Generating an accurate Software Bill of Materials (SBOM) for C/C++ code is notoriously difficult. Unlike ecosystems with centralized package managers, C/C++ projects rely on vendored code, static linking, and manual dependency management, which causes most SBOM tools to miss components or produce incomplete results.
The right tool depends on your build environment, accuracy requirements, and whether you have source access or only compiled binaries. This guide covers 12 of the best SBOM tools that support C/C++ development, along with evaluation criteria and a workflow for generating accurate SBOMs.
Listen to the Audio Overview
Why C/C++ SBOM Generation Is Uniquely Challenging
Several tools support SBOM generation for C/C++ projects, including general-purpose open-source options and specialized tools that integrate directly with the C/C++ build ecosystem. That said, generating accurate SBOMs for C/C++ remains one of the hardest problems in software supply chain security.
The core issue is that C/C++ lacks a centralized package manager. Unlike JavaScript with npm or Python with pip, C/C++ developers typically manage dependencies manually. They copy source files, use git submodules, or compile libraries from source. Most SBOM tools rely on package manifests to identify components, and when those manifests don’t exist, the tools struggle to produce accurate results.
Static linking compounds the problem further. When libraries are compiled directly into an executable, their boundaries disappear entirely. A finished binary might contain dozens of third-party components, but without clear markers, even sophisticated analysis tools miss them.
Build system fragmentation adds yet another layer of complexity:
- Make, CMake, Autotools, Bazel, Yocto: Each handles dependencies differently
- Proprietary build systems: Many embedded teams use custom toolchains with no standard integration points
- Cross-compilation: Embedded targets often require specialized build configurations that generic tools don’t understand
For embedded systems and critical infrastructure, incomplete SBOMs create real risk. Devices running C/C++ code often operate for 10-20 years, and blind spots in vulnerability management persist throughout that entire lifecycle.
What to Look for in an SBOM Tool for C/C++ Projects
Dependency discovery without a package manager
Any tool you evaluate for C/C++ projects has to identify dependencies through build system integration, source analysis, or binary inspection. It cannot rely on manifest files that simply don’t exist in most C/C++ workflows. This capability is the single most important factor to consider.
Build system compatibility
Confirm support for your specific build environment before committing to a tool. Make, CMake, Autotools, Bazel, and Yocto each require different integration approaches. Seamless compatibility reduces friction for engineering teams and improves adoption across your organization.
SBOM format support for SPDX and CycloneDX
SPDX and CycloneDX are the two dominant SBOM standard formats. Regulatory frameworks, including FDA guidance and the EU Cyber Resilience Act (CRA), accept both, though some procurement contracts specify a preference. Your tool ideally outputs both formats.
Vulnerability identification and CVE mapping
Once components are identified, the tool maps them to known vulnerabilities using databases such as the National Vulnerability Database (NVD). Accuracy here depends entirely on correct component identification upstream. If the SBOM misses a component, the vulnerability scan misses it too.
License compliance detection
Open-source license obligations carry legal weight, especially when shipping embedded products. GPL, LGPL, and Apache licenses each have different requirements. Copyleft violations can put intellectual property at risk, so tracking license terms alongside components matters for legal and compliance teams.
Accuracy and reduction of false positives
A high false positive rate wastes engineering time and erodes trust in the tool. Build-time SBOM generation tends to produce fewer false positives than binary analysis alone because it observes what actually gets compiled rather than guessing from the output.
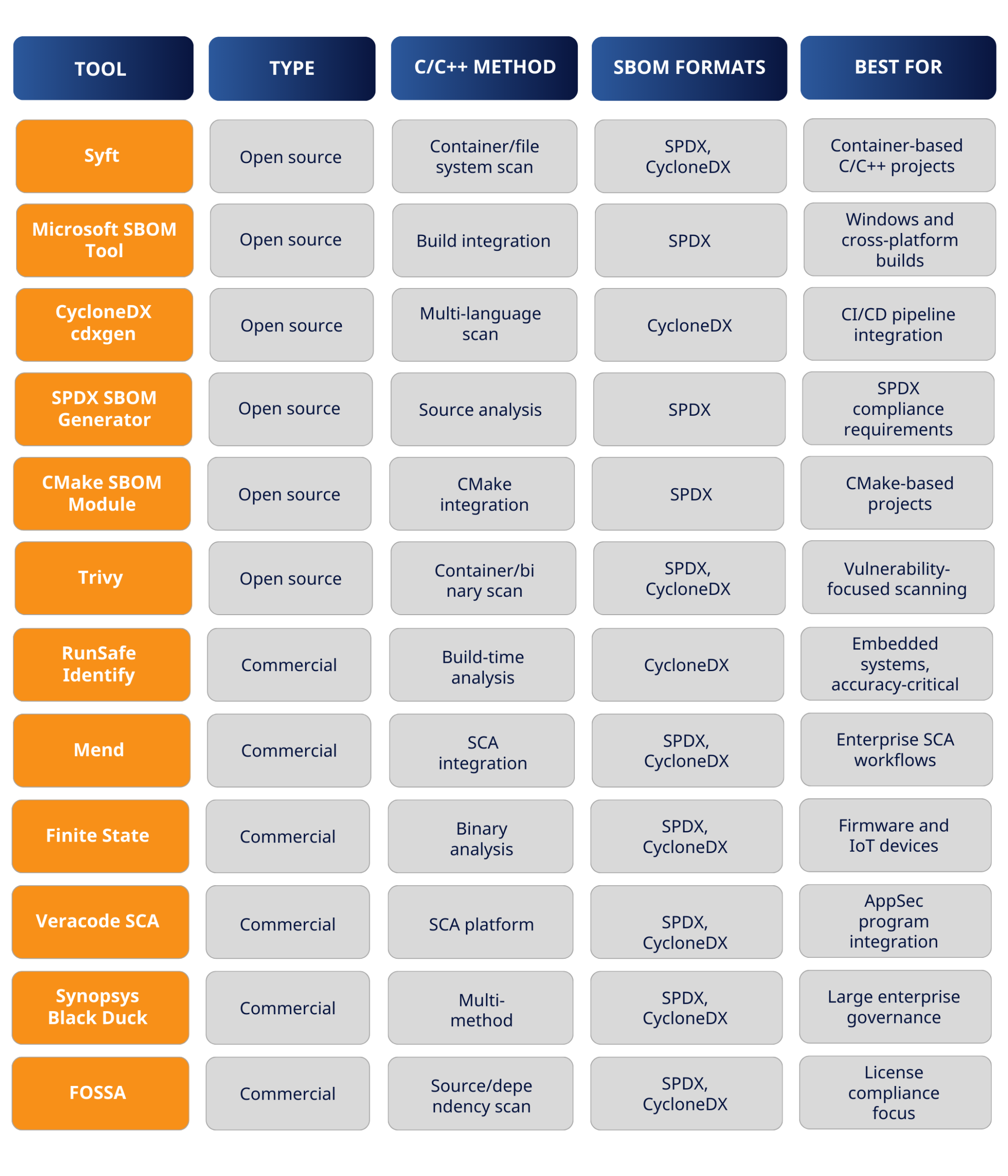
Top 12 SBOM Tools that Support C/C++ Development
Open source SBOM generation tools
Open source tools work well for teams with technical resources to configure and maintain them. They’re free to use, though they often require more hands-on setup for C/C++ projects.
1. Syft by Anchore
Syft is a popular CLI tool for generating SBOMs from container images and filesystems. For C/C++ projects, Syft focuses on detecting OS packages and some binary fingerprinting. It works best when C/C++ code is containerized, since it can identify system-level dependencies within the container image.
2. Microsoft SBOM Tool
Microsoft’s open-source tool integrates with build pipelines to generate SPDX-format SBOMs. It supports multiple ecosystems, though C/C++ projects without package managers require additional configuration. The tool works well in Windows and cross-platform build environments.
3. CycloneDX Generator
OWASP’s official SBOM tool supports many languages, including partial C/C++ support via plugins. Strong CI/CD integration makes it a good choice for automated pipelines. The tool generates SBOMs in CycloneDX format and can be extended for specific build environments.
4. SPDX SBOM Generator
This tool focuses on producing compliant SPDX output. C/C++ support requires additional tooling to identify dependencies before generation, so teams often use it alongside other analysis tools. It’s particularly useful when SPDX format is a hard requirement.
5. CMake SBOM Module
For projects using CMake, this module provides native integration directly into the build system. It captures dependencies declared in CMakeLists.txt. However, it may miss vendored or manually included code that isn’t explicitly declared in the CMake configuration.
6. Trivy
Trivy is primarily a vulnerability scanner that also generates SBOMs. For C/C++ projects, Trivy focuses on OS-level packages in container images rather than application-level dependencies. It’s useful when vulnerability scanning is the primary goal and SBOM generation is secondary.
Commercial SBOM tools for C/C++
Commercial tools typically offer better accuracy, dedicated support, and deeper integration for enterprise and regulated environments. They come with licensing costs but often reduce the configuration burden on engineering teams.
7. RunSafe Identify
RunSafe Identify generates build-time SBOMs specifically designed for embedded systems and C/C++ codebases. By capturing dependencies during compilation, it achieves higher accuracy than post-build analysis. The platform includes vulnerability identification, license compliance, and reachability analysis. It’s particularly suited for teams facing regulatory requirements, like FDA or EU CRA SBOM requirements, as it is built specifically to support embedded software.
8. Mend
Mend (formerly WhiteSource) is an enterprise SCA platform with SBOM generation capabilities. C/C++ support varies by project structure and works best when dependencies are clearly defined. The platform integrates with existing development workflows and provides policy enforcement.
9. Finite State
Finite State specializes in binary analysis for firmware and IoT devices. It’s effective for legacy C/C++ systems where source code access is limited. The platform can analyze compiled binaries to identify embedded components and known vulnerabilities.
10. Veracode SCA
Veracode SCA integrates SBOM generation into a broader application security platform. C/C++ depth depends on project configuration and build system integration. Teams already using Veracode for other security testing can add SBOM generation to their existing workflows.
11. Synopsys Black Duck
Black Duck offers SCA with multiple detection methods and enterprise governance features. Accurate C/C++ results may require significant configuration. The platform is well-suited for large organizations with complex compliance requirements.
12. FOSSA
FOSSA emphasizes license compliance alongside SBOM generation. C/C++ support requires integration with build systems to achieve accurate dependency mapping. The platform is particularly useful when license risk is a primary concern.
How to Choose the Best SBOM Tool for C/C++ Projects
Your selection depends on several factors specific to your environment and requirements:
- Project type: Embedded and firmware projects benefit from tools that handle cross-compilation and RTOS environments; containerized applications can use standard container-scanning tools.
- Source access: Teams with full source and build access benefit most from build-time SBOM generation; legacy binary-only systems require binary analysis tools.
- Regulatory requirements: FDA, EU CRA, and federal mandates may specify SBOM formats and depth requirements.
- Integration fit: Consider how the tool fits into existing CI/CD pipelines and vulnerability management workflows.
- Accuracy tolerance: Critical infrastructure and safety-critical systems demand lower false positive and negative rates than general-purpose software.
How to Generate an Accurate SBOM for C/C++ Applications
Step 1. Map your build system and dependencies
Start by documenting all third-party libraries, their sources (vendored, submodules, system packages), and how they’re linked. This groundwork determines which tool approach will work for your environment. Without this mapping, you’re guessing at which tool will produce accurate results.
Step 2. Select the right SBOM generation tool
Match tool capabilities to your build environment and accuracy requirements based on the evaluation criteria above. Consider running a proof-of-concept with your actual codebase before committing to a tool.
Step 3. Integrate SBOM generation into your build pipeline
Configure the tool to run during or immediately after the build process. For build-time tools, this means hooking into Make, CMake, or your build system’s execution. The goal is to capture dependencies at the moment they’re resolved.
Step 4. Validate SBOM completeness and accuracy
Compare the generated SBOM against known dependencies. Check for missing components, incorrect versions, and phantom entries. Iterate on the configuration to improve results. This validation step often reveals gaps that require tool adjustments.
Step 5. Automate SBOM generation for every build
Once validated, automate SBOM generation for every build to maintain a current inventory as code changes. Store SBOMs alongside release artifacts for traceability. This automation ensures your SBOM stays current without manual effort.
Gain Visibility into Your C/C++ Codebases
Accurate SBOM generation for C/C++ requires tools designed for the language’s unique challenges. Build-time approaches offer the highest accuracy for embedded and critical systems where incomplete visibility creates operational risk.
Schedule a consultation to see how build-time SBOM generation provides accuracy and visibility into your embedded software components.
Frequently Asked Questions About SBOM Tools for C/C++
Build-time SBOMs capture dependencies as they’re compiled and linked, providing higher accuracy. Binary analysis reverse-engineers finished executables and may miss components due to stripped symbols or static linking. The tradeoff is that build-time generation requires access to the build environment, while binary analysis can work with compiled artifacts alone.
Can SBOM tools detect statically linked C/C++ libraries?
Most binary analysis tools struggle with statically linked libraries because the code merges into the final executable without clear boundaries. Build-time SBOM generation captures static dependencies during the linking phase before this information is lost.
How do teams generate an SBOM for legacy C/C++ code without source access?
Binary analysis tools like Finite State or Trivy can inspect compiled executables to identify embedded components. Accuracy is lower than source-based methods, so teams often validate results against any available documentation or known component lists.
Which SBOM format is required for FDA or EU CRA compliance?
Both SPDX and CycloneDX are accepted by major regulatory frameworks, including FDA guidance and the EU Cyber Resilience Act. Check specific requirements for your industry, as some procurement contracts may specify a preferred format.
How often do teams regenerate their C/C++ SBOM?
Generating a new SBOM with every build or release ensures the inventory reflects current code. Automated SBOM generation integrated into CI/CD pipelines makes this sustainable without manual effort.
Do SBOM tools work with embedded Linux and RTOS projects?
Some SBOM tools support Yocto, Buildroot, and other embedded Linux build systems. RTOS support varies significantly across tools. Verify tool compatibility with your specific toolchain and target platform before committing. RunSafe Security’s SBOM tool supports Linux, VxWorks, Yocto, QNX, Bare Metal, Free RTOS, Green Hills, and Windows. See a list of supported OSes here.