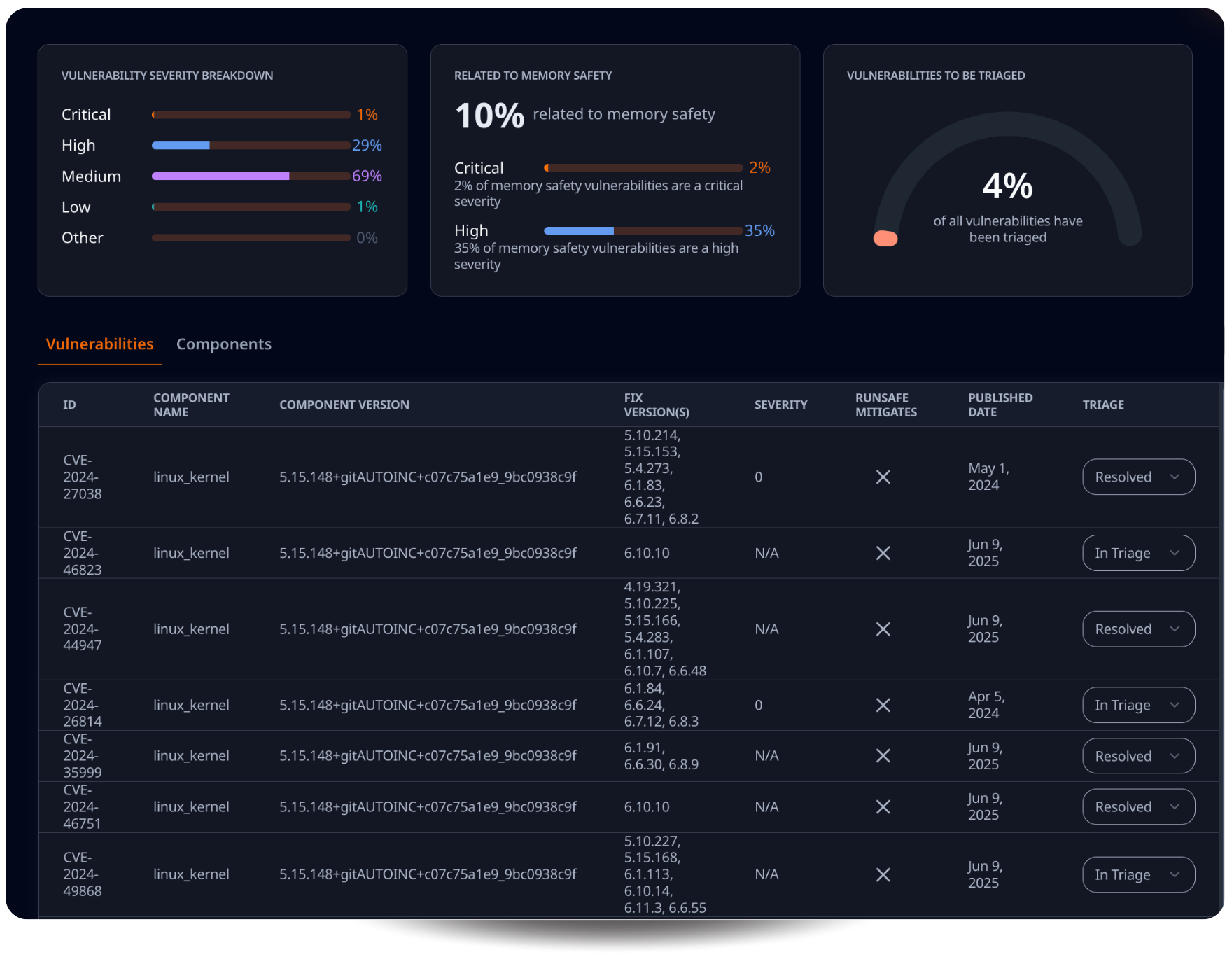
RunSafe identifies vulnerabilities in your software, providing full visibility into your software supply chain and potential threats.
Build-Time SBOMs: Your First Line of Defense in Embedded Software Security
Generate an SBOM for Your C/C++ Application
Get started with build-time SBOM generation and vulnerability identification for your C/C++ projects.