RunSafe Alkemist is a cybersecurity solution built to defeat an entire class of cyber attacks. It seamlessly integrates into software build toolchains to eliminate the threat of memory-based vulnerabilities. Through RunSafe’s unique User Plugin, Jfrog users can now automatically apply Alkemist protections directly to artifacts flowing through Artifactory repositories. With JFrog being the Universal DevOps technology leader known for enabling liquid software via continuous update flows, Alkemist’s seamless security technology is a perfect fit.
Given JFrog customers are focused on continuous, free-flowing development and deployment, they need a way to harden software binaries without slowing down developers or changing workflows.
The partnership with JFrog enables JFrog Artifactory users to supercharge their binary protections through a simple Alkemist plugin deployed within their Artifactory repositories enabling instant protection for selected binaries.
As compiled binaries are dropped into Artifactory, Alkemist protections are automatically applied to each targeted artifact, thus hardening 3rd party libraries and shared objects from cyber-attack.
Alkemist is the only offering to automatically harden software binaries with memory protections without changing functionality, performance, or overhead. Customers’ deployment cycles are enhanced with binary diversity offering proactive protection from a common attack method.
What is JFrog?
JFrog is on a mission to enable continuous updates through liquid software, empowering developers to code high-quality applications that securely flow to end-users with zero downtime. JFrog is the creator of Artifactory, the heart of the end-to-end Universal DevOps platform for automating, managing, securing, distributing, and monitoring all types of technologies. JFrog products are available as open-source, on-premise, and on the cloud on AWS, Microsoft Azure, and Google Cloud. As a leading universal, highly available enterprise DevOps solution, the JFrog platform empowers customers with trusted and expedited software releases from code-to-production. JFrog is trusted by more than 5,600 customers, and top global brands depend on JFrog to manage their binaries for their mission-critical applications. JFrog is privately held with offices across North America, Europe, and Asia. Learn more at jfrog.com.
“We’re excited to partner with RunSafe so our customers now have the option to automatically reduce attack surfaces and enable secure continuous deployments,” said Casey O’Mara, head of WW business development, JFrog. “With this integration, our users have the ability to deploy the Alkemist plugin to instantly start protecting native binaries and containers.”
What are the Benefits of Applying Alkemist Protections Directly to Artifacts?
For DevOps Managers:
- Add security without developer friction
- Instantly harden all software binaries
- Deploy plugin in minutes
For JFrog Artifactory Users:
- Protect your binaries from cyber attack
- Dramatically reduce attack surfaces by 60-70%
- Enable continuous delivery without developer friction
How Does Alkemist Work?
Alkemist’s patented protections are applied directly to compiled binaries and introduce randomization in how programs load in memory without changing program functionality. This eliminates the determinism attackers require to exploit all memory-based vulnerabilities by breaking the kill chain. Once these protections are applied, a binary‘s memory layout is unique, immunizing the software from memory-based attacks. The Alkemist JFrog plugin changes hacker economics by taking in a single software binary and creates multiple versions that are immunized from attack, thus removing the risk of malware proliferation.
Originally born out of a research project for the Advanced Research Projects Agency of the Department of Defense (DARPA), Alkemist is the only automated cyberhardening tool to protect open source, in-house developed code, and third-party binaries while leaving each system functionally identical, but logically unique.
Click to learn more about RunSafe’s Alkemist technology.
How Does Alkemist Work with JFrog Artifactory?
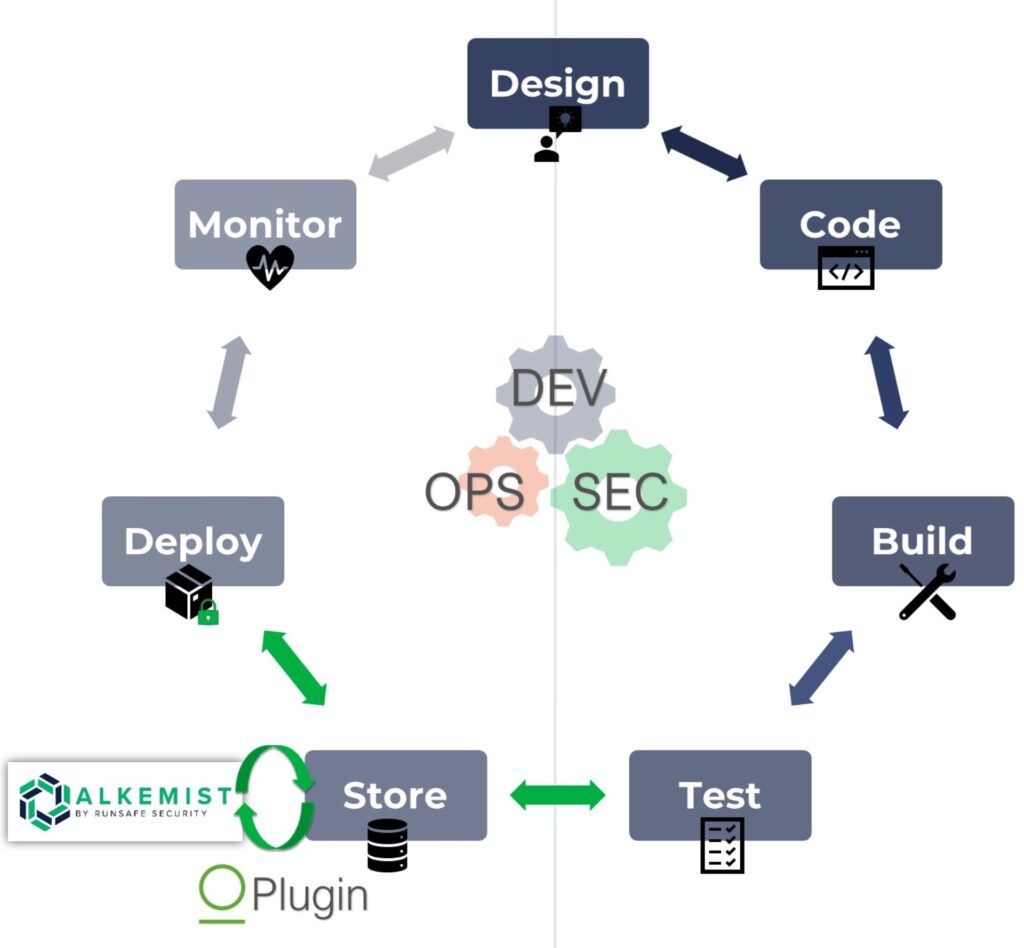
RunSafe has developed a User Plugin enabling Artifactory customers to apply Alkemist protections directly to software binaries flowing into and out of their repos. This highly configurable solution allows users to build a library of protected artifacts without disrupting the normal deployment processes already in place. There is no change to your pipeline beyond insertion of the plugin. By dropping the Alkemist User Plugin for Artifactory into a CI/CD or DevSecOps pipeline, a unique, but functionally equivalent, binary can be deployed to each target system in an automated fashion.
Process Flow
- No change or additional overhead to standard DevSecOps or CI/CD process
- Design, Build, Test, Store, and Deploy your code as normal
- Integrate automated binary hardening in 3 steps:
- Install Artifactory Alkemist plugin
- Install Alkemist images
- Configure plugin and connect Artifactory user plugin and Alkemist images on the same network
- Plugin detects files on push to repository and begins transforms, which are then stored back in Artifactory
- Plugin detects download request and delivers unique hardened binary from repository
Resources for JFrog Users and DevOps Managers
RunSafe Alkmsit and Jfrog Artifactory Overview
Artifactory Plugin Overview Video
Visit the Alkemist Self Service Portal for Demos and Deployment Guides.