Modern software is facing major cybersecurity challenges, with memory safety vulnerabilities being one of the biggest risks. Even with billions invested in advanced security tools, attacks targeting memory vulnerabilities are still common. Studies show that 70% of vulnerabilities in compiled code are memory safety vulnerabilities.
Load-time Function Randomization (LFR), a type of runtime exploit prevention, defends software from memory-based exploits, providing much-needed protection for embedded software deployed across critical infrastructure.
How Does Load-time Function Randomization (LFR) Work?
Load-time Function Randomization (LFR) is a cutting-edge runtime application self-protection (RASP) technique specifically designed to counter memory-based exploits, which remain a persistent threat in modern software systems. By dynamically altering the memory layout of an application during its load time, LFR introduces a powerful layer of unpredictability that disrupts the strategies employed by attackers.
One of the core mechanisms of LFR is function relocation. When an application is loaded into memory, LFR systematically relocates its functions, ensuring that every runtime instance of the application features a unique memory layout. This process means that attackers cannot rely on static memory addresses to predict where specific functions are located. Instead, each execution becomes a fresh puzzle, making it nearly impossible for malicious actors to target the application with precision.
LFR also provides immunity to code exploits, particularly memory-based attacks such as buffer overflows and Return-Oriented Programming (ROP). These attacks depend on the ability to predict or manipulate the memory layout of an application. By introducing countless permutations through randomization, LFR undermines these exploit techniques, rendering them largely ineffective. This innovation raises the bar significantly for attackers, as they would need to account for an exponentially larger range of possibilities, making exploitation infeasible in most practical scenarios.
Importantly, LFR achieves all of this while ensuring the preservation of code logic. The underlying functionality and logic of the application remains unchanged, allowing developers to implement LFR without rewriting or reconfiguring their existing codebases. This seamless integration makes LFR a versatile and developer-friendly solution, offering protection without disrupting established workflows. As a result, LFR not only strengthens application defenses but also empowers development teams to focus on innovation rather than constantly reacting to emerging threats.
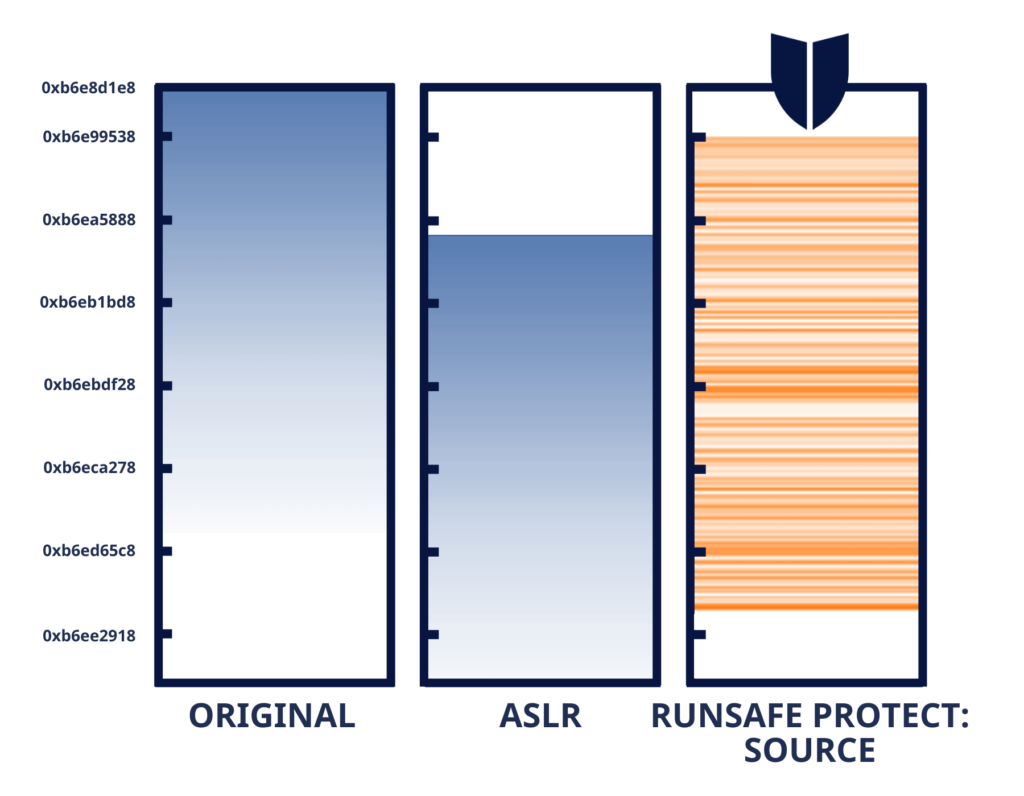
What Is ASLR and How Does LFR Differ?
Address Space Layout Randomization (ASLR) has been a key memory safety measure for over two decades. However, ASLR shifts entire programs or libraries as single units, leaving vulnerabilities within those layouts exploitable. One leaked memory detail can compromise the entire system.
LFR takes ASLR to the next level by offering granular protection. Instead of moving entire programs, it randomizes individual functions, creating far greater entropy and making memory corruption exploits exponentially harder to execute.
Applications of Load-time Function Randomization
The versatility of LFR enables its application across a broad range of industries and systems.
Proprietary Software Protection
Organizations using C/C++ or proprietary code can protect sensitive systems from memory exploits, ensuring both performance and security remain intact.
Embedded Systems Security
Use cases include aerospace and defense, automotive, and medical devices with embedded software. By providing consistent memory protection, LFR reduces the need for constant patches and resource-intensive updates.
Application Security Hardening
DevSecOps pipelines can leverage LFR during build processes to safeguard applications from source to runtime, leading to fewer reactive fixes and enhanced customer trust.
Benefits of RunSafe’s Implementation of LFR
RunSafe Security’s solution, RunSafe Protect, integrates LFR to deliver unmatched memory protection across software systems.
1. Comprehensive Security
LFR eliminates vulnerabilities related to memory corruption, such as buffer overflows and use-after-free attacks, protecting organizations from the most critical attack vectors.
2. No Performance Impacts
Unlike some security approaches that come at the cost of system speed or efficiency, LFR achieves protection with very little overhead. This makes RunSafe Protect an ideal solution for resource-constrained environments.
3. Developer-Friendly Deployment
LFR integrates seamlessly into CI/CD pipelines without requiring changes to existing frameworks or development workflows. Its ease of use ensures minimal disruption for teams.
4. Broad Compatibility
LFR is effective across a range of operating systems, architectures, and industries. RunSafe Protect supports Linux, VxWorks, ARM, and Intel environments, among others.
Learn more about RunSafe Protect in our deep dive into the technology that powers it. Get the white paper: Tech Deep Dive: RunSafe Security’s Protect Solution.
Why LFR Is Essential for Software Security
Proactive defense mechanisms like LFR are no longer optional in addressing the most prevalent software weaknesses. With advanced threat actors refining their exploitation techniques and targeting critical systems, defending against memory-based vulnerabilities quickly and efficiently is a must.
By introducing LFR, organizations can harden their systems against adversaries while preserving efficiency and reliability.
Want to explore how RunSafe Protect can elevate your software security? Request a consultation to learn more about deploying LFR.