Stop Hackers from Exploiting Memory-Related Vulnerabilities.
Use RunSafe Code – patented Moving Target Defense (MTD) techniques – to neutralize memory-related exploits.
![]()
Memory corruption vulnerabilities
(buffer, stack, and heap)
![]()
Return/jump oriented
programming(ROP/JOP) attacks
![]()
Launching and scaling
zero-day attacks
How It Works
RunSafe Code™ hardens software by relocating where functions load into memory uniquely for every software load for each instance deployed. This software diversity denies attackers the ability to exploit memory-based weaknesses in software, which comprise nearly 70% of vulnerabilities in compiled code. With no new software and no change in the lines of code, there is no change in system performance and no change in functionality.
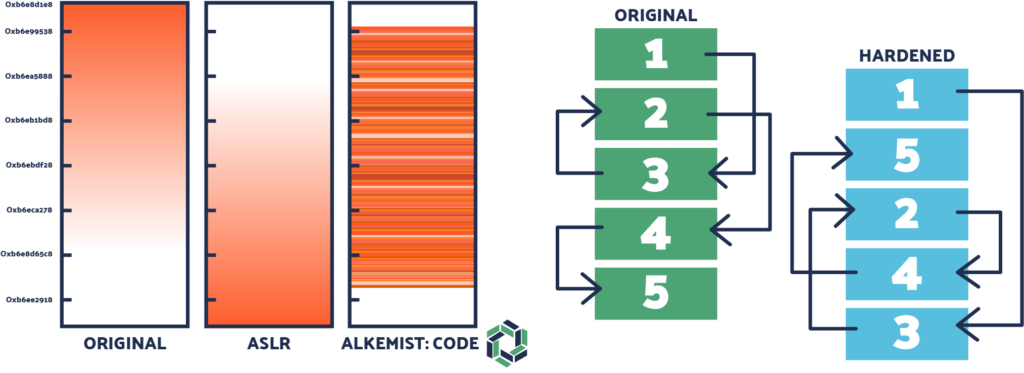
Based on a portfolio of 14 patented Moving Target Defense (MTD) related techniques, the RunSafe lightweight hardening process incurs no performance overhead! With RunSafe Code, there is no way for hackers to know distances between functions or create exploits that take advantage of knowing how functions are laid out, let alone launch and scale attacks.

Address 20% of NIST 800-53 Controls with RunSafe Code
TRY FOR FREE(No contract / no credit card needed)