Enhance Application Security with Software Memory Protection
RunSafe Security offers cutting-edge application security hardening, defending against memory-based attacks and reducing attack surfaces to safeguard your software. Our advanced solutions ensure your applications remain secure, resilient, and protected from emerging threats, providing peace of mind and robust defense.
Protecting Your Software from Build-Time to Runtime Across Industries
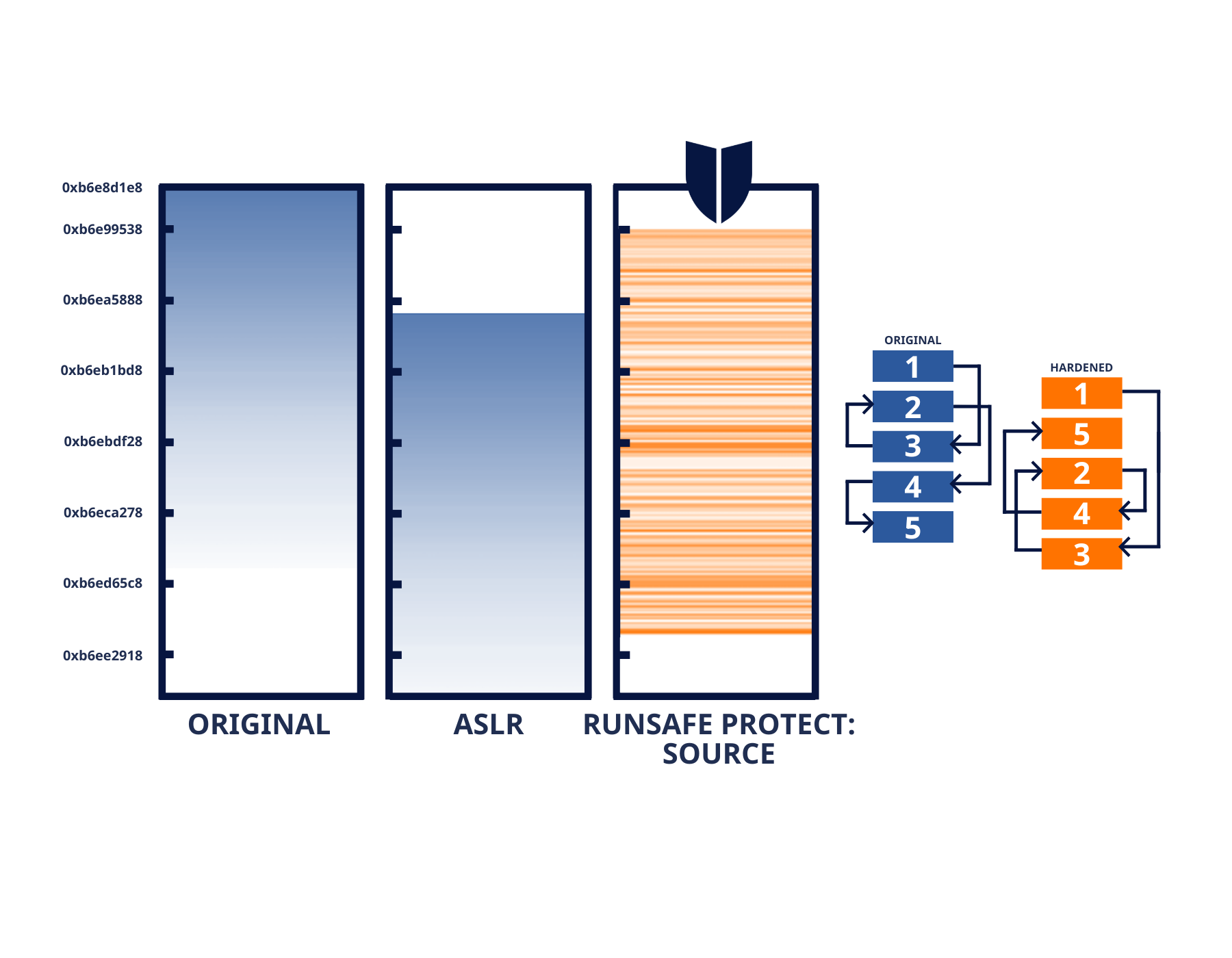
RunSafe’s innovative security technology ensures each binary image is functionally identical but logically unique by applying load-time memory randomization, effectively neutralizing memory-based attacks like buffer overflows and return-oriented programming (ROP). The transformation occurs at the binary level, altering the memory layout without modifying the underlying source code. This proactive measure eliminates the need for constant patching and continuous monitoring, delivering robust and ongoing protection against known and unknown vulnerabilities.
By transforming software binaries during the build process, RunSafe strengthens embedded applications and OT systems by neutralizing exploitable memory vulnerabilities before they can be targeted. This approach not only enhances your security posture but also reduces operational overhead by automating vulnerability mitigation, allowing security teams to focus on higher-level tasks.
“From our perspective, adding RunSafe means we have more opportunity to shrink the attack surface and reduce overall risks for our customers since security is now already built into our product.”
Robust Defense
Fortify your applications against sophisticated threats with RunSafe Security’s advanced solutions, ensuring comprehensive protection and resilience.
Continuous Protection
Maintain robust security from source to runtime with RunSafe Security’s proactive and integrated solutions.
Efficiency Boost
Enhance the efficiency of your security processes with minimal impact on performance, ensuring streamlined protection without compromising speed or functionality.

Comprehensive Software Security from Source to Runtime
RunSafe’s solution minimizes attack surfaces by incorporating memory protection directly into your CI/CD pipelines. This process secures in-house, open-source, and third-party binaries at the build stage, ensuring vulnerabilities are neutralized before deployment. By relocating functions in memory at runtime, our approach prevents attackers from exploiting memory-based vulnerabilities, delivering robust security from source to runtime.
This application security hardening is fully automated, requiring no code changes or system performance impact. It protects compiled code across industries including automotive, rail, aviation, energy, military, and medical devices, providing comprehensive, scalable defense for any software environment.

Comprehensive Application Security Hardening
RunSafe Security’s comprehensive approach ensures that attacks are prevented before they can occur, significantly reducing the need for constant monitoring. Our solutions protect your from development to deployment ensuring robust security.
Easily incorporate RunSafe’s security measures into your existing workflows, streamlining your processes while enhancing protection without relying solely on detection and response. With RunSafe, you can maintain a strong security posture without compromising efficiency or disrupting your development pipeline.
Latest Resources
The Best SBOM Tools for C/C++ Development
Generating an accurate Software Bill of Materials (SBOM) for C/C++ code is notoriously difficult. Unlike ecosystems with centralized package managers, C/C++ projects rely on vendored code, static linking, and manual dependency management, which causes most SBOM tools...
Why Connected Cars Need “Less Data,” Not More: Cybersecurity, Autonomy, and the Future of Connected Cars
Connected vehicles are getting smarter by the model year, but also noisier, more exposed, and harder to secure. Cars include dozens of computers and sensors, plus cameras, microphones, and wireless connections that constantly observe what is happening inside and...
Breaking Down the Top 15 Software Supply Chain Attacks
Software supply chain attacks surged at the end of 2025, with 41 attacks uncovered in October alone. And there was an unmistakable pattern. Attackers stopped trying to breach organizations directly and instead focused on opportunities for widespread impact. Why pick...
Ready to Get Started?
RunSafe strengthens application security hardening by automatically incorporating memory protection during the build process, eliminating vulnerabilities and reinforcing system defenses without disrupting performance or requiring code changes.


