The automotive industry is at a turning point. Cars have become rolling computers, with more than 100 million lines of code powering everything from braking systems to infotainment screens. But as vehicles have evolved into software-defined machines, the security protections around them have not kept pace.
RunSafe Security’s new 2025 Connected Car Cyber Safety & Security Index reveals that consumers are more aware of cybersecurity risks than ever before and they’re ready to make buying decisions based on how automakers respond.
Listen to the Audio Overview
Consumer Awareness Has Outpaced Automaker Action
For years, automotive cybersecurity was treated as a technical issue best left to engineers. Today, it’s become a mainstream consumer concern. In our survey of 2,000 connected car owners across the U.S., the UK, and Germany, 65% of drivers believe remote hacking of a vehicle is possible, yet only 19% feel “very confident” that their car is protected.

That confidence gap is profound. Drivers perceive their vehicles as more vulnerable than other connected devices, such as smartphones, which receive regular security updates. And they’re right to be concerned. Recent years have seen everything from mass remote recalls to exploits that allowed researchers to take control of vehicles from miles away.
Safety, Not Privacy, Drives Concern
One of the most striking findings is that drivers now view connected car security as a matter of life and death. An overwhelming 79% say protecting their physical safety from cyberattacks is more important than safeguarding the personal data inside their cars.
Unlike traditional cybersecurity breaches that expose sensitive data, automotive hacks can directly compromise safety-critical systems like steering, braking, and acceleration. Consumers understand this risk and expect automakers to treat it with the seriousness it deserves.
Software Supply Chain Risks in the Spotlight
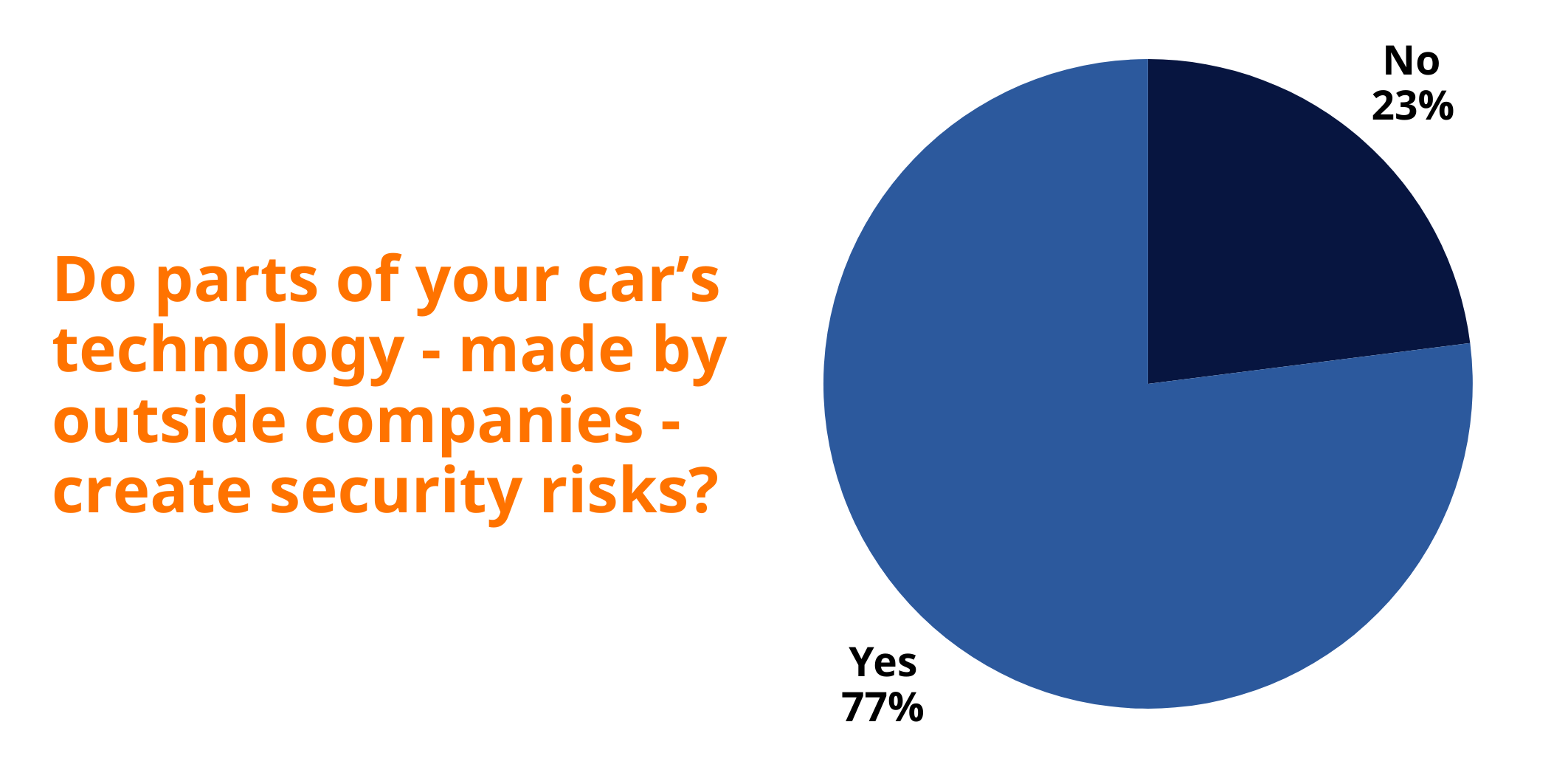
Modern vehicles aren’t built by a single company; they’re the product of a complex ecosystem of suppliers. Our survey found 77% of drivers recognize third-party components as cybersecurity risks, and 83% want transparency about software origins.
This demand for disclosure puts new pressure on automakers. Consumers don’t want vague assurances about safety and security. They want to know what’s inside their vehicles, where it came from, and how it’s being protected.
Automotive Cybersecurity as a Competitive Advantage
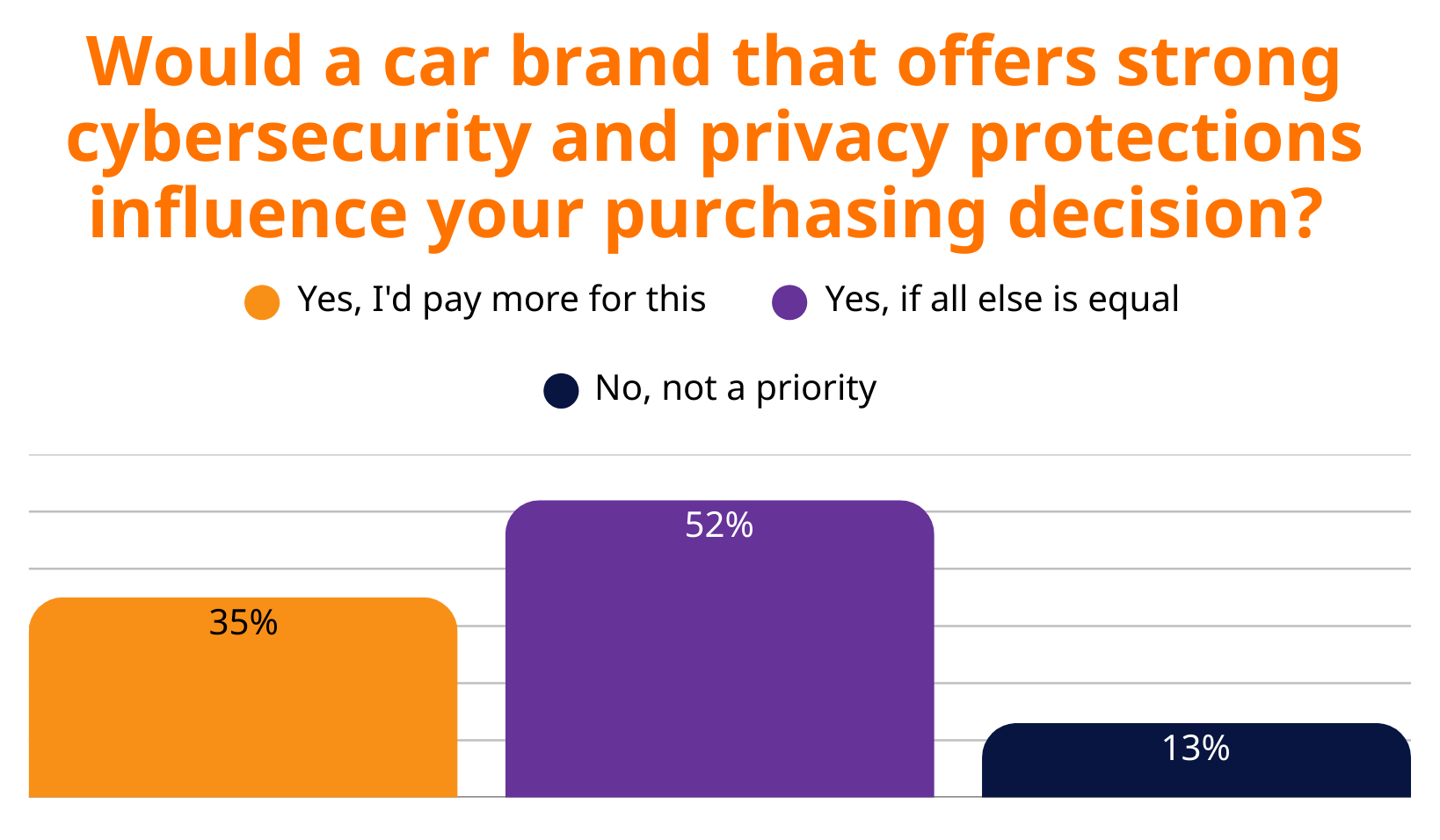
Perhaps the most important finding of all: cybersecurity now has the power to make—or break—a sale. Eighty-seven percent of consumers say strong protections influence their buying decisions, with 35% willing to pay premium prices for enhanced security.
That’s a stunning shift in the way drivers view their cars. Security has moved from a behind-the-scenes technical feature to a frontline differentiator, on par with performance, comfort, and fuel economy.
Automakers that ignore this reality risk losing customers to more security-conscious competitors—or worse, driving them toward older, less profitable vehicles. In fact, 70% of drivers said they would consider buying an older, less connected car just to reduce cyber risk.
Automotive Cybersecurity Is a Defining Market Force
The 2025 Connected Car Cyber Safety & Security Index shows that automotive cybersecurity is a business imperative that directly impacts brand loyalty, market share, and revenue potential.
The message from consumers is clear: build security in, be transparent about software supply chains, and treat cybersecurity as seriously as safety. Those who act now will gain a durable competitive edge.
Download the full 2025 Connected Car Cyber Safety & Security Index to see the complete findings and insights for automakers and suppliers.