Cyber defense for embedded systems is justified using a total cost of ownership approach
I admit it. Cyber defense is not eye catching, especially effective cyber defense, which is automated and transparent to the operator. An air platform’s range and a control system’s user interface are given the spotlight. However, cyber defense has financial benefits, offers product differentiation, and smooths out the patching processes both for product manufacturers and their customers. The importance of cyber defense will go up over time, no doubt. Until then, as cyber defense champions, we must quantify economic benefits to justify faster adoption.
Here is a total cost of ownership (TCO) we completed with an embedded product manufacturer. This analysis is a joint effort between RunSafe and the product manufacturer. They provided labor costs, patch frequency, organizational constructs, and more. We know the impact our cyber defense has based on the historic prevalence of memory corruption vulnerabilities in compiled code like theirs. Collecting the data is the hard part. The TCO calculations are purposely straightforward, centering on reduction of engineer labor, which can then be allocated to more lucrative pursuits, like new product features.
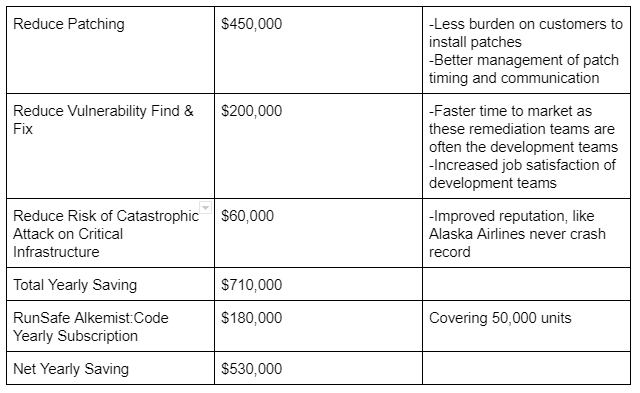
Bottom line: Implementing our cyber defense solution saves $530K net per year in hard costs plus additional benefits, as summarized below. Reduced patching is the largest cost saving.
Scanning & Patching Leave a Gap in Security
It’s clear additional cyber defense is required. Scanning and patching are not enough. A recent study by North Carolina State University shows that for Linux operating system software over a 10-year period, only 2.5% of memory vulnerabilities were identified in vulnerability scanning tools. Which shows us that scanning, a widely adopted practice, leaves one vulnerable.
Similarly, multiple studies say companies and users generally aren’t patching on time due to lack of knowledge, the effort to coordinate change, the process slowing progress, fear of breaking current setup, and other barriers. At its best, patching is reactive. More often, costs and other barriers mean patching is delayed, if done at all.
Given these issues, one could conclude that additional cyber defense, such as RunSafe’s Alkemist, that closes the gap left by patching and scanning would be widely adopted. However, we know that’s not the case. Decision makers need evidence of economic benefits before taking the next step.
Scanning & Patching Are Expensive
Scanning and patching are major cost drivers in the development and maintenance of products. That’s the aspect cyber defense proposals can attack. Effort is put into code scanning/review, penetration testing, subsequent remediation, and then coordinated release of patches to customers. These issues spawn lengthy retesting cycles and gobble up R&D resources that would otherwise be able to work on new features and products. For this TCO analysis, the manufacturer allocated $75K per patch to one product for just engineering labor. They’re also patching more than once a month.
From a risk management perspective, the application of a large number of patches (or bug remediations) implies that further problems, complexities, and instability could be introduced to a system, therefore increasing the likelihood of subsequent problems or failure. It should also be acknowledged that in some cases, in order to meet tight release deadlines and budgets, security bugs are simply accepted as a tolerable risk to be remediated at a later date, if ever.
Both TCO and risk management best practices dictate that fewer patches are desirable.
Automated Cyber Defense to Reduce Patching and Remediation Costs
Our joint analysis shows TCO is reduced by adding Alkemist:Code to this manufacturer’s process. The savings above derive from smoothing out labor effort on R&D items and patching support. Many of the vulnerabilities do not need to be acted on immediately, reducing the number of updates and time spent researching fixes. In this example, current yearly patching is $1.2M ($75K per patch, 16 per year). Alkemist:Code reduces the number of patches to 10, producing a savings of $450K. This ~40% reduction in patches is the result of Alkemist:Code mitigating memory corruption vulnerabilities before they are identified and thus avoiding the need for a seperate patch cycle.
In addition, reduction of patches means the additional benefit of controlling patch timing and better communication. For a product manufacturer, there is a delicate balance between announcing vulnerabilities and managing expectations on the time required to issue a patch for the vulnerability identified. When done well, security can be a differentiator to drive sales adoption. When done poorly, makers are scrambling to research a vulnerability, consuming scarce resources that could be applied to new product features.
Other benefits include improved customer relationships (no one likes patching) and improved engineering team experience (no one likes chasing down someone else’s vulnerability). Some of these soft benefits could be quantified as well, but the math gets more complicated and that reduces the impact.
Armed with this TCO analysis, the manufacturer adopts a new approach to cyber defense to ensure their products keep operating through attacks, using Alkemist:Code’s sophisticated automation and mitigation, rather than brute force find and fix.
RunSafe’s design tenets are: do no harm to the original software, be scalable, and be widely applicable. RunSafe’s approach means embedded systems are protected against both known and unknown, yet-to-be-exploited vulnerabilities. The benefit is mitigation of memory corruption vulnerabilities—those ubiquitous vulnerabilities comprising 40-70% of identified vulnerabilities, depending on the code stack. Mitigation happens automatically at run-time, ensuring the smooth operation of protected systems.
Interested in seeing RunSafe’s Alkemist technology in action? Start a free trial today.