Cybersecurity for C/C++ and Proprietary Software
Protection Without Altering Your Code or Build System
Securing proprietary software is challenging due to its hidden source code, which can both protect against and expose it to vulnerabilities. While this obscurity makes flaws harder for attackers to find, it also means that issues may remain unnoticed and unpatched longer.
SAST and DAST tools have historically struggled to identify vulnerabilities in proprietary code, with studies showing that up to 90% of memory corruption bugs can go undetected. Even with regular patching, systems remain vulnerable to critical attack vectors. RunSafe Security addresses this gap by hardening embedded software at runtime, preventing memory safety exploits without requiring code rewrites or impacting system performance.
“From our perspective, adding RunSafe means we have more opportunity to shrink the attack surface and reduce overall risks for our customers since security is now already built into our product.”
Immediate Protection from Exploitation
Experience robust protection from day one without any changes to your existing codebase.
Performance and Code Integrity
Enhance security without compromising the software’s core functionality or overall performance.
Future-Ready
Defense
Future-proof your software with a forward-thinking solution that evolves with emerging threats and vulnerabilities.
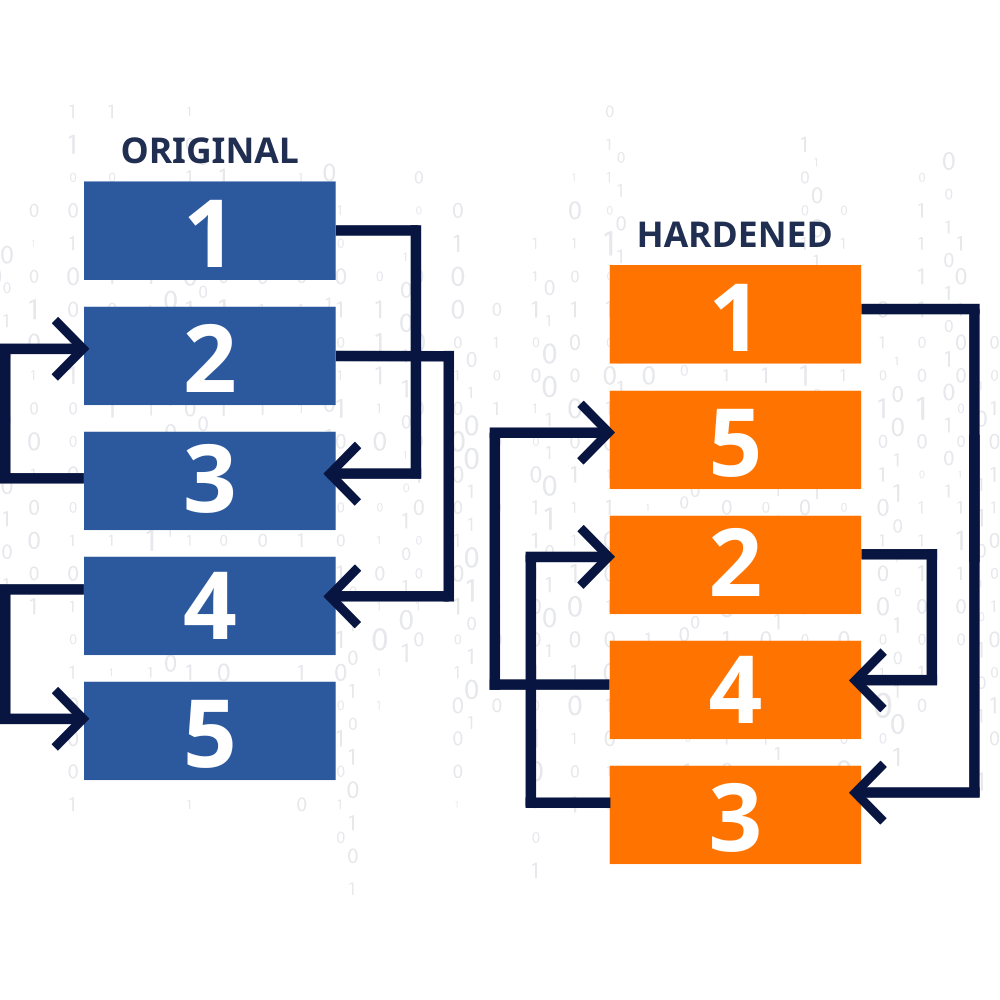
Strengthening Security with Function Randomization and Unique Memory Layouts
RunSafe’s technology ensures that each time your software is loaded, it generates a unique memory layout. This dynamic approach makes it exceedingly difficult for attackers to predict the location of specific functions, neutralizing standard exploit techniques like Return-Oriented Programming (ROP) and buffer overflow attacks.
RunSafe introduces this variability at runtime to significantly enhance the security of your proprietary software. By combining these advanced protections with continuous monitoring, RunSafe provides an adaptive defense that evolves with emerging threats, ensuring comprehensive security for your software. This layer of defense ensures that your software remains resilient and secure throughout its operational life.


Maintaining Robust Security for Proprietary Software with RunSafe Security
RunSafe helps organizations maintain robust product security for proprietary software by integrating protection at build time and ensuring ongoing defense at runtime. RunSafe effectively addresses vulnerabilities before they can be exploited, reducing the need for frequent patches and updates, and minimizing the risk of potential security breaches that could disrupt operations or damage reputations.
This approach aligns with controlled patch management processes, ensuring that updates are stable, effective, and deployed without disrupting operations. This safeguards your systems and fosters trust among stakeholders by demonstrating your commitment to protecting critical infrastructure.
Latest Resources
Navigating Third-Party Software Risk: Best Practices for 2026
Most of the code running in your product probably isn't code you wrote. Open source libraries, vendor SDKs, and firmware components all become part of your attack surface the moment they're compiled into your build. Third-party software risk is the potential for...
The Worst Vulnerabilities of 2025: How Pre-Auth RCE Broke the Perimeter
Across industries, the year’s most damaging vulnerabilities shared the same defining trait: unauthenticated remote code execution (pre-auth RCE) on internet-facing systems. VPNs, firewalls, web frameworks, and even core ERP platforms all fell victim to flaws that...
3 SBOM Generation Methods: Binary vs Build-Time vs Source Code
Your SBOM is only as useful as it is accurate, and the method you use for Software Bill of Materials (SBOM) generation determines the level of accuracy you will receive. SBOM generation method determines whether an SBOM captures what developers declared, what scanners...
Ready to Get Started?
RunSafe protects proprietary software by automatically securing code without requiring rewrites, preventing memory-based vulnerabilities, and maintaining system integrity.


