Recently, nation-state actors, like the Volt Typhoon campaign, have demonstrated the potential real-world impact of memory safety vulnerabilities in the software used to run critical infrastructure.
It’s for this reason, among other national security, economic, and public health concerns, that the Cybersecurity and Infrastructure Security Agency (CISA) has made memory safety a key focus of its Secure by Design initiatives.
Now, CISA is urging software manufacturers to publish a memory safety roadmap by January 1, 2026, outlining how they will eliminate memory safety vulnerabilities in code, either by using memory safe languages or implementing hardware capabilities that prevent memory safety vulnerabilities.
Though manufacturers are on the hook for the security of their products, the responsibility doesn’t fall solely on the shoulders of the manufacturers. Buyers of software in the OT sector also have an equally important role to play in addressing memory safety to build the resilience of their mission-critical OT systems against attack.

“The roadmap to memory safety is a great starting point for asset owners to talk to their suppliers, saying this is a big concern of mine, especially for my OT software,” said Joseph M. Saunders, Founder and CEO of RunSafe Security. “Then, what we’re looking for from product manufacturers is that they have a mature process to assess how to achieve memory safety.”
Why Memory Safety Should Be on Your Radar
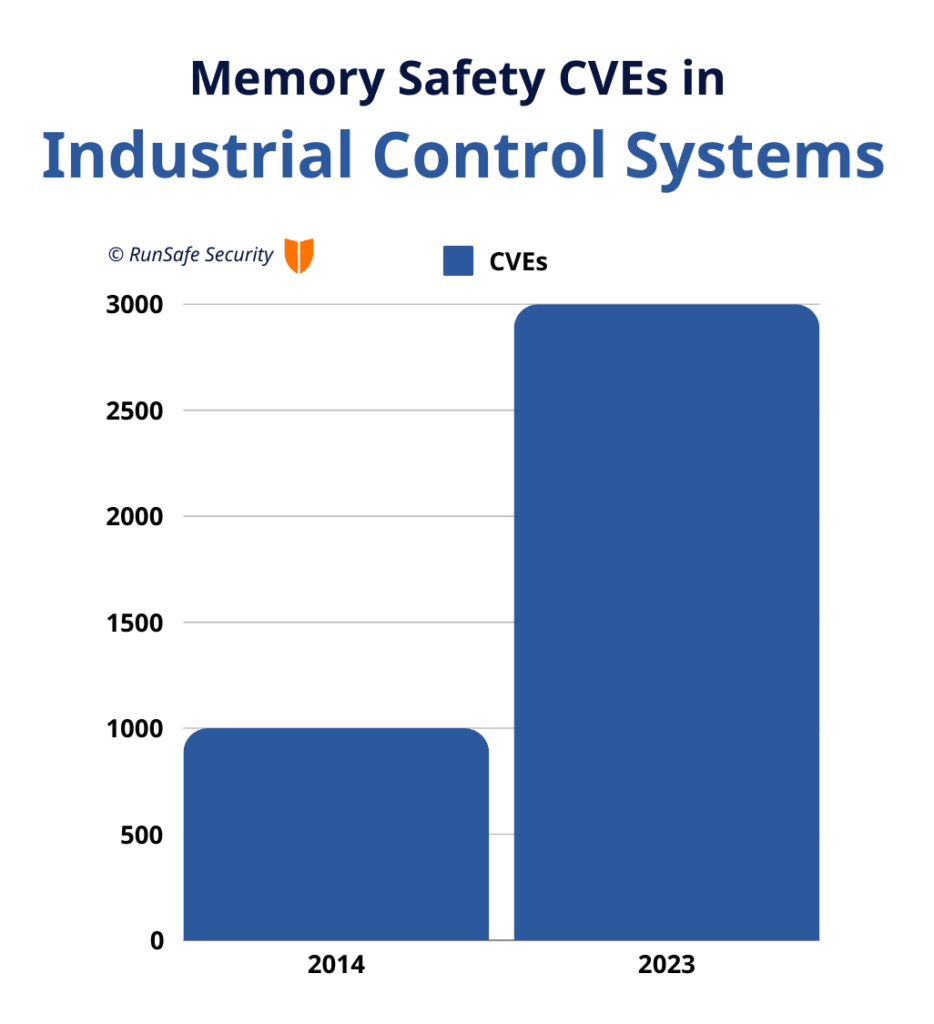
Why all the fuss about memory safety, and why now? Memory safety vulnerabilities consistently rank among the most dangerous software weaknesses, and they are alarmingly common. Within industrial control systems, memory safety vulnerabilities have been steadily rising, growing from less than 1,000 CVEs in 2014 to nearing 3,000 in 2023 alone.
In one example, programmable logic controllers were found vulnerable to memory corruption flaws that could enable remote code execution. In the OT world, where systems control critical industrial processes, such vulnerabilities aren’t just security risks — they’re potential catastrophes waiting to happen.
Building a Memory Safety Strategy: Collaboration Between OT Software Manufacturers and Buyers Is Needed
CISA has set a clear deadline: January 1, 2026. With this date in mind, OT software manufacturers and buyers can begin to have important conversations about addressing memory safety, both for existing products written in memory-unsafe languages and for new products to be released down the line.
What should be on the agenda for discussion when building and evaluating a memory safety roadmap? Here are four key areas to look at.
1. Vulnerability Assessments
Start with a comprehensive Software Bill of Materials (SBOM) to identify and prioritize memory-based vulnerabilities in OT software. Think of it as a detailed inventory that helps you:
- Identify existing vulnerabilities
- Map your software supply chain
- Pinpoint products most at risk from memory-based vulnerabilities
2. Smart Remediation Planning
Once vulnerabilities are identified, manufacturers should take next steps to eliminate them. OT software buyers can discuss with manufacturers about remediation options like:
- Prioritizing addressing systems with high exposure and potential impact
- Evaluating options for rewriting legacy code in memory-safe languages, like Rust
- Considering proactive solutions such as Load-time Function Randomization (LFR) for existing systems when code rewrites are not practical
3. Future-Proofing Your Products
Software buyers should discuss with their suppliers how they are incorporating memory safety into their product lifecycle planning.
Look ahead by:
- Integrating memory safety into your product roadmap
- Taking advantage of major architectural changes to implement memory-safe languages
- Deploying software memory protection for existing code
4. Building Strong Partnerships
A memory safety roadmap is a great opportunity for software manufacturers and buyers to open up conversations about memory safety and collaborate to find a path forward. When considering working with a supplier, evaluate their willingness to
- Establish regular communication channels
- Transparently track progress
- Demonstrate a shared commitment to security goals
Moving Forward with CISA’s Memory Safety Guidance
By working together, software buyers and manufacturers can not only meet CISA’s memory safety mandate but also build more resilient OT systems.
“All asset owners should do a study with their suppliers to understand the extent to which they are exposed to memory safety vulnerabilities,” Saunders said.
From there, software manufacturers can build a roadmap to tackle the memory safety challenge once and for all.
Learn more about how RunSafe Security protects critical infrastructure and OT systems from memory-based vulnerabilities.





