Zero-day vulnerabilities are the bogeymen of cybersecurity. They lurk unseen in our systems until the moment of exploitation, leaving defenders with no time to prepare.
Our goal at RunSafe is to give defenders a leg up against attackers, so we wondered: What if we could quantify this seemingly unquantifiable risk? What if we could take meaningful action to implement zero-day protection for systems before vulnerabilities are even discovered?
To dig into these questions, we partnered with Ulf Kargén, Assistant Professor at Linköping University, who developed the CReASE (Code Reuse Attack Surface Estimation) tool, which is part of RunSafe Identify.
Quantifying the Unquantifiable: A New Approach to Zero-Day Risk
VulnCheck, in their “2024 Trends in Vulnerability Exploitation” report, found that 23.6% of all actively exploited vulnerabilities in 2024 were zero-day flaws. We’re seeing nation-state actors like Volt Typhoon and Salt Typhoon specifically target these unknown vulnerabilities to achieve their objectives, as noted in research from Google Threat Intelligence Group, which tracked 75 zero-day vulnerabilities exploited in the wild in 2024.
Most of the industry’s response to zero days has been trying to detect and prevent threats by looking for indicators of attack, suspicious behavior, and patterns that might tip us off. But attackers have gotten really good at hiding and masking their activity. What’s been left wide open is the underlying risks in software itself. Instead of securing the foundation, we’ve built bigger walls around our systems.
That might work in a data center where systems live behind firewalls and racks of gear. But in the world of IoT and embedded devices, there are no walls. These systems are deployed far from the protection of the network where they are alone, exposed, and vulnerable. They need to be self-reliant. They need to be like samurai—able to defend themselves without backup.
Because of this, we saw the need for a method to quantify the risk of zero days and a way to make devices intrinsically more robust against exploitation, regardless of what vulnerabilities might exist within them. If you can quantify risk with real technical rigor, you can make smart decisions to reduce your attack surface and make a compelling argument to leadership on where to focus resources.
Return-Oriented Programming: Understanding the Threat
Modern cyberattacks frequently use a technique called Return-Oriented Programming (ROP). When traditional code injection attacks became difficult due to improved security measures, attackers evolved to use “code reuse” attacks instead.
Modern exploits repurpose a program’s own code, using existing code snippets (called “gadgets”) within a program and chaining them together to create malicious functionality. The program’s own code is weaponized against itself.
This insight gives us a way to measure memory-based zero-day risk specifically. While it’s impossible to predict all potential vulnerabilities in code, we can analyze whether useful ROP chains exist in a binary that could lead to the successful exploitation of a vulnerability.
Quantifying Zero-Day Risk with CReASE
We worked alongside researcher Ulf Kargén at Linköping University who developed the Code Reuse Attack Surface Estimation (CReASE) tool to quantify previously unmeasurable risk. You can listen to Ulf discuss the tool and how it works in this webinar.
CReASE scans binaries to identify potential ROP gadgets and determines whether they could be chained together to perform dangerous system calls. It doesn’t try to predict where specific vulnerabilities might exist but instead analyzes whether the code structure would allow successful exploitation if a vulnerability were discovered.
It answers the question: Are any useful ROP chains available to an attacker?
Unlike existing tools that focus on guaranteeing working exploit chains (often sacrificing scalability or completeness), CReASE uses novel data flow analysis to achieve both scalability and completeness comparable to a human attacker.
The result is a risk scoring system that quantifies the probability that the next memory-based zero-day vulnerability could be exploited to achieve specific dangerous outcomes like remote code execution, file system manipulation, or privilege escalation.
The CReASE tool is found within RunSafe Identify, and analyzes your exposure to CVEs and memory-based zero days as well as total risk reduction with RunSafe Protect applied.
The Memory Safety Challenge
To understand why this approach is so powerful, we need to recognize two critical facts:
- 70% of vulnerabilities in compiled code are memory safety vulnerabilities
- 75% of vulnerabilities used in zero-day exploits are also memory safety vulnerabilities
These numbers tell us that memory safety vulnerabilities constitute a significant risk in our codebases. When a memory vulnerability is exploited, attackers can execute arbitrary code, take control of devices, crash systems, exfiltrate data, or deploy ransomware.
By focusing our risk quantification and mitigation efforts on memory-based vulnerabilities specifically, we’re addressing a common and dangerous attack vector for zero-day exploits.
Memory Randomization: Making Zero-Day Vulnerabilities Inert
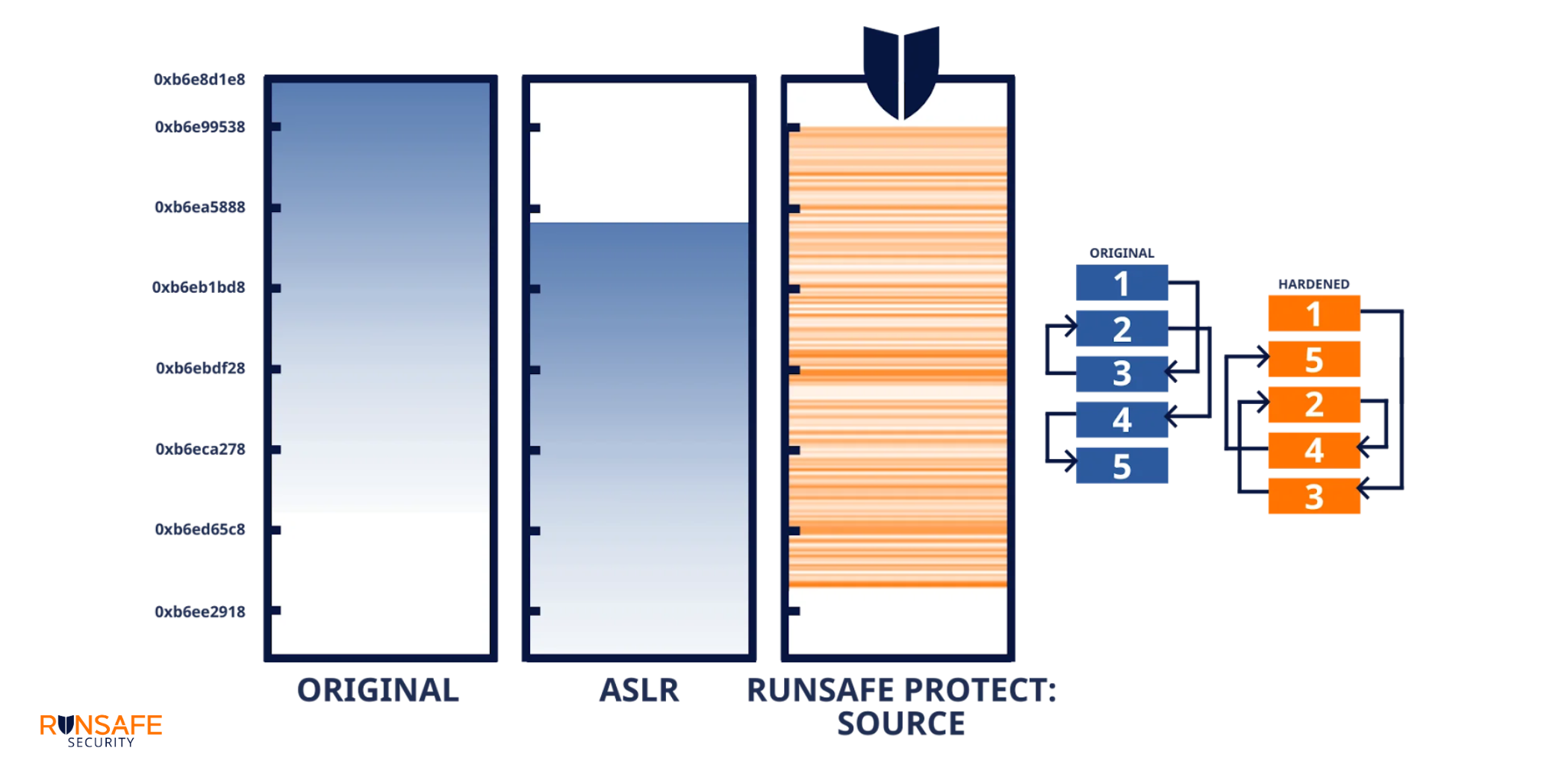
Once we quantify the risk, what can be done about it? Traditional memory protection like Address Space Layout Randomization (ASLR) provides some security by randomizing where blocks of code are loaded in memory. However, ASLR still loads functions contiguously, making it vulnerable to information leak attacks.
RunSafe’s approach takes randomization to the function level. Instead of randomizing where the entire binary loads, we randomize each function independently. In a typical binary with 280 functions, this creates 280 factorial possible memory layouts — more than 10^400 combinations.
Even if a memory-based zero-day vulnerability exists, with RunSafe’s Load-time Function Randomization (LFR), attackers can’t reliably construct a working ROP chain because they can’t predict where the necessary gadgets will be located. We’ve effectively made the vulnerability inert.
Taking Action: Zero-Day Vulnerability Protection
The most effective approach to memory-based zero-day risk combines analysis and protection:
- Analyze your binaries to understand your current risk profile
- Apply function-level randomization to neutralize potential exploits
- Measure the risk reduction to quantify your improved security posture
Our customers typically see a risk reduction that changes the odds from “the next zero-day can compromise the system” to “maybe one in the next 10,000 zero-days might succeed.” That’s a dramatic improvement in security posture.
While no solution can eliminate all types of zero-day vulnerabilities, addressing memory-based vulnerabilities targets the most common and dangerous attack vector. In a world where zero-days will always exist, making them ineffective is the next best thing to eliminating them entirely.
Interested in seeing how much you could reduce your risk by stopping the exploit of memory-based vulnerabilities? Get in touch with our team, who can help you get started.