How It Works
Thwarting How Attackers Operate
Memory corruption attacks try to trick a software program into running attacker-provided code, instead of programmer-written code. For this to work, the attacker must find vulnerabilities in the software binary code that allow the injection of code and/or the redirection of execution. Alkemist transforms open source, in-house developed code, and third-party software binaries so that attackers can’t calculate in advance how to successfully execute their code.
What Alkemist Does
RunSafe Security’s Alkemist hardens software against memory corruption errors and buffer overflow exploits – the techniques attackers typically use to gain control of embedded systems and devices. Alkemist’s remotely deployable, automatic cyberhardening transformation tool utilizes Runtime Application Self-Protection (RASP) and Moving Target Defense (MTD) techniques.
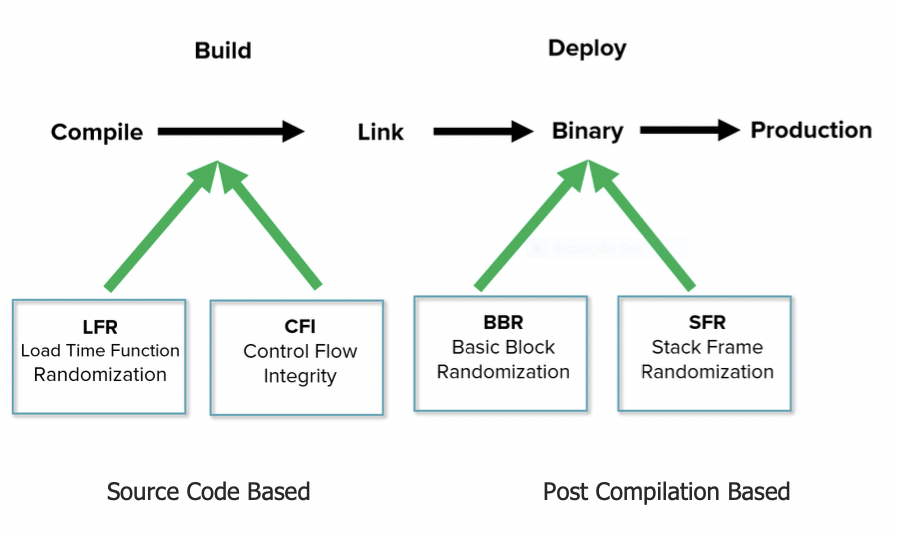
At build time, these methods are used:
- Load-time Function Randomization randomizes function locations every time the binary loads, obscuring the information needed for an attack. So, the same file can be signed and deployed to hundreds of millions of devices, while keeping function-location information away from the attacker.
At deploy time, these methods are used:
- Block-level Binary Randomization randomizes memory, basic block functions, and access to third-party libraries. This reordering means that malware is denied the deterministic logical structure it requires to propagate and take control of code, while maintaining the identical functions as features of the initial software image.
- Stack Frame Randomization creates stack-level entropy by randomizing the buffer set aside for local variables when functions are instantiated on the stack. This entropy deprives an attacker of the information needed to craft a payload that weaponizes a stack overflow vulnerability.
By precluding an exploit from spreading across multiple devices and networks, Alkemist disrupts hacker economics and shifts the odds in favor of the defender.
Render threats inert by eliminating attack vectors and significantly reducing vulnerabilities.